Research from cybersecurity and threat intelligence company Cyble identifies a spike in attacks targeting virtual network computing (VNC) — a graphical desktop-sharing system that uses the Remote Frame Buffer (RFB) protocol to control another machine remotely— in critical infrastructure sectors.
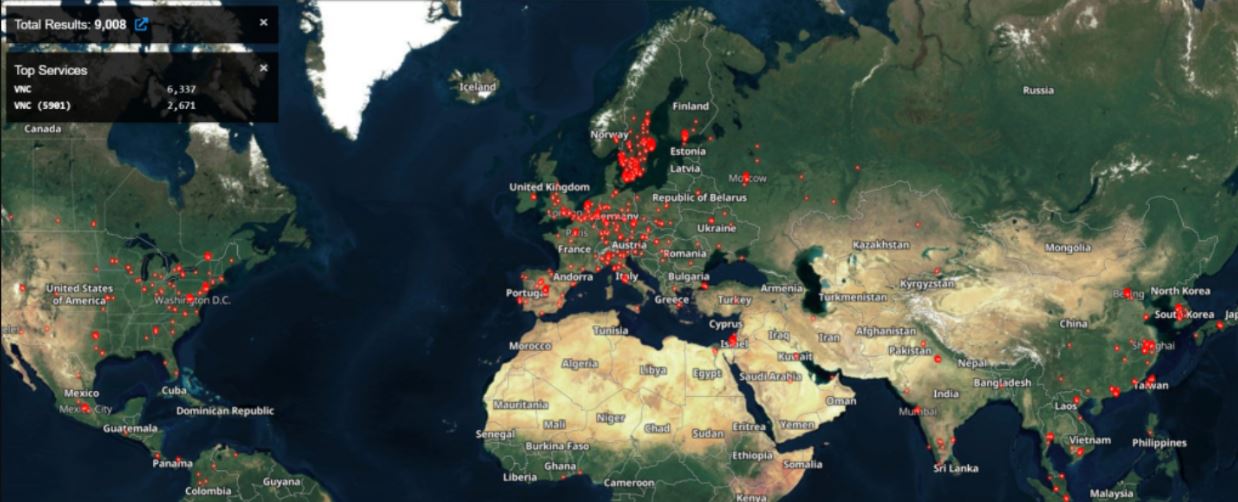
Analyzing their Global Sensor Intelligence (CGSI) data, researchers observed a spike in attacks on port 5900 (the default port for VNC) between July 9 and August 9. Most of the attacks originated in the Netherlands, Russia and Ukraine, according to the company, and highlight the risks of exposed VNC in critical infrastructure.
Exposed VNCs Put Industrial Control Systems at Risk
According to a blog post, organizations that expose VNCs over the Internet, by not enabling authentication, extend the reach of attackers and increase the probability of cyber incidents. More than 8,000 exposed VNC instances were detected with authentication disabled. They also discovered that exposed assets connected via VNC are frequently sold, bought, and distributed in cybercrime forums and marketplace.
“Although the count of uncovered VNCs is low compared to previous years, it should be noted that those found during the time of analysis belong to various organizations that fall within critical infrastructure such as water treatment plants, manufacturing plants, research facilities,” according to the firm. Researchers succeeded in shrinking several human-machine interface (HMI) systems, supervisory control and data acquisition (SCADA) systems, and workstations, connected via VNC and exposed on the Internet.
An attacker accessing a dashboard can manipulate the operator’s default settings and can change values for temperature, flow, pressure, etc., which could increase stress on equipment, causing physical damage to the site and potentially to nearby operators. Exposed SCADA systems could also be operated by an attacker, who could further obtain confidential and sensitive information that can be used to compromise the entire ICS environment. Exposing systems in this way allows attackers to target a particular component within the environment and start a chain of events by manipulating various processes involved in the targeted installation.
Vulnerable VNC is an easy target for attackers
VNC allows access to a targeted machine and has woefully insufficient tools to protect those machines, even when using passwords. The damage that can be caused depends on the organization and user permissions under which VNC is running. In one example, a Ministry of Health system was exposed, which means private health information is exposed.
Remote desktop services, like VNC, are one of the easiest targets for hackers to identify, as they operate on well-known default ports and there are many tools out there to search for these services and brute-force the passwords. Any organization running public-facing remote access services with authentication not configured is basically putting out a ‘welcome’ sign to adversaries. Finding these kinds of open services is trivial, so any actor, from script kiddies to the most sophisticated, could take advantage of these misconfigurations to gain initial access to the environment. One of the challenges of protecting critical infrastructure environments is that many advocates assume there is an air gap that separates traditional IT networks from ICS networks. Segmented networks don’t always exist, and those responsible for defense need to have real-time visibility into public-facing services. These services need to have restricted network access with strong authentication enabled, including base-based authentication.” in certificates.
Businesses should limit their exposure to the Internet using VNC and use multi-factor authentication (MFA) for any remote connectivity to a network, including through VPNs or directly using protocols such as RDP, VNC, or SSH.
Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator.
He is a cyber-security researcher with over 18 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked on the projects of Citrix and Google in deploying cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.
