Cybersecurity specialists report the detection of a new technique to collect credentials from stolen users abusing the features of the renowned platform for the analysis of URLs and potentially malicious files VirusTotal, currently owned by Google. Researchers from security firm SafeBreach used a VirusTotal license to demonstrate their attack, managing to collect more than a million login credentials.
A user licensed in VirusTotal can query the service dataset with a combination of queries by file type, file name, sent data, country, and file content, among others. The researchers thought that, by abusing this platform, threat actors could search for vulnerable websites, Internet of Things (IoT) devices, and data breach incidents. The attack is based on the use of VirusTotal tools and APIs, such as VirusTotal Query, VirusTotal Graph, and Retrohunt.
In conjunction with these tools, experts also used some known variants of malware, such as RedLine Stealer, Azorult, Raccoon Stealer, and Hawkeye, in addition to some hacking forums such as DrDark and Snatch_Cloud. Using RedLine Stealer, researchers were able to abuse some browsers to collect data such as saved credentials, autofill data, and payment card details; upon execution, the malware takes an inventory of the system that includes information such as username, location data, hardware configuration, and security software scanning.
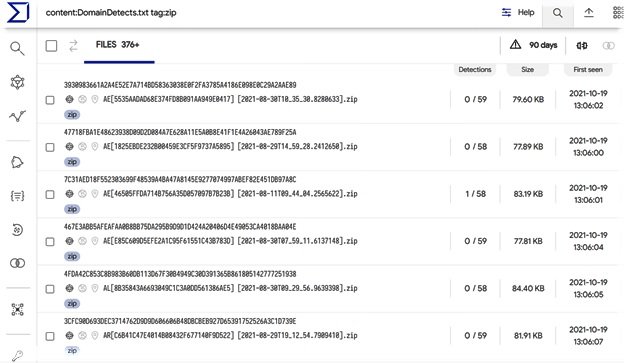
It all starts with using VirusTotal Query to search for binary files identified by at least one antivirus engine like RedLine, which in the research yielded 800 results. Experts also searched for files called DomainDetects.txt, which is one of the file names the malware extracts, getting hundreds of files in response.
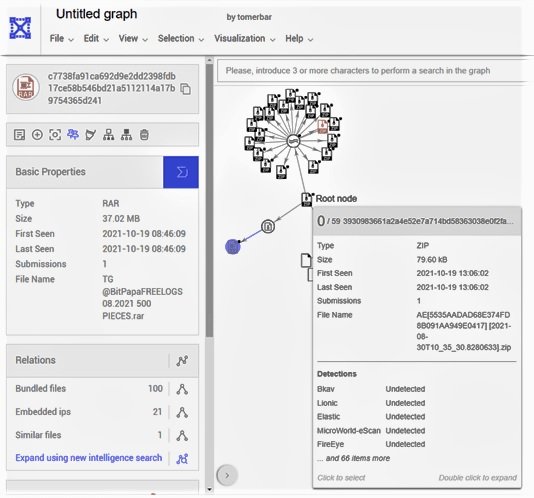
Subsequently, using VirusTotal Graph the researchers found a file of their search results that was also included in a RAR file containing extracted data belonging to 500 victims, including 22,715 passwords for hundreds of different websites. Additional results included even larger files, which contained more seemingly active passwords.
The findings have already been notified to Google, along with a number of recommendations to mitigate abuse of these features, including periodically searching and deleting files with sensitive user data and banning API keys that upload these files.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
