The implementation of an automated audit on IT systems is part of the essential knowledge for any cybersecurity specialist. This time, pentesting experts from the International Institute of Cyber Security (IICS) will show you four tools to identify vulnerabilities in Linux systems automatically.
The cybersecurity community considers Linux to be a very secure operating system, although security features can vary considerably between the various distributions available. To mitigate the negative impact of potential flaws, pentesting experts must perform periodic security audits before problems accumulate and escalate.
The utilities shown below will help researchers during the analysis and pentesting phases, automating some research steps.
LYNIS
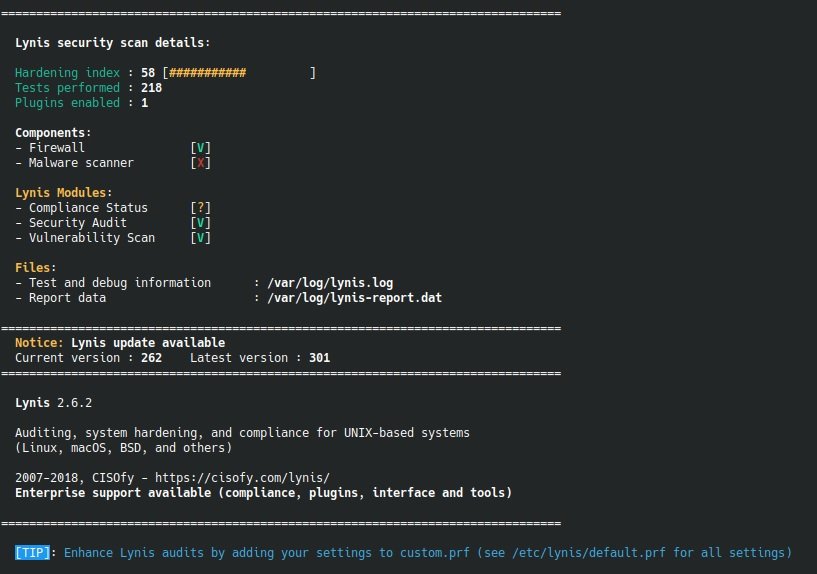
This is an audit tool for UNIX-like systems (Linux, OS X and Open BSD, among others). Lynis helps pentesters verify the means of protection available on the system, as well as provide tips for proper security configuration through general system analysis, vulnerable software packages, and potential configuration issues.
Lynis supports the following Linux distributions:
- CentOS
- Debian
- Fedora
- OEL
- openSUSE
- RHEL
- Ubuntu
Among its main features, pentesting experts highlight the following:
- Automated security audit
- ISO27001, PCI-DSS & HIPAA compliance tests
- Vulnerability analysis
- Asset configuration and management
- Patch and update management
- Pentesting
- Intrusion detection
Installation and launch
The tool must be installed via YUM:
$ yum install lynis
On Debian-like systems:
$ apt-get install lynis
For openSUSE:
$ zypper install lynis
