Experts report that the websites and entire infrastructure of the REvil ransomware group have remained offline for the most recent hours. This group, also known as Sodinokibi, is able to operate through multiple illegal websites used to communicate with the victims of its attacks and to leak stolen information.
Reports indicate that, since Monday night, REvil’s websites have remained offline with no apparent explanation. Below is a screenshot of one of REvil’s websites on the Tor network, which shows an error message.
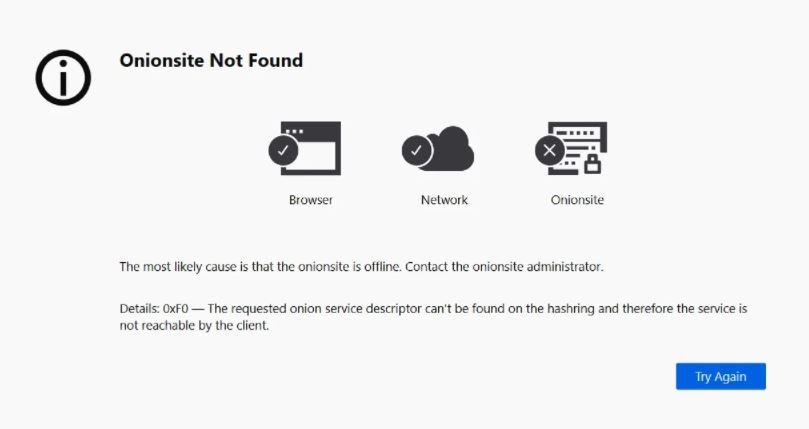
In this regard, Tor Project member Al Smith mentioned: “This error means that the onion site was disabled or is offline. The exact reason should be known to the website operators.”
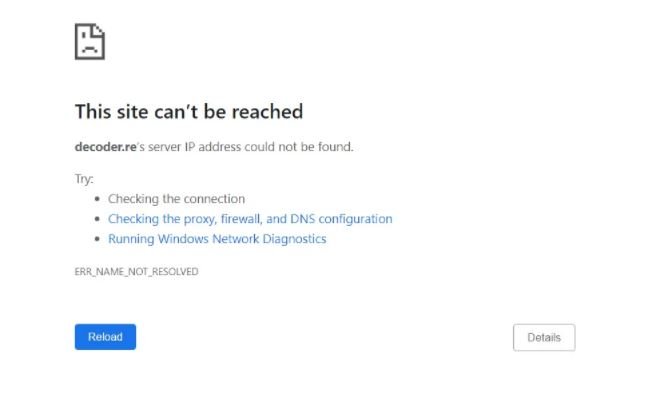
Although the platforms associated with REvil often display this kind of error, it is very strange that all these sites close simultaneously. In addition, the conventional web site decoder.re can no longer be resolved by DNS queries, which could mean that the domain’s DNS records have been extracted or that its backend DNS infrastructure has been shut down.
REvil has been the main actor in some of the most recent hacking incidents. In early July, this ransomware group infected the networks of more than 1500 organizations by abusing a severe vulnerability in the Kaseya VSA remote management software. Although hackers initially demanded about $70 million USD in exchange for restoring affected systems to normal, the demand dropped to $50 million USD shortly after the attack.
These recent attacks have drawn the attention of authorities in the U.S., who have announced the adoption of tougher measures for the investigation of these cybercriminal groups. However, this doesn’t seem to worry REvil’s operators too much, who even provide interviews for platforms specializing in cybersecurity issues.
Until now it is not known if these failures were the result of a failure in the Tor network or was a premeditated action by REvil operators, although members of the cybersecurity community do not rule out any possible explanation. This wouldn’t be the first time hackers have decided to shut down their operations; on previous occasions, the DarkSide and Babuk ransomware groups decided to voluntarily terminate their activities due to increasing scrutiny from the authorities.
This is not to say that hacking groups stop operating, since after the closure of operations hackers usually rename their malicious activities or integrate into other cybercriminal groups.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
