A team of researchers formed by Daniele Antonioli from the Swiss Federal Institute of Technology in Lausanne, Kasper Rasmussen from the CISPA Helmholtz Centre for Information Security in Germany and Nils Ole Tippenhauer from the University of Oxford has just revealed the finding of a vulnerability in Bluetooth, the wireless connection protocol for linking devices such as smartphones, laptops, tablets and Internet of Things (IoT) devices.
This Bluetooth Impersonation Attacks (BIAS) could affect any device with the classic version of the connection protocol, also known as Basic Rate, Enhaced Data Rate, or simply as Bluetooth Classic.
Apparently, the flaw exists because of the way devices manage the binding key (or long-term key), which is generated when two devices are paired for the first time. This key is used to derive session keys on future connections, eliminating the need to re-pair the two appliances. The flaw reported by researchers would allow a threat actor to impersonate the identity of one previously linked device to another, so it could connect without knowing the previously established long-term key.
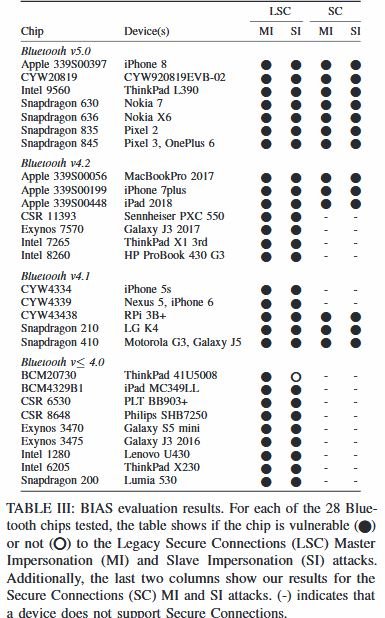
If the attack is successfully completed, hackers can take control of the target Bluetooth Classic device. Researchers tested the attack against multiple devices (smartphones, tablets, computer boards, headphones) from the world’s leading manufacturers, including Apple, Motorola, Google, Nokia, HP, Lenovo, Philips, Sennheiser, Raspberry Pi and Cypress.
Researchers notified the finding to the Bluetooth Special Interest Group (Bluetooth SIG), the organization responsible for monitoring Bluetooth standards in December 2019. Just hours ago, Bluetooth SIG released a statement informing that Bluetooth Specifietion Core was updated, preventing hackers from degrading secure protocols to the vulnerable version, thus mitigating the risk of exploitation on current devices.
In addition, manufacturers of devices with built-in Bluetooth will need to implement a firmware update in the coming months to fully resolve the issue. For now, it’s hard to track the status of updates, so we’ll have to wait some time.
This is the same computer that discovered the Bluetooth Key Negotiation Attack (KNOB) a few months ago. Experts mention that if a hacker combines both attacks, it could bypass authentication on Bluetooth-enabled devices, even those operating with a secure version of the protocol. A full technical report of the attack is available on the investigators’ official platforms.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