For installation via Git:
$ cd /usr/local
$ git clone https://github.com/CISOfy/lynis
$ cd lynis
Pentesting experts mention that it is also possible to directly download and unzip the file with the utility to a previously created directory. Lynis works without preliminary configuration; you can start a basic scan using the following command:
$ lynis audit system
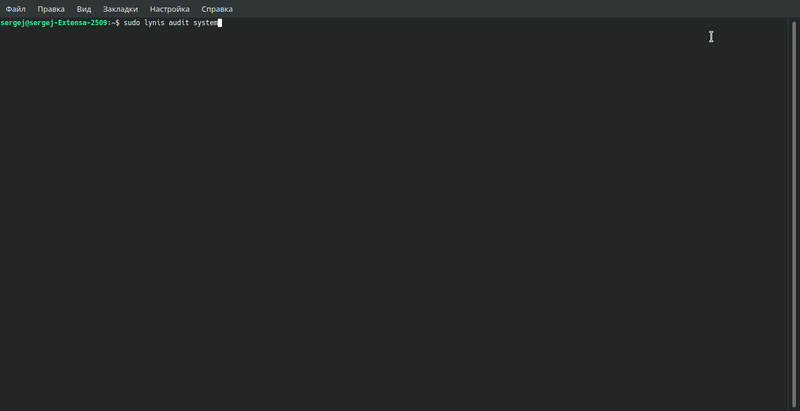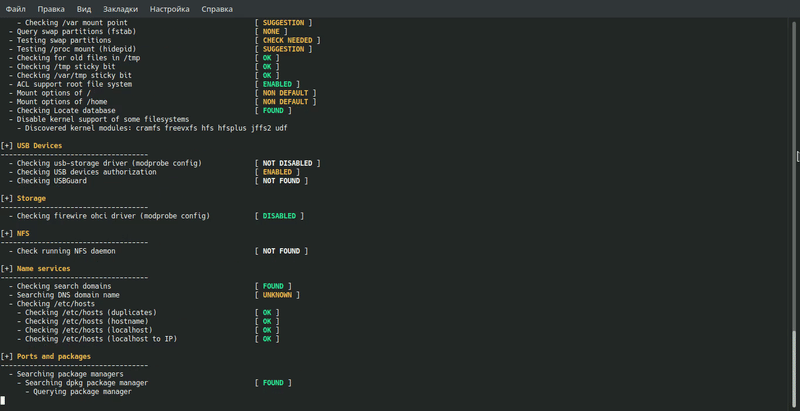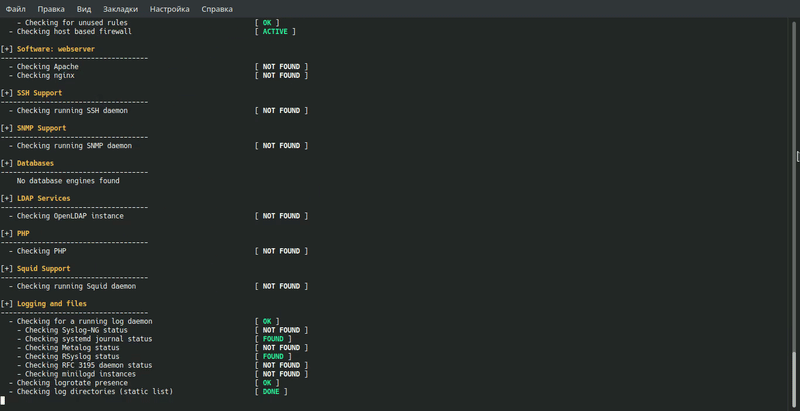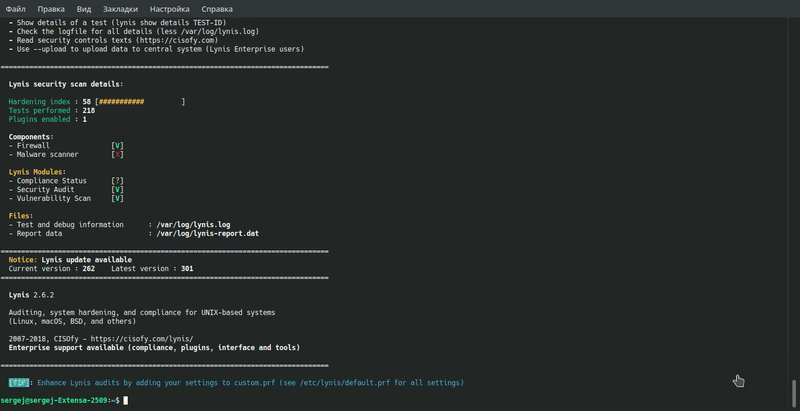
For a quick start, try the following features:
- checkall, -c: Start scanning
- check-update: Searching for updates
- cronjob: Start Lynis through the programmer
- quick, -Q: Don’t expect user input, except for errors
- version, -V: Show the current version of Lynis
LUNAR
Lockdown Unix Auditing and Reporting (LUNAR) is a script used by pentesting experts to generate a UNIX host security audit report. This script is based on CIS and other frameworks. LUNAR’s essential features are related to system safety assessment, self-assessment, and security improvements.
LUNAR is available for the following Linux distributions:
- RHEL 5.6.7
- Centos 5,6,7
- Scientific Linux
- SLES 10,11,12
- Debian
- Ubuntu
- Amazon Linux
- Solaris (6,7,8,9,10 and 11)
- Mac OS X
The utility also supports the Amazon Cloud Platform (AWS) and Docker containers.
LUNAR is an sh command-line script, so no complicated installation steps are required. To get started, download the file from GitHub, unzip it to a previously selected directory, and run it from the command line.
$ ./lunar.sh –a
Pentesting experts recommend running the utility in audit mode (option -a).
