The opensource shared file server for UNIX-like systems could put thousands of installations at risk due to a critical vulnerability allowing anyone to become a domain administrator.
Samba is a widely used open source toolkit that not only makes it easy for Linux and Unix computers to communicate with Windows networks, but also allows you to host an Active Directory domain just like Windows would without the need for Windows servers. Samba’s usefulness means that it is widely used in the Linux and Unix worlds, in the enterprise, in the cloud, and even in networking hardware such as home routers and NAS devices.
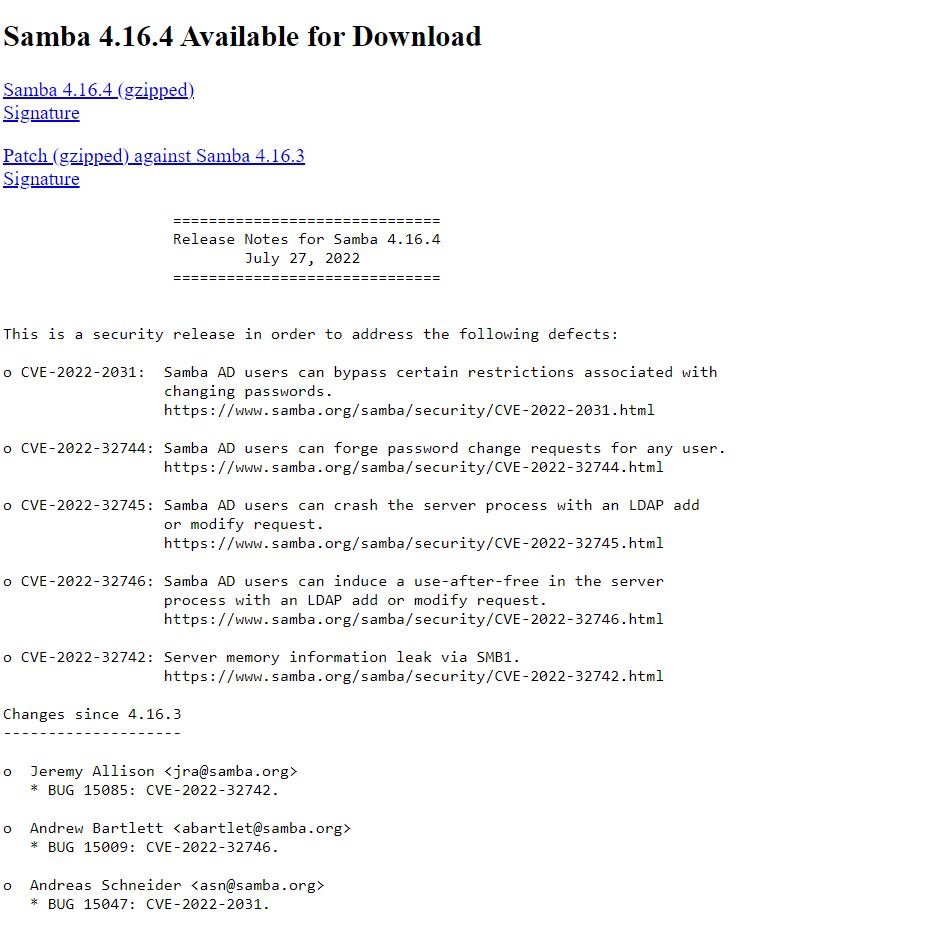
As detailed in the latest Samba release notes, there are five vulnerabilities patched, including these:
- CVE-2022-2031: Samba AD users can bypass certain restrictions associated with changing passwords.
- CVE-2022-32745 – Samba AD users can crash the server process with an LDAP add or modify request.
- CVE-2022-32746 – Samba AD users can induce a use-after-free in the server process with an LDAP add or modify request.
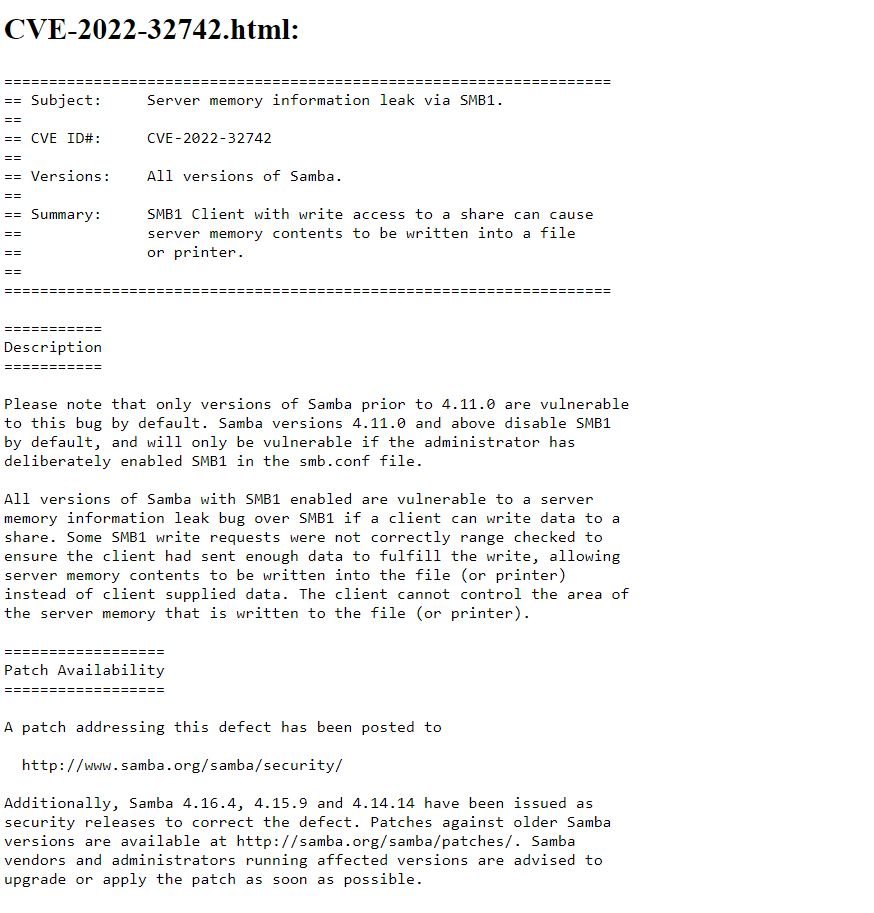
- CVE-2022-32742 – Server memory information leak over SMB1.
And this one, which is the most serious of thm, as you’ll immediately see in the flaw description:
- CVE-2022-32744: Samba Active Directory users can spoof password change requests from any user. The bug was officially reported on May 25 by the SAMBA team, and was recently fixed in the latest update on July 27. This vulnerability could be exploited by any user on the network and is critical in severity (CVSS 8.8 out of 10).
In a nutshell, exploiting this flaw would allow attackers to manipulate Samba’s password change service, known as kpasswd, through a series of failed password change attempts until finally accepting a password change request i.e password authorized by the attackers themselves.
It is a type of attack known as “PYOP”, the acronym for “Print Your Own Passport”, where after repeated failed attempts the user is asked to present an official credential that proves their identity in order to continue. This is where the attacker presents a credential that he has created himself and that the system accepts despite being false.
Patches that correct these SAMBA vulnerabilities are now available on their website. The updates you need are as follows:
- If you’re using version 4.16, update from 4.16.3 or earlier to 4.16.4
- If you’re using version 4.15, update from 4.15.8 or earlier to 4.15.9
- If you’re using version 4.14, upgrade from 4.14.13 or earlier to 4.14.14
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
