Researchers from the Arctic Wolf Labs team observed a strong overlap with the Tactics, Techniques, and Procedures (TTPs) associated with ransomware attacks that aim to exploit the CVE-2022-29499 as the initial access vector.
Although these attacks were not associated with a single ransomware operator, researchers have been able to identify malicious behavior comparable to that of the Lorenz APT. In a document published yesterday, security researchers revealed that the initial malicious activity emanated from a Mitel VoIP device located at the network perimeter.
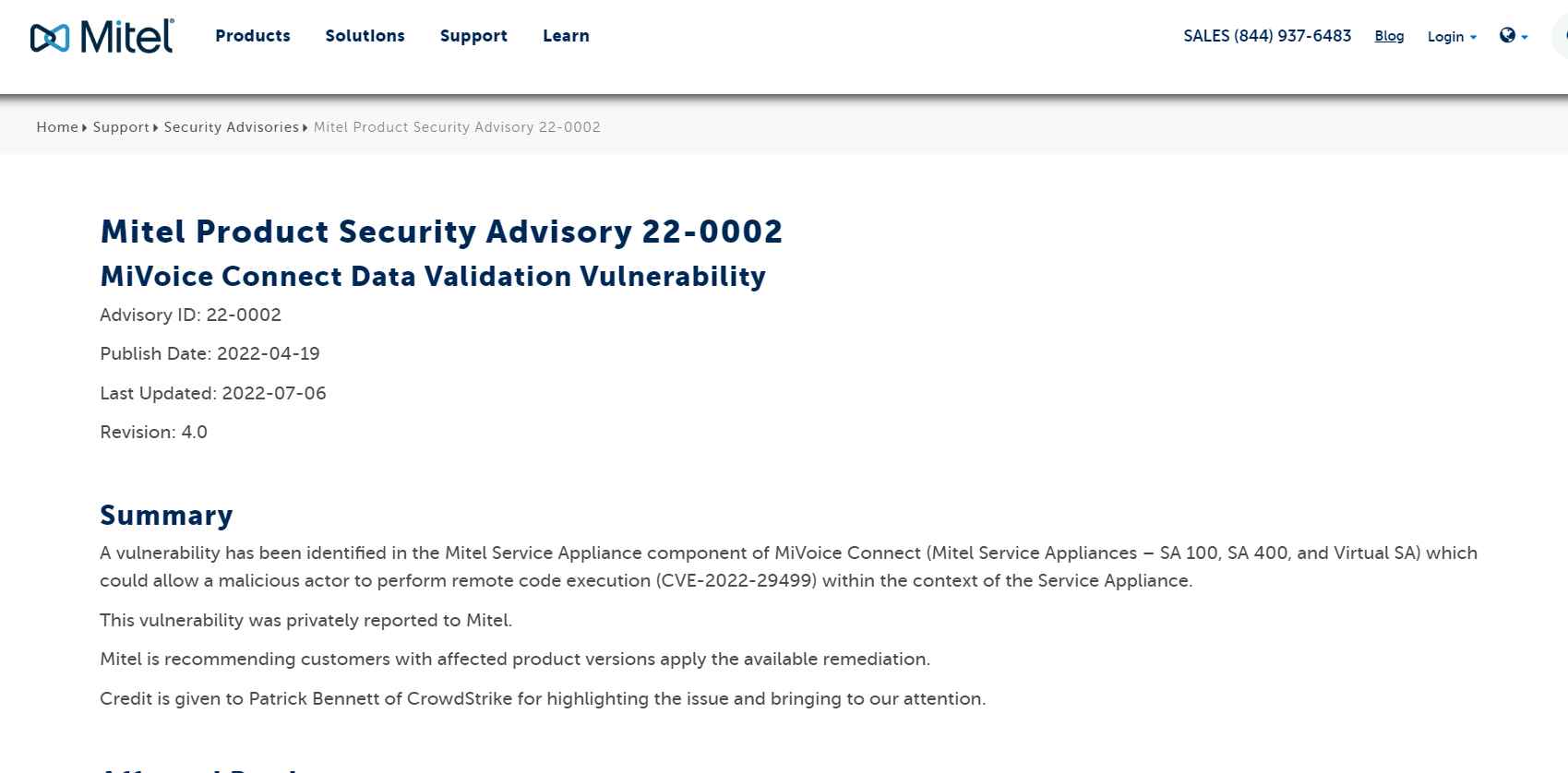
“Lorenz exploited CVE-2022-29499, a remote code execution affecting the Mitel Service Appliance component of MiVoice Connect, to achieve a reverse shell, and then used Chisel as a tunneling tool to pivot into the environment.”
According to security expert Kevin Beaumont, this is an essential addition to a ransomware operator’s arsenal, as Mitel’s Voice over IP (VoIP) technologies are used by businesses in critical industries around the world (including many government agencies). ), with more than 19,000 devices currently vulnerable to Internet-based attacks.
Mitel has patched the vulnerability by releasing security updates in early June 2022, following the release of a fix script in April for affected MiVoice Connect versions.
Since December 2020, the Lorenz ransomware group has attacked various businesses globally, demanding hundreds of thousands of dollars in ransom from each victim.
This group is also known for selling the stolen data obtained before encryption to other actors to coerce their victims into paying the ransom, as well as selling access to their victims’ internal networks along with the stolen data.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
