VMware published entails of multiple vulnerabilities affecting following products
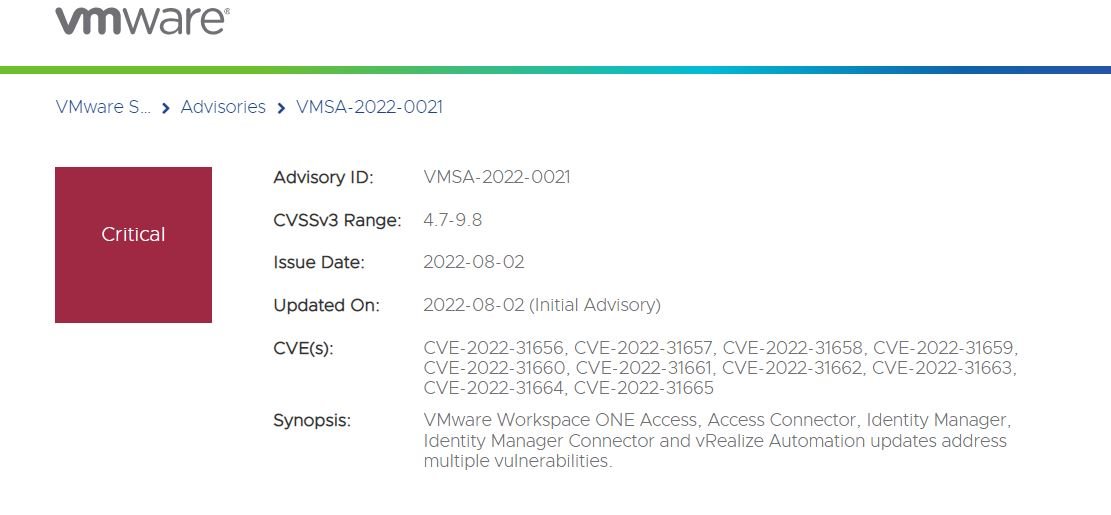
- VMware Workspace ONE Access (Access)
- VMware Workspace ONE Access Connector (Access Connector)
- VMware Identity Manager (vIDM)
- VMware Identity Manager Connector (vIDM Connector)
- VMware vRealize Automation (vRA)
- VMware Cloud Foundation
- vRealize Suite Lifecycle Manager
Following are the details of the vulnerabilities.
1. CVE-2022-31656
Authentication Bypass Vulnerability
VMware Workspace ONE Access, Identity Manager and vRealize Automation contain an authentication bypass flaw affecting local domain users. A threat actor with network access to the UI may be able to obtain administrative access without the need to authenticate.
Severity Score – CVSSv3 base score – 9.8.
Mitigation
To remediate, apply the patches available on the vendor website. Workarounds for CVE-2022-31656 have been documented in the VMware Knowledge Base articles.
2. CVE-2022-31658
JDBC Injection Remote Code Execution Vulnerability
VMware Workspace ONE Access, Identity Manager and vRealize Automation contain a remote code execution vulnerability. A threat actor with administrator and network access can trigger a remote code execution.
Severity Score – CVSSv3 base score – 8.0
Mitigation
To remediate, apply the patches available on the vendor website.
3. CVE-2022-31659
SQL injection Remote Code Execution Vulnerability
VMware Workspace ONE Access and Identity Manager contain a remote code execution vulnerability. A threat actor with administrator and network access can trigger a remote code execution.
Severity Score – CVSSv3 base score – 8.0
Mitigation
To remediate, apply the patches available on the vendor website.
4. CVE-2022-31660, CVE-2022-31661
Local Privilege Escalation Vulnerability
VMware Workspace ONE Access, Identity Manager and vRealize Automation contain two privilege escalation vulnerabilities. A threat actor with local access can escalate privileges to ‘root’.
Mitigation
To remediate, apply the patches available on the vendor website.
5. CVE-2022-31664
Local Privilege Escalation Vulnerability
VMware Workspace ONE Access, Identity Manager and vRealize Automation contain a privilege escalation vulnerability. A threat actor with local access can escalate privileges to ‘root’.
Severity Score – CVSSv3 base score – 7.8
Mitigation
To remediate, apply the patches available on the vendor website.
6. CVE-2022-31665
JDBC Injection Remote Code Execution Vulnerability
VMware Workspace ONE Access, Identity Manager and vRealize Automation contain a remote code execution vulnerability. A threat actor with administrator and network access can trigger a remote code execution.
Severity Score – CVSSv3 base score – 7.8
Mitigation
To remediate, apply the patches available on the vendor website.
7. CVE-2022-31657
URL Injection Vulnerability
VMware Workspace ONE Access and Identity Manager contain a URL injection vulnerability. A threat actor with network access may be able to redirect an authenticated user to an arbitrary domain.
Severity Score – CVSSv3 base score – 5.9
Mitigation
To remediate, apply the patches available on the vendor website.
8. CVE-2022-31662
Path traversal vulnerability
VMware Workspace ONE Access, Identity Manager, Connectors and vRealize Automation contain a path traversal vulnerability.A malicious actor with network access may be able to access arbitrary files.
Severity Score – CVSSv3 base score – 5.3
Mitigation
To remediate, apply the patches available on the vendor website.
9. CVE-2022-31663
Cross-site scripting (XSS) vulnerability
VMware Workspace ONE Access, Identity Manager and vRealize Automation contain a reflected cross-site scripting (XSS) vulnerability. Due to improper user input sanitization, a threat actor with some user interaction may be able to inject javascript code in the target user’s window.
Severity Score – CVSSv3 base score – 4.7
Mitigation
To remediate, apply the patches available on the vendor website.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
