Cybersecurity specialists have found at least 14 security vulnerabilities in NicheStack, a popular TCP/IP library used in industrial equipment and OT devices manufactured by more than 200 vendors. This set of flaws, dubbed as INFRA:HALT, was discovered by security teams from Forescout and JFrog.
As some may know, NicheStack is a C library developed by HCC Embedded that can be added to a device’s firmware to facilitate internet connectivity and other networking. Such libraries are common on thousands of devices, although the cybersecurity community rarely focuses on the flaws of this technology.
A couple of years ago some similar flaws were detected in common TCP/IP stacks, so Forescout researchers decided to launch The Memory Project in order to analyze flaws in the most popular TCP/IP stacks. This research made it possible to find the INFRA:HALT flaws.
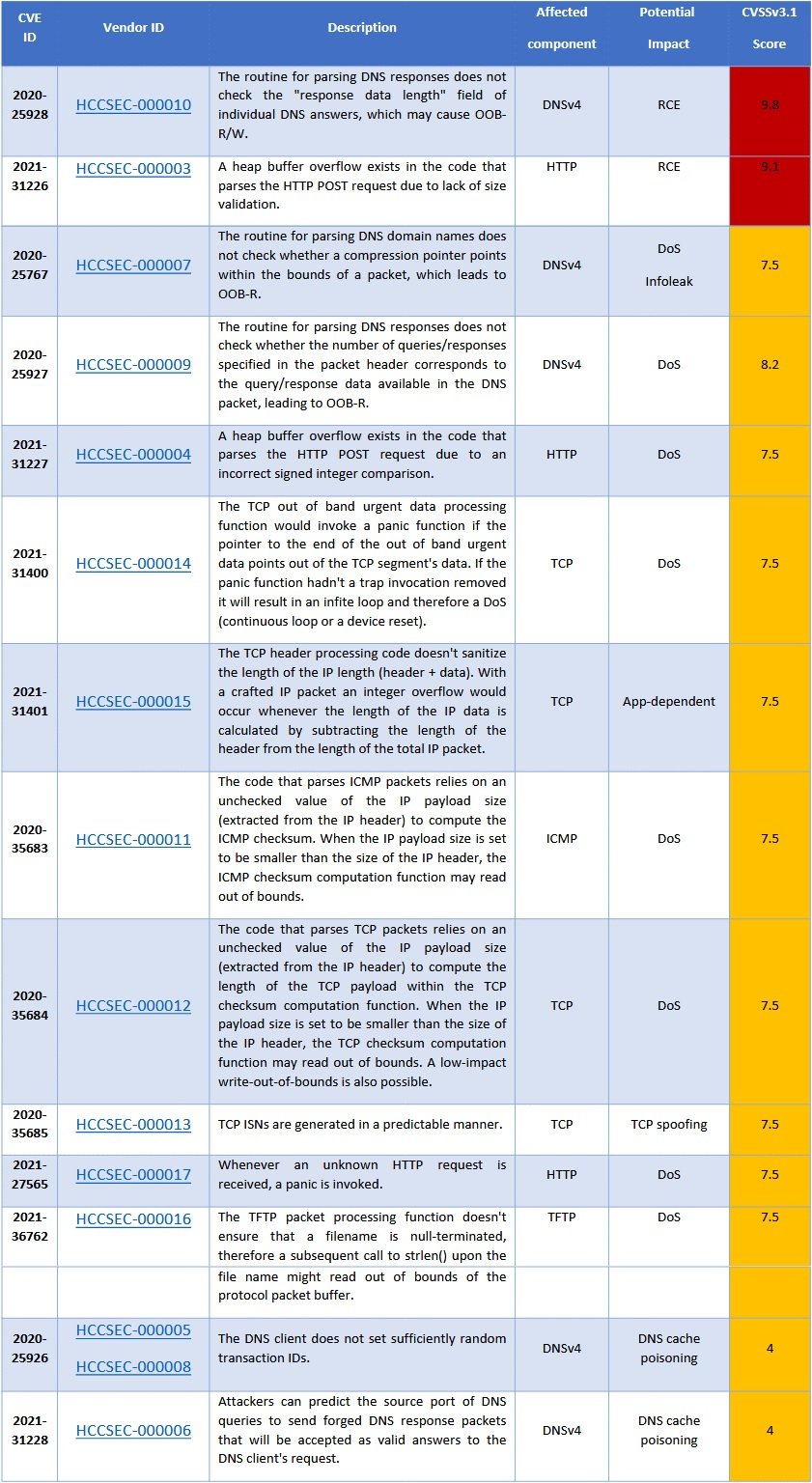
While previous research focused on finding vulnerabilities in conventional Internet of Things (IoT) devices, this time the project focused on detecting flaws in industrial deployments, including mines, pipelines, and water treatment plants. According to the report, successful exploitation of INFRA:HALT flaws enables remote code execution, denial of service (DoS) attacks, extraction of sensitive information, and even DNS cache poisoning attacks.
Experts mention that the successful exploitation of these flaws requires threat actors to gain access to an OT network, an environment separate from internal networks and whose implementation is recommended for industrial security purposes. While this is a recommended security measure, this condition does not extend to industrial devices exposed online, which can be employed as an entry point for hackers.
A network scan identified at least 6,400 OT devices potentially vulnerable to these flaws, especially by exploiting CVE-2020-25928 and CVE-2021-31226. These two vulnerabilities would allow threat actors to take control of the affected devices.
Although this scenario seems disastrous, many of the affected manufacturers have already released security patches to fix all the flaws addressed. The main disadvantage is that by the time full firmware updates are released, threat actors could have exploited these vulnerabilities in real-world scenarios. That is why users of affected deployments are encouraged to deploy the available patches as soon as possible.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