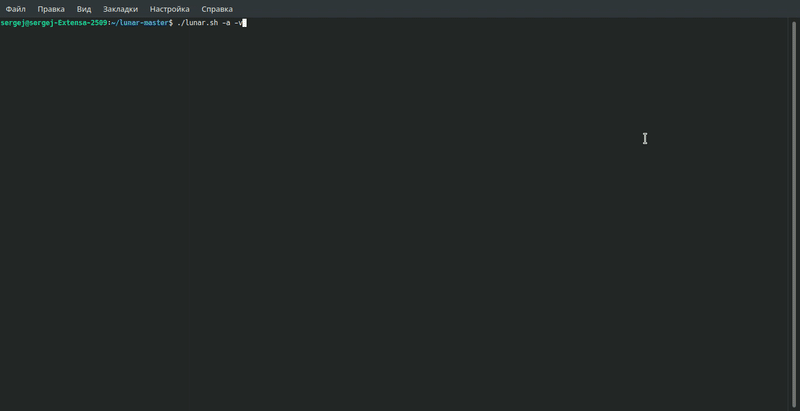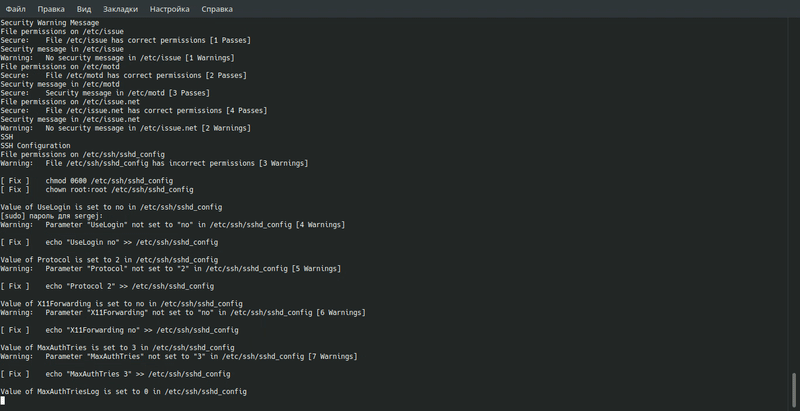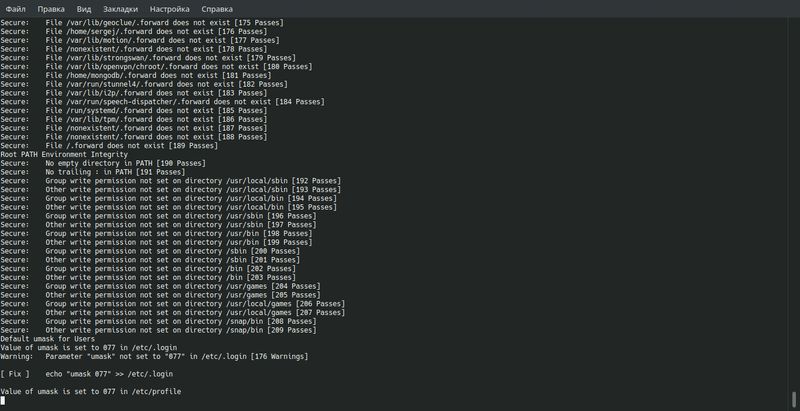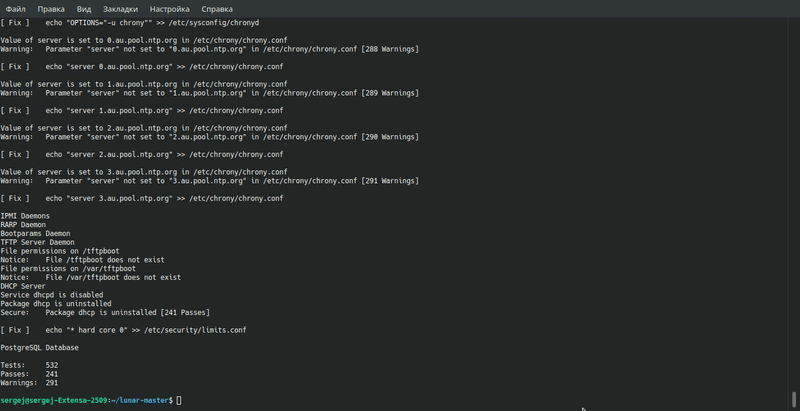
Below is a list of the main parameters of the utility:
- -a: Start in audit mode without making system changes
- -v: Detailed mode (used with -a & –A)
- -d: View proposed changes to the system before adding them to the settings
- -s: Start selective mode
- -l: Start in lockdown mode (make changes)
- -S: List all UNIX features available for custom mode
- -W: List all AWS features available for custom mode
- -D: List all Docker features available for custom mode
- -Z: Show changes made to the system
- -b: List backup files
- -n: Show available code segments
- -u: Restore from backup
LSAT
The Linux Security Audit Tool (LSAT) is a modular development, so new features can be quickly added. LSAT verifies inetd logs, searches for unnecessary RPMs, and verifies kernel versions, pentesting experts mention.
LSAT is available for the following distributions:
- Gentoo
- RedHat
- Debian
- Mandrake
- Linux Mint 18
- CentOS 7
- Sparc: Sun OS (2.x)
- Redhat sparc, Mandrake Sparc
- Apple OS X
Experts mention that the tool should also work properly in Slackware and other less popular distributions.
Installation and launch
LSAT is installed using the construction from the source and has a preconfigured automatic configuration: autoconf.
