Cybersecurity specialists mention that the developers of the Trickbot Trojan have added a new set of advanced features to prevent researchers from reverse-engineering this malware, protection based on the blocking of computers used for analysis.
Trickbot has become one of the main tools for stealing financial information and running ransomware. In addition, thanks to its modular nature, it became a popular choice for the implementation of other malware variants.
In their latest report, IBM Trusteer experts detail the finding of these new features, focused on avoiding analysis and reverse engineering. As you may already know, this process aims to dissect a malware sample, analyze its code, and figure out how it works and how to protect or mitigate its capabilities. The malware’s creators added three obfuscation methods to prevent ethical hackers from being able to analyze Trickbot.
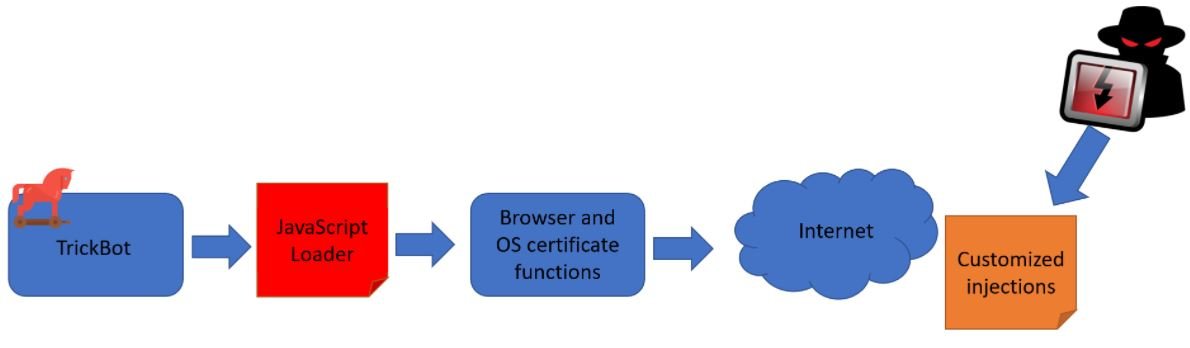
The first method is based on server-side injections, rather than loading them from infected machines. This way, malicious injections are less likely to reach researchers, in addition to using a JavaScript downloader or loader for communication with the hackers’ server.
The second method is the use of HTTPS communications when injections are obtained from Trickbot’s C&C server. Hackers use flags to specify the page a victim is browsing and requests from unknown or “unwanted” sources can be ignored, blocking data flows and preventing researchers from properly analyzing communication flows.
The third method consists of an anti-debugging script capable of triggering a memory overload if a researcher performs a “code beautification”, a technique to make large swaths of code more readable and easier to analyze. When the Trojan detects this practice, it will start a loop automatically.
The researchers mention that the malware operators also use Base64 obfuscation, redundant scripts and code, and native feature patches in order to trick researchers.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
