A number of unpatched D-Link routers were vulnerable to a serious buffer overflow and remote code execution (RCE) flaw.
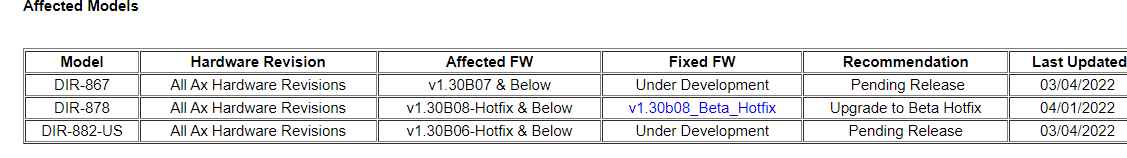
The CVE-2022-41140 flaw, with a CVSS score of 8.8, was discovered in the supported DIR-867, DIR-878, and DIR-882-US routers, although only the DIR-878 model got a patch. Submitting specifically prepared data to the lighttpd service can cause a command injection and cause the vulnerability to arise without the need for authentication. TCP port 80 is the default listening port for the lighttpd service. An adversary who can exploit the flaw might completely hijack the device.
The failure to properly validate the length of user-supplied data before transferring it to a fixed-length stack-based buffer is the cause of CVE-2022-41140.
The security vulnerability was found by an unnamed researcher participating in Trend Micro’s Zero Day Initiative, and D-Link was informed of it in February. The presence of this flaw and the fact that the first beta hotfix patch for the DIR-878 model was available have previously been verified by D-Link. According to D-Link, the updated firmware for the DIR-867 and DIR-882-US is in development. As soon as a firmware upgrade is accessible at support.dlink.com, it will be made available there.
Applying fixes and upgrades made available by the manufacturer is strongly advised for users of D-Link devices in order to reduce potential risks.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
