The major Barnes and Noble bookstore announced that the systems used by online readers were experiencing some flaws over the weekend. This Wednesday afternoon, the company unveiled that its security teams were still working to restore their systems completely.
This explanation was not enough for users, who did not understand why they were not able to access the content of their e-books, so Barnes and Noble released a statement about it:
“We continue to experience a system failure that is disrupting certain B&N Press and NOOK functions. We are urgently working to get all services back up and running normally. Unfortunately, the recovery process has taken longer than expected, so we want to apologize for the inconveniences caused by this incident.” The company emphasizes that your clients’ financial information is completely safe.
In some cases, the company sent its users a letter to give greater context to the incident: “It is with great regret that we informed them that on October 10 Barnes and Noble was the victim of a cyberattack that resulted in unauthorized access to some of our systems.” The company asks its users to remain alert about any attempted cyberattack using the information exposed, as well as ensuring that further reports will be shared as soon as possible.
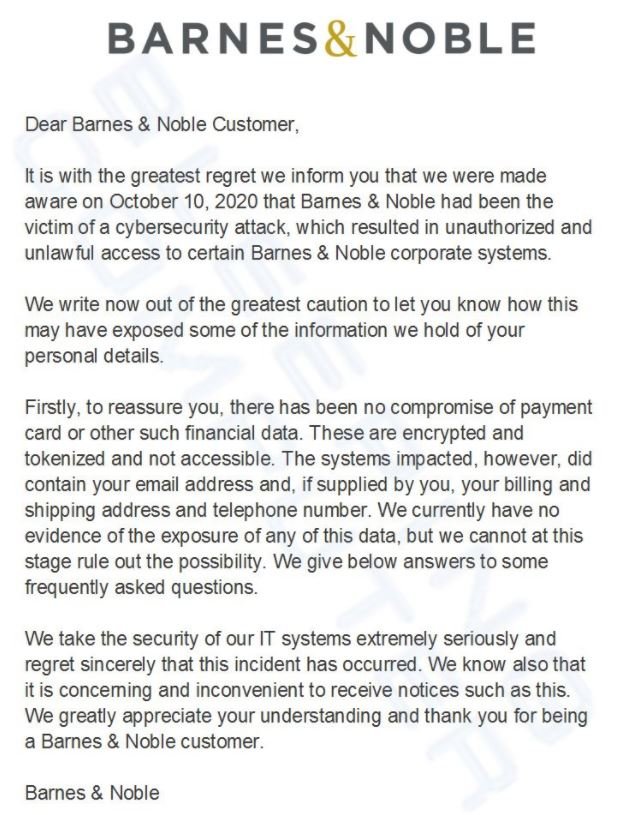
In its letter, the company also notes that many of the potentially exposed personal data are protected with encryption, so malicious hackers are unlikely to abuse the exposed information.
Cybersecurity expert Chris Moschovitis believes the company has underestimated the effects of a cyberattack, so they need to take better steps to protect their customers. The expert also believes that users should be careful about the amount of information they share with public companies; regarding the incident, Moschovitis believes it could be a ransomware attack or some other variant of malware.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
