Cybersecurity specialists have detected a new HTTP request smuggling attack that uses a mix of legitimate and malicious requests with the ability to generate multiple problems for any corporate network. The report was filed by security firm Bishop Fox.

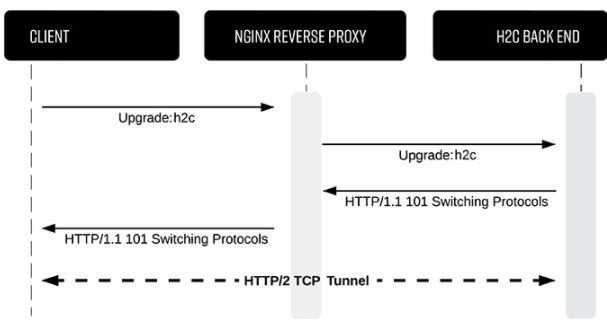
Jake Miller, the report’s investigator, says the consequences of this attack can be devastating to any system. The attack, dubbed “h2c smuggling,” is based on the HTTP/2 protocol, initiated by an HTTP/1.1 header sent through unencrypted communication, and occurs when a threat actor uses h2c to send requests to an intermediary server (or proxy server), capable of bypassing server access mechanisms.
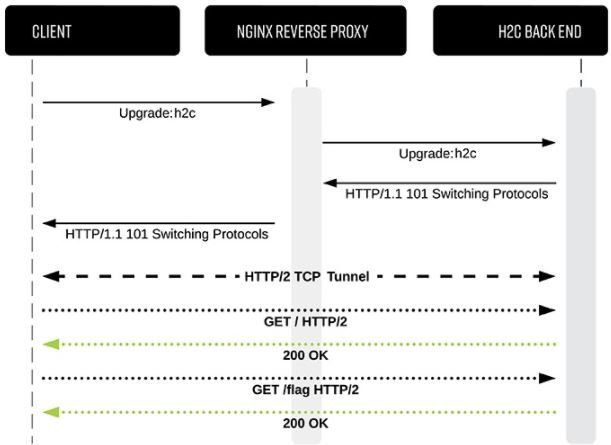
According to the expert, malicious hackers could use this attack to forge headers in internal communications and access the endpoints of a compromised network. Miller says it published the vulnerability due to the large number of clients that could be impacted by the attack: “We found affected servers in all kinds of organizations, suggesting that this flaw could be a general problem,” he adds.
Regarding the scope of this failure, the expert believes that its impact could be large enough to affect any proxy, including endpoints such as APIs or payments that could be affected regardless of other proxy endpoints.
Consumers may not be directly affected by this attack, although unauthorized access to their account information may occur: “Organizations that rely on proxies to prevent access to sensitive terminals could restrict the use of internal headers to mitigate attack risk,” Miller says.
This is a barely discovered attack vector, so researchers have not been able to determine if it has been actively exploited. Previously, counterfeiting and smuggling attacks on similar HTTP requests have been used, leveraging HTTP processing failures to access internal management panels, perform spoofing attacks, unlawfully accessing the networks of thousands of organizations.
Of course, the active implementation of this attack has its own limitations. For example, threat actors would have to figure out exactly what malicious tasks might be performed once they have accessed the compromised networks, mitigating the negative impact since this method only provides access to backend systems.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
