HTTP/2 Rapid Reset Zero-Day Vulnerability
Recent months have witnessed the emergence and exploitation of a distinctive zero-day vulnerability, dubbed “HTTP/2 Rapid Reset”, resulting in unprecedented Distributed Denial of Service (DDoS) attacks. This sophisticated technique, active since August, has shattered previous benchmarks in its magnitude and intensity.
Technical Dissection
Vulnerability Synopsis
The HTTP/2 Rapid Reset attack exploits a subtle frailty within the HTTP/2 protocol framework, manipulating its intrinsic stream cancellation functionality. Malevolent actors ingeniously initiate and instantaneously abort requests in rapid succession, inundating and incapacitating target servers and applications. This vulnerability is cataloged under CVE-2023-44487.
Mechanism of Attack
Overview
The HTTP/2 Rapid Reset attack leverages a specific facet of the HTTP/2 protocol: the stream cancellation mechanism. This mechanism, originally devised to facilitate clients in aborting initiated requests when responses are rendered unnecessary, has been perverted by adversaries to orchestrate DDoS attacks.
Mechanism Elucidation
Under normal operational circumstances, a client dispatches a request to a server, anticipating a corresponding response. Should the client deem the response unnecessary (perhaps due to user navigation away from a partially loaded webpage), it transmits a stream cancellation signal, instructing the server to cease processing the request.
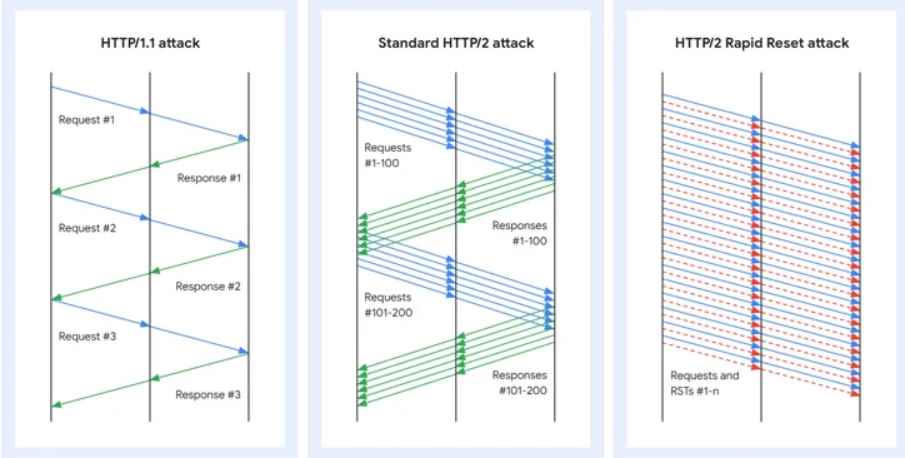
In the context of the HTTP/2 Rapid Reset attack, malevolent actors automate this sequence, dispatching and then immediately aborting requests. This automated “dispatch-abort” cycle is executed on a massive scale, generating a deluge of requests and cancellations that servers must process, leading to server resource exhaustion.
Illustrative Example
Consider the following hypothetical scenario to elucidate the attack mechanism:
- Initiation Phase: A malevolent actor commandeers a botnet comprised of numerous compromised devices. Each device within this digital legion is programmed to assail specific servers operating under the HTTP/2 protocol.
- Attack Launch: Devices within the botnet dispatch seemingly legitimate requests to the targeted servers, followed swiftly by cancellation signals, effectively pre-empting server processing of the initial requests.
- Overload Phase: Target servers are inundated with paired requests and cancellations. The rapid resource allocation and deallocation for each pair exert significant strain on the servers, leading to resource exhaustion and service denial.
- Amplification Phase: The attack is inherently asymmetric, requiring minimal effort from the attacking devices compared to the resource-intensive processing demanded of the servers. This asymmetry enables a relatively diminutive botnet to overwhelm robust servers.
- Outcome Phase: The resultant server overload manifests as service denial for legitimate users, who experience connectivity delays or outright connection failures as servers grapple with the malicious traffic onslaught.
Significance
The HTTP/2 Rapid Reset attack is particularly insidious due to its capacity to generate voluminous requests with a relatively small botnet, serving as a potent instrument for executing large-scale DDoS attacks. The ease of automation coupled with the substantial impact on targeted servers underscores the critical nature of this vulnerability, necessitating immediate attention and mitigation from the cybersecurity community.
Mitigation Strategies
Leading corporations in the tech industry, including Amazon, Cloudflare, and Google, have successfully mitigated attacks peaking at 398 million requests per second. These entities have adopted and implemented a suite of measures, ranging from network capacity augmentation to the development and deployment of technologies specifically engineered to counteract the deleterious effects of this zero-day vulnerability. Through these concerted efforts, there has been a notable enhancement in mitigation capabilities and resilience against attacks of massive scale.
Impact Assessment and Industry Response
Immediate Impact
The exploitation of this vulnerability has precipitated a spike in error reports from the clientele of affected companies. The sheer volume of incoming attacks has overwhelmed certain network components, inducing intermittent errors and performance degradation for a subset of customers.
Industry Mobilization
In the wake of successful mitigation initiatives, companies have engaged in responsible disclosure protocols and forged collaborations with industry counterparts to fortify the collective security posture of the internet. Patches designed to preemptively thwart the exploitation of this vulnerability are currently under development, with organizations strongly advised to expediently deploy these patches across all internet-facing web servers to bolster their defensive perimeters.
Recommendations for Practitioners
- Conduct a thorough examination and remediation of all internet-facing systems, applying provided mitigations where necessary.
- Ensure robust DDoS protection mechanisms are in place, covering applications, DNS, and network traffic, and consider the deployment of Web Application Firewalls for enhanced security.
- Expedite the deployment of patches for web servers and operating systems across all internet-facing web servers to fortify defenses against this novel threat vector.
- As a contingency, consider the deactivation of HTTP/2 and HTTP/3 protocols to mitigate the threat, bearing in mind the potential for significant performance degradation.
- Contemplate the integration of secondary, cloud-based DDoS L7 providers at the network perimeter to enhance resilience against DDoS attacks.
The HTTP/2 Rapid Reset zero-day vulnerability represents a formidable threat to the cybersecurity landscape, facilitating the execution of record-breaking DDoS attacks by malicious actors. It is imperative for organizations to adopt proactive defensive measures and deploy patches to safeguard their networks against this emergent threat. Through collaborative endeavors and responsible disclosure practices, the cybersecurity community is poised to navigate and mitigate the risks associated with this zero-day exploit, thereby ensuring the continued security and integrity of the internet ecosystem.
For practitioners seeking deeper technical insights and mitigation tactics, registration for upcoming webinars hosted by leading cybersecurity firms is recommended, alongside regular consultation of their official websites for updates on the evolving situation.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
