Researchers in the field of information security have found a new strain of ransomware that has been given the name CACTUS and that infiltrates targeted networks by exploiting known weaknesses in VPN equipment. Since March 2023, CACTUS has been seen targeting major business companies, and it uses double extortion techniques to obtain sensitive data before it is encrypted. No evidence suggests that the ransomware is currently using a data leak site.
Once CACTUS actors have successfully gained access to a network, their next step is to try to enumerate user accounts and available endpoints. After this, they will create new accounts and utilize bespoke scripts to automate the distribution and detonation of the ransomware encryptor using scheduled processes. In addition to that, the malware installs a backdoor in SSH for permanent access, employs PowerShell instructions to carry out network scanning and identify devices for encryption, and makes use of Cobalt Strike and the Chisel tunneling tool for command-and-control purposes.
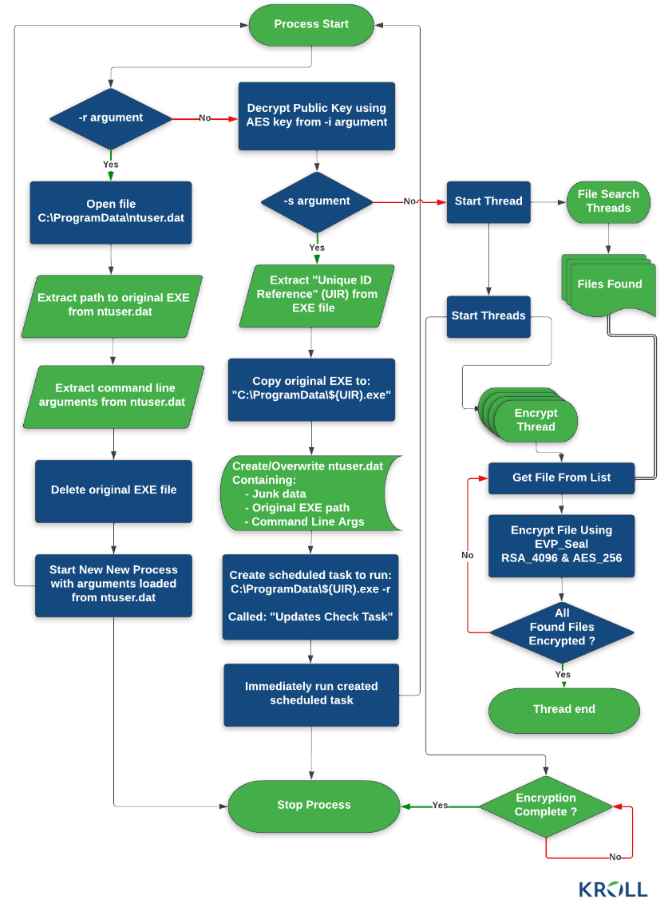
CACTUS encrypts itself, making it harder to detect and helping it elude antivirus and network monitoring technologies. This is accomplished via the use of a batch script that extracts the ransomware binary using 7-Zip, followed by the removal of the.7z archive before executing the payload. In addition, actions are made to deactivate and remove security solutions, and credentials for escalation privileges are extracted from web browsers and the Local Security Authority Subsystem Service (LSASS).
The next step after gaining elevated privileges is lateral movement, followed by the exfiltration of data and finally the distribution of ransomware. This last step is accomplished by using a PowerShell script that Black Basta has also used in the past. CACTUS is designed to circumvent the detection of endpoint security measures. This is yet another technique for ransomware to totally dodge the endpoint security measures such as antivirus and EDR, and it demonstrates how simple it is for threat actors to launch an attack using ransomware despite the fact that the most advanced detection technologies in the world are now in use. Each year, ransomware is responsible for the total collapse of thousands of businesses. In each of these incidents, the businesses that were affected made significant investments in prevention tools and were given guarantees such as ‘completely effective against ransomware. Even the White House has admitted that our capacity to fight ransomware assaults is falling behind the rate at which they are becoming worse. It is just a matter of time until some company experiences a cyberattack, which will result in the loss of its essential data and infrastructure for good. We are unable to continue to depend on prevention since doing so expects us to be successful 100% of the time without fail. In addition to this, we need to put in place ransomware containment technologies that will swiftly stop the attack and air-gapped backup solutions that will allow us to restart the systems with the absolute minimum amount of downtime.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
