On December 6th, 2022, CloudSEK announced that the firm had been the target of a cyber attack. The internal investigation team discovered throughout the course of their investigation into the primary cause of the event that the threat actor acquired access to a employee’s Jira account by leveraging Jira session cookies that were contained in stealer logs that were being sold on the dark web.
After conducting additional research, it was discovered that cookies are not invalidated for Atlassian products (Jira, Confluence, and BitBucket), even if the password is changed and 2FA (Two-factor Authentication) is enabled. The cookie validity period is thirty days, so even if the password is changed, the cookies will remain valid. They will only become invalid after the user signs out, or after thirty days have passed.
We have sent this information to Atlassian, and they have recognized that there is a problem and are attempting to find a solution to it.
Researchers from CloudSEK have discovered that this vulnerability allows an attacker to gain control of the Jira accounts of hundreds of businesses. According to our findings, there are more than 1,282,859 compromised machines and 16,201 Jira cookies available for purchase on markets located on the dark web. In addition, over 2,937 hacked machines and 246 sets of Jira credentials have been made public during the last month alone. Within the last three months, we have found at least one computer belonging to a Fortune 1000 organization that has been hacked. This just takes into account their core domains and does not take into account their subsidiaries.
Atlassian products are utilized extensively all around the world. The company has more than 10 million users spread out over 180,000 businesses, including 83 percent of the Fortune 500. Furthermore, malicious actors are aggressively taking use of this vulnerability to hack business Jira accounts.
Even with two-factor authentication (2FA), stolen Atlassian cookies may lead to unauthorized account access.
Even if the password is changed and two-factor authentication is turned on, the analysis carried out by CloudSEK reveals that cookies associated with Atlassian products continue to be used for a period of thirty days. Therefore, threat actors may use stolen cookies to restore Jira, Confluence, Trello, or BitBucket sessions even if they do not have access to the MFA OTP or PIN. The cookies become invalid either 30 days after being set or when the user signs out of their account, whichever comes first.
Because tokens are necessary to use this and get access to systems, it is a recognized concern, but most businesses do not consider it to be within the scope of security reporting. This is because tokens are needed. There are more vulnerabilities, such as XSS, that may be exploited to get tokens, and security reports must account for these vulnerabilities. In spite of this, the use of social engineering is not permitted during Bug Bounty engagements; nonetheless, exploiting malware and dumping information such as cookies both necessitate the use of social engineering.
On the other hand, it is not an overly difficult task for threat actors to get these tokens at this point in time. Theft of cookies has grown routine as a result of the surge in the number of efforts to infiltrate devices, breaches, and password dumps. And one can simply search for a corporation, purchase their logs, and identify suitable tokens in order to obtain access to their internal systems. In addition, cookies can be bought, and there is a market for them.
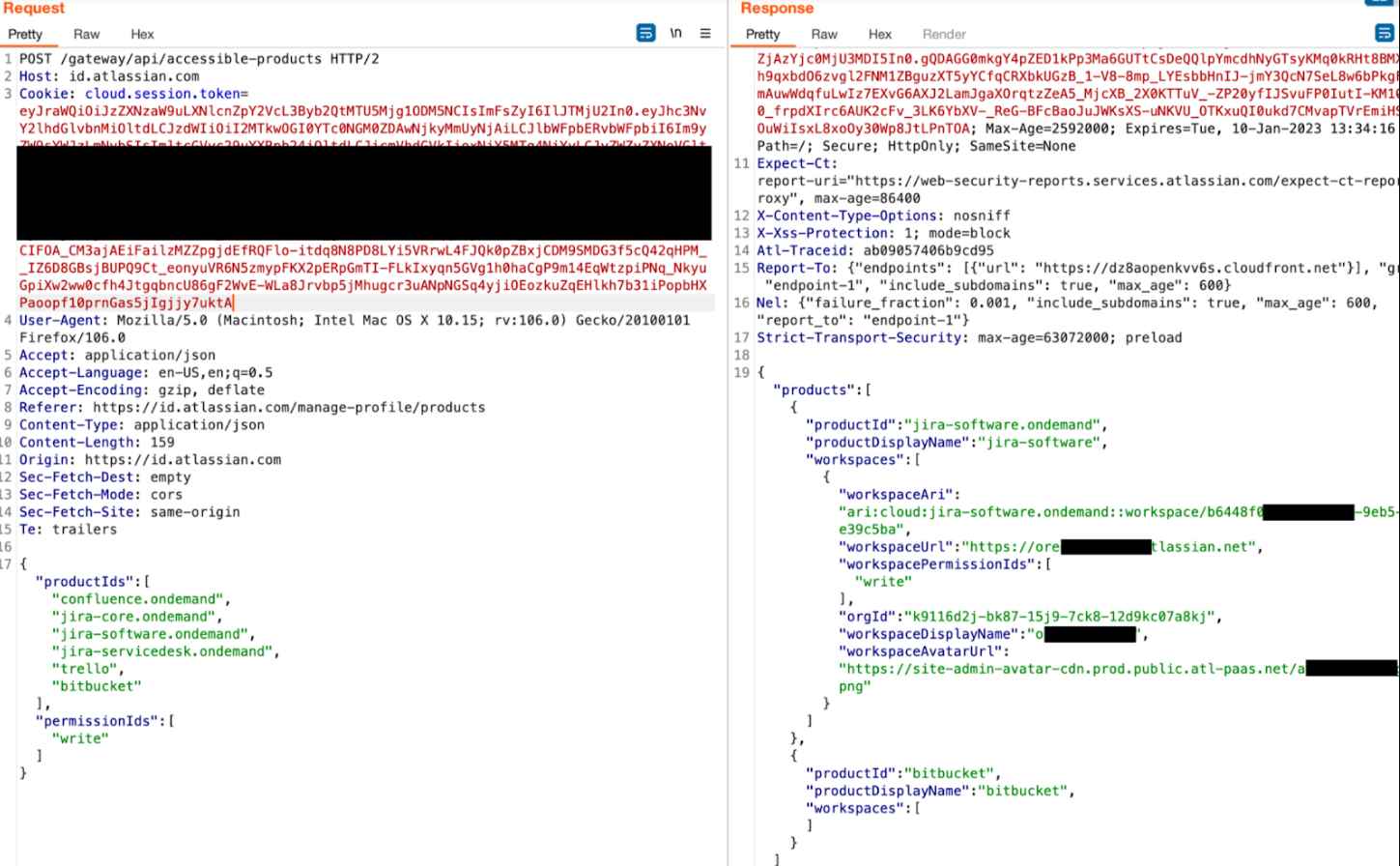
To hijack a session using Atlassian products, all that is necessary is a single JSON web token (JWT), which is denoted by the cloud.session.token property. JSON Web Tokens, or JWT tokens, issued by Atlassian include the user’s email address encoded inside the cookie. As a result, it is simple to ascertain whose user the cookie should be associated with.
Interventions to Reduce the Impact
In the sake of security, personnel should be regularly reminded to log out of critical apps.
Until a remedy is published by atlassian, you should reduce the amount of time that Atlassian products are allowed to sit idle by accessing the Security > Authentication rules area on admin.atlassian.com.
Implement idle-session timeout to ensure re-logins
Maintain vigilance on cybercrime forums in search of the most recent strategies used by threat actors.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