$ ./configure
$ make
To install on the system in /usr/local/bin:
$ make install
Basic tool options:
- -d diff: Current and old md5, output to lsatmd5.diff
- -m: Testing for a specific distribution
- redhat
- debian
- mandrake
- solaris
- gentoo
- macosx
- -a: Show the help page
- -o: This is the name of the output file, by default lsat.out
- -r: Check rpm integrity, etc.
- -s: Silent mode
- -v: Detailed output
- -w: Output file in HTML format
- -x: Exclude modules from the list of files from checks
LBSA
This is a basic Linux security audit scenario for continuous policy en application (CPE). According to pentesting experts, it can be run from the command line as a root user or on a regular basis by the programmer.
This script is specifically used to inform the administrator of possible configurations that can be changed to keep the system secure. LBSA focuses on finding:
- Common vulnerabilities in Linux login account settings
- Common vulnerabilities in SSH configuration
- Common vulnerabilities in temporary and shared memory file systems (/tmp, /var/tmp, /dev/shm, etc.)
- Recommendations for file system permissions
- Heartbeat and DRBD configuration file permissions
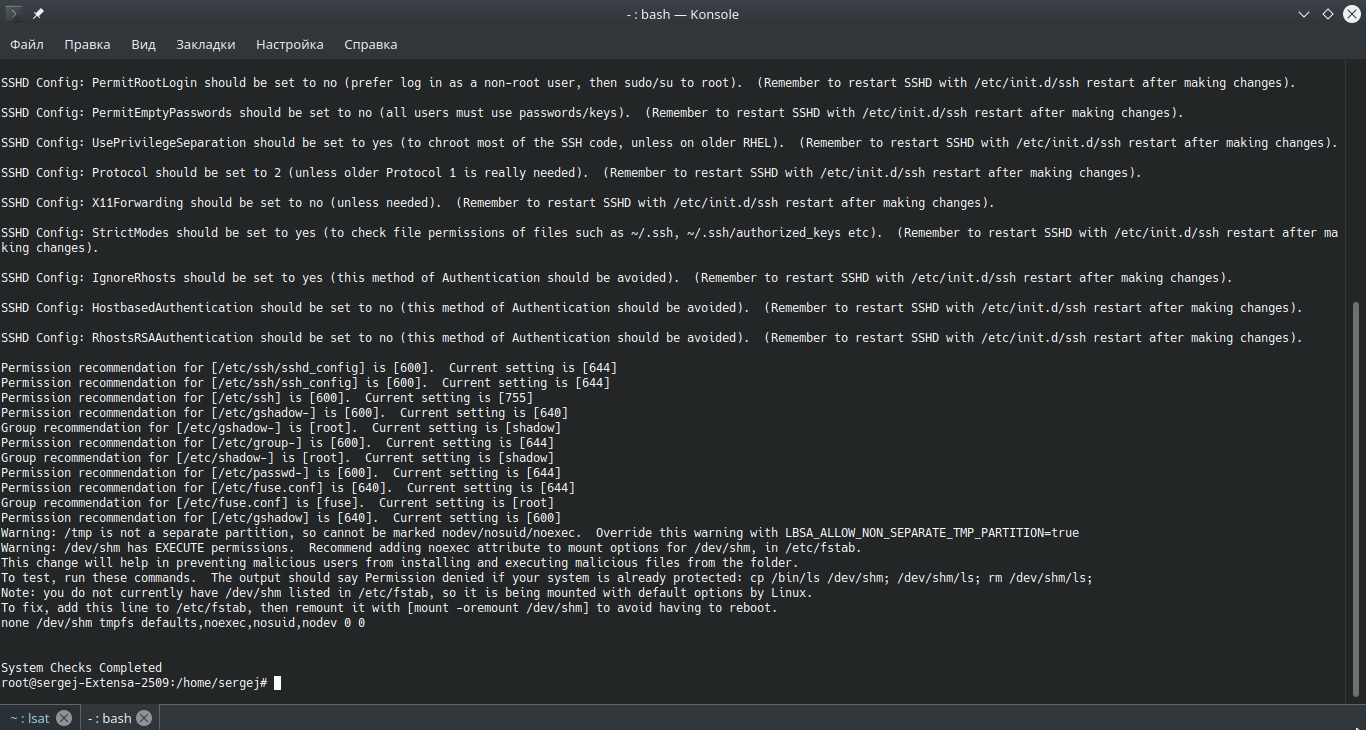
The full version of the script can be found on its developers’ official page, but before using the tool you should remember that, in some cases, changes made by LBSA can cause a decrease in the performance of your system. This script should work immediately and IICS experts only recommend some small but important system changes that should be easy to make.
For more material like this, feel free to visit the official platforms of the International Institute of Cyber Security (IICS).
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
