Developers of the popular open source automation server software Jenkins issued a warning about a critical vulnerability on the Jetty web server whose exploitation could cause memory corruption and leaks of sensitive information.
The vulnerability, tracked as CVE-2019-17638, received a score of 9.4/10 on the Common Vulnerability Scoring System (CVSS) scale and is present in all versions between Eclipse Jetty 9.4.27.v20200227 and 9.4.29.v20200521, a Jetty wrapper, to act as an HTTP server and servlet when you start using java -jar jenkins.war. This is how Jenkins runs when using any of the installers or packages, but not when running with servlet containers like Tomcat”, it is read in the warning.
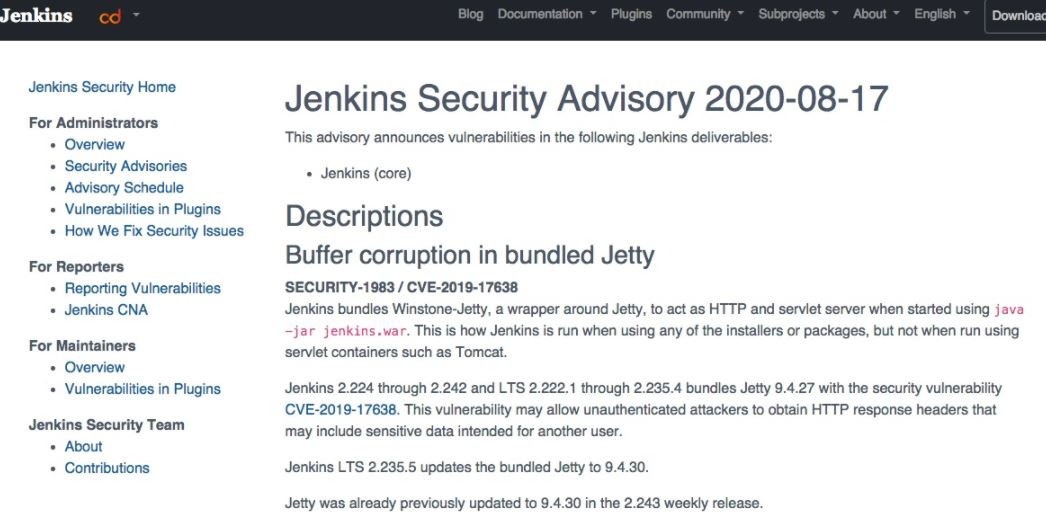
According to the report, the vulnerability would allow unauthenticated threat actors to obtain HTTP response headers that might include sensitive data intended for another user. The flaw would have been introduced in Jetty version 9.4.27, which added a function to manage large HTTP response headers and prevent buffer overflow.
“Updating fixed the buffer overflow, but the field was not aborted,” said Greg Wilkins, Project Manager Jetty. “The solution causes HTTP response headers to be published to the buffer pool twice, resulting in memory corruption and information disclosure,” Wilkins adds.
In a recently detected exploit case, memory corruption made it possible for clients to move between sessions, so they gained access to accounts because a user’s authentication cookies ended up in the hands of another user. The version of Jetty 9.4.30.v20200611, released last month, contains the necessary fixes. It is recommended that Jenkins users update vulnerable deployments to mitigate the risk of exploiting this vulnerability.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
