The Group-IB Threat Intelligence discovered the MajikPOS POS malware’s Command and Control (C2) server on April 19, 2022. C&C was found to be inadequately structured, and the manner it had been created allowed for the extraction of stolen credentials for additional investigation. Threat Intelligence specialists examined the server and discovered that it also houses the C2 management panel of Treasure Hunter, a different POS malware that also collects stolen credit card information. Investigators acquired data on the affected devices and the credit cards stolen as a result of this campaign after examining the malicious infrastructure. The hackers have stolen more than 167,000 payment records from at least February 2021 (as of September 8, 2022), primarily from the US.
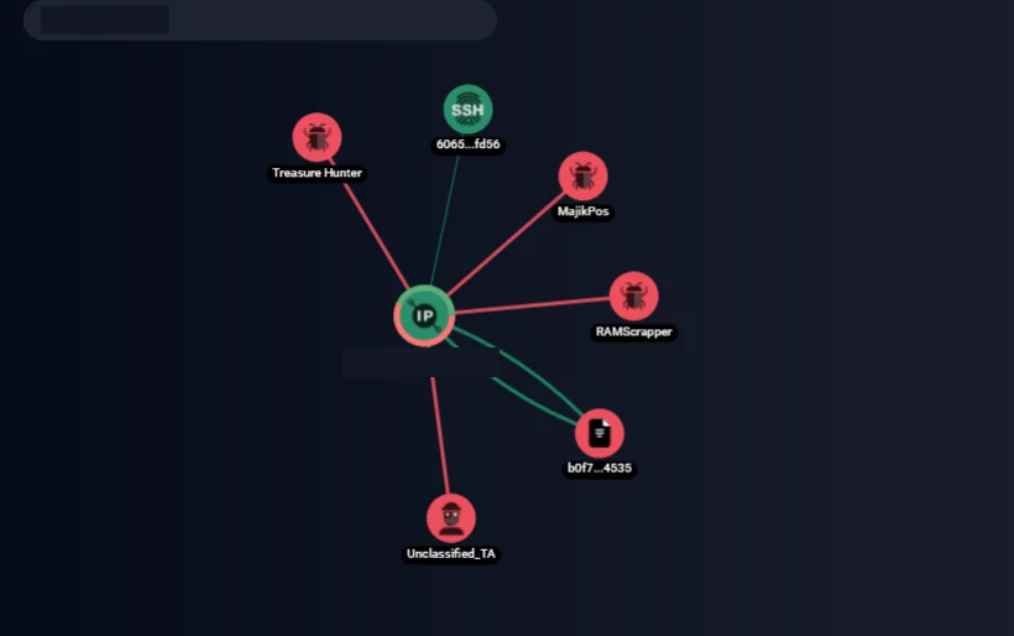
The panel is still in operation as of the time of writing this blog. Alert was send to the unit’s law enforcement partners and a US-based financial threat sharing group. Early in 2017, POS terminals in the US and Canada were the initial targets of the MajikPOS malware. On July 18, 2019, the user cartonash issued a notice about the sale of the MajikPOS (also known as MagicPOS) source code on the unofficial forum “exploit[.]in.” Additionally, the malicious actors offered to sell the shop’s source code, which was utilized to sell dumps that the malware had amassed. MajikPOS has been making the rounds on the DarkWeb ever since, making it challenging to pinpoint the origin of the threat. On the same server, Treasure Hunter malware’s command and control panel were also discovered to be active. 2014 saw the initial discovery of the POS malware known as Treasure Hunter. RAM scraping is its primary function. MajikPOS and the earliest steps of the kill chain are comparable. After infecting a POS terminal, the malware lists the processes that are currently active, grabs all usable credit card data from the RAM, and sends this data to a C2. Both of these malware panels include details about POS systems that have been attacked as well as stolen dumps. In the course of the research, experts examined around 90,000 distinct card dumps from the Treasure Hunter panel and about 77,400 from the MajikPOS panel. The number of victims continues to rise because the infection is still active as of the time this blog was written.
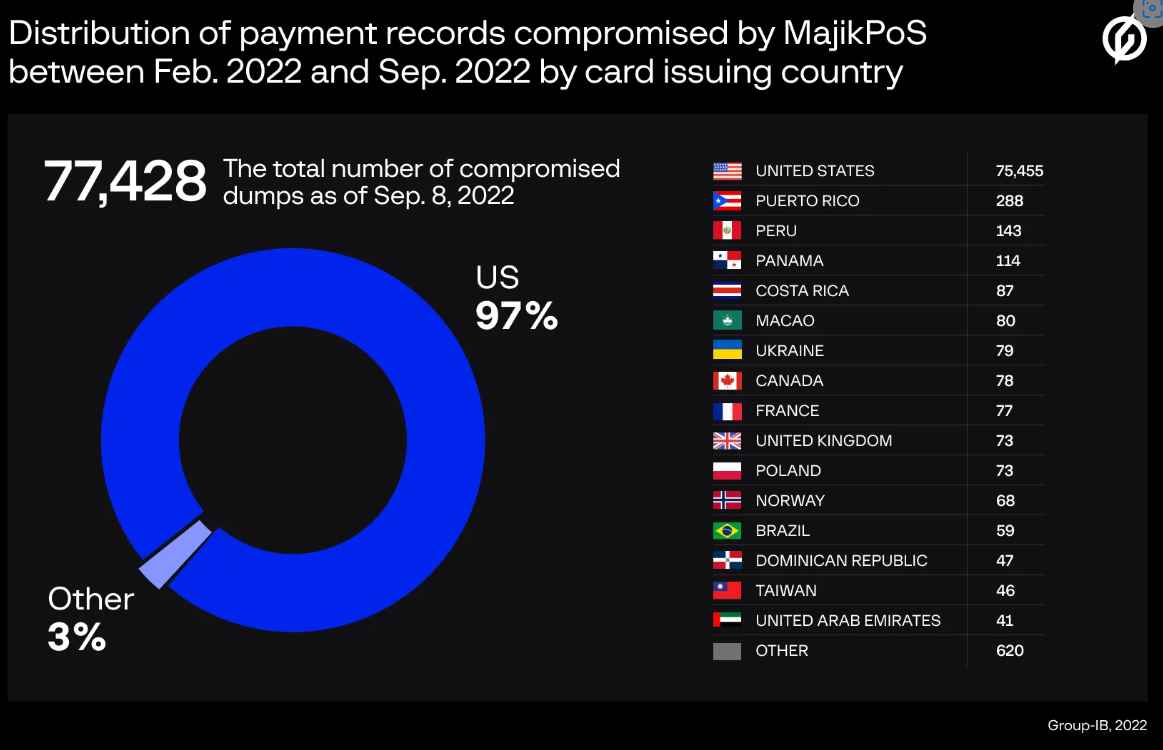
Although a dump itself cannot be used to make online transactions, criminals who purchase such data can cash out documents that were stolen. If the card-issuing organization doesn’t find the breach right away, thieves can create cloned cards (sometimes known as “white plastic”) and use them to make unauthorized in-person transactions or withdraw cash from ATMs.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
