The cybercriminal who stole more than 200 bitcoin (BTC) from Luke Dashjr, the creator of Bitcoin Core, carried out a series of transactions in order to conceal the ultimate destination of the stolen assets. This individual demonstrates a high level of caution and a significant amount of understanding about programming and Bitcoin based on their actions.
According to the data that was made public by an automatic tool that is included in the OXT browser and enables for the monitoring of transactions, a sequence of roughly seventy operations were carried out, each of which included dozens of additional transactions.
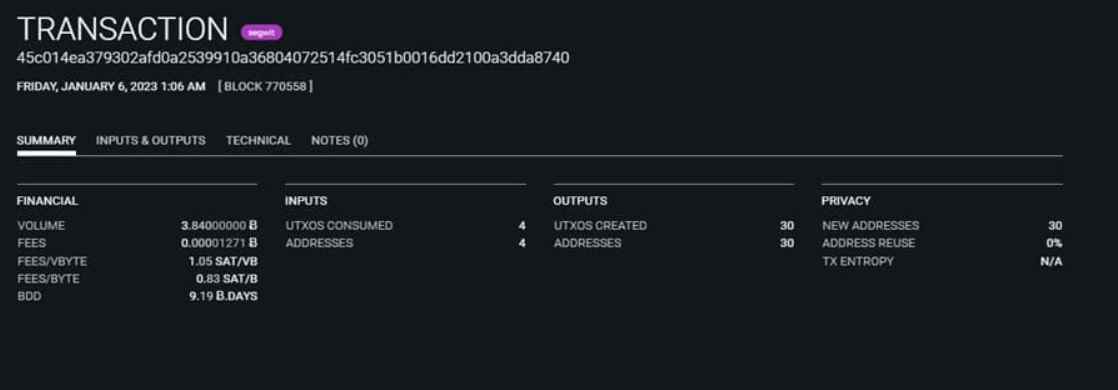
According to the monitoring application known as OXT Observer, these kind of transactions were carried out less than a day ago for values ranging between 2 BTC and 3 BTC on average.
The practice of breaking up stolen money into a series of smaller transactions is referred to as “peelchain” (peel or break the chain). This enables the criminal to swap the stolen money for another kind of cash in a manner that is less obvious to law enforcement and makes it more difficult for them to track the money.
It is suspected that the hacker in question hid the trail of these Bitcoin transactions by using a Bitcoin mixer in this particular instance. In other words, he hid the final destination of the funds by using a piece of software that mingles his own transactions with a group of others.
Mixers are tools focused on privacy rather than on money laundering, contrary to what has been portrayed in the media in the past. This is an important point to keep in mind.
You can see that the transaction in issue does not tell where the bitcoins are going if you examine the information that OXT Observer provides for just one of these activities. This is because the transaction in question does not reveal the destination of the bitcoins. However, it displays the transaction as part of a more comprehensive collection.
The use of mixers would be the last precaution that this hacker would take in order to avoid being discovered. Two days ago, CriptoNoticias published an article in which they discussed the methods that this individual would have used in order to have a better level of control over the coins that were taken from Luke Dashjr.
In this regard, we are aware that the hacker carried out transfers to P2SH addresses, which enable the establishment of additional addresses that may receive or transmit BTC within a framework of requirements, the absence of which prevents the money from being spent. For instance, by using a P2SH address, it is possible to stipulate that the cash will only become accessible when a transaction involving several keys has been digitally signed.
Luke Dashjr, one of the Bitcoin Core engineers with the greatest expertise, disclosed a short while ago that a hacker had obtained one of his PGP keys. PGP keys are used to encrypt and safeguard files and other vital keys. Luke Dashjr shared this information less than a week ago. The exact same key was used in the theft of the developer’s online wallet, which was carried out by the thief.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
