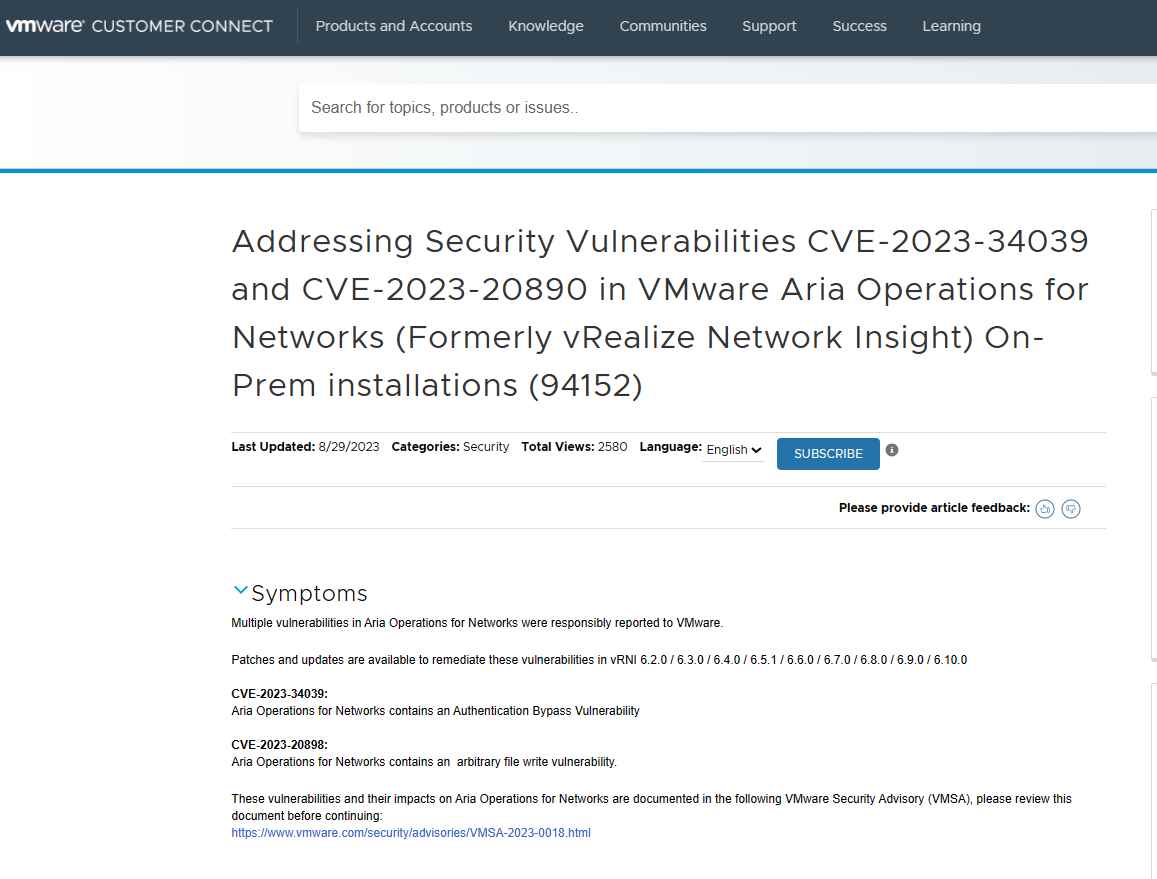
VMware has found two significant vulnerabilities, either of which might enable threat actors to circumvent authentication and get arbitrary write access on VMware Aria Operations for Networks. T
Businesses may construct a highly available, efficient, and secure infrastructure with the help of VMware Aria Operations for Networks. This infrastructure can operate effectively in many cloud settings. VMware has moved promptly to patch these security flaws after discovering them.
Vulnerability in Authentication Bypass (CVE-2023-34039)
This vulnerability occurs as a consequence of the absence of a distinct cryptographic key generation, which results in an SSH authentication bypass and ultimately allows for access to the Command Line Interface of Aria Operations for Networks. This vulnerability has been assigned a CVSS Score of 9.8, which is considered to be Critical.
Threat actors are able to carry out destructive operations on the program VMware Aria Operations for Networks after they have gained access to the Command Line Interface of that software. Despite this, there is no indication that an exploit for this vulnerability is easily exploitable.
Vulnerability in the Writing of Arbitrary Files (CVE-2023-20890)
A malicious actor with administrator capabilities to VMware Aria Operations for networks is able to take advantage of this vulnerability and abuse it. The threat actor has the ability to write files to any place they want, which might lead to the execution of remote malware. This vulnerability has been assigned a CVSS Score of 7.2, which is considered to be High.
It has been determined that the File handler is the component that is vulnerable due to this issue. There is neither information to suggest that this vulnerability is being exploited at the present time nor an exploit that is readily accessible to the public.
Versions of VMware Aria Operations for Networks that are older than 6.11 are immune to these vulnerabilities. Users of these products are strongly encouraged to review the VMware Knowledge Base article KB94152, which was published as part of the process to patch these vulnerabilities.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
