Within the Linux kernel, a security flaw that has been given the identifier CVE-2023-2002 has been discovered; this flaw poses a severe threat to computer systems that depend on Bluetooth connectivity. By taking advantage of an incorrect permission check in the Bluetooth subsystem, this exploit gives remote attackers who have already been authenticated the ability to execute arbitrary instructions on the machine that is being impacted.
When the Bluetooth subsystem of the Linux kernel handles ioctl system calls of HCI sockets, there is not enough of a check to ensure that permissions are granted. This leaves the system susceptible to a vulnerability. This omission makes it possible for tasks that do not have the required CAP_NET_ADMIN capability to designate HCI sockets as trustworthy, which in turn makes it possible for illegal management commands to be executed. The vulnerability may be exploited with the mere existence of a group of setuid applications that are frequently used (for example, su and sudo).
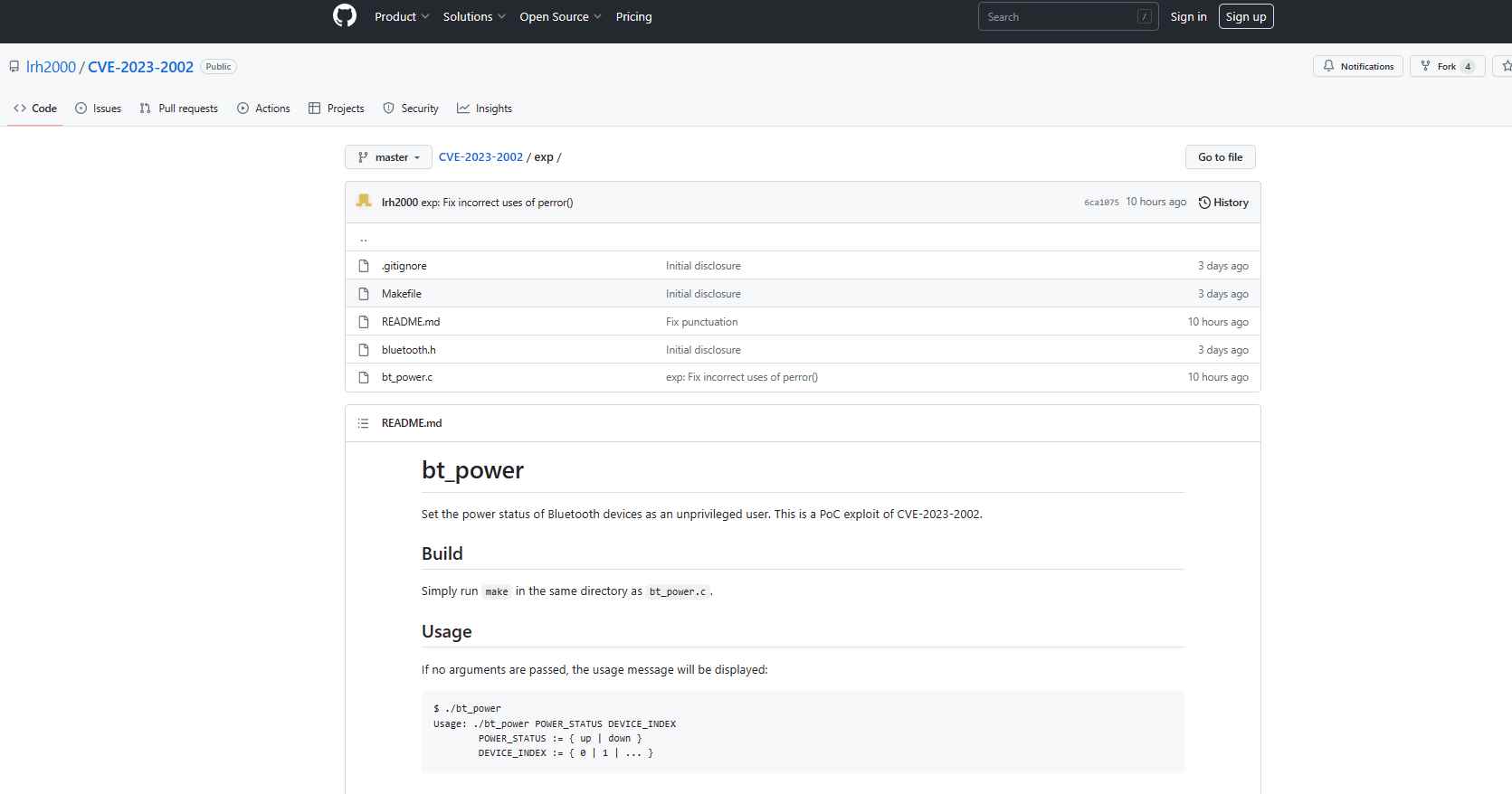
An adversary may exploit this vulnerability by submitting a specially constructed request to the system that is the target of the attack. This will provide the adversary the ability to carry out arbitrary management commands. On GitHub, an attack known as a proof-of-concept (PoC) has been made public. This vulnerability is able to change the power status of Bluetooth devices.
If CVE-2023-2002 is exploited successfully on the system in question, the confidentiality, integrity, and availability of Bluetooth communication may all be put at risk. Even if the Bluetooth service is deactivated or not installed, an attacker may still connect the controller with malicious devices and use it to perform attacks. In addition to this, they are able to block certain devices from pairing with one another and gaining access to sensitive information, such as OOB data.
The major security flaw known as CVE-2023-2002 leaves Linux systems that use Bluetooth connectivity open to the risk of being attacked. Users are strongly encouraged to install any patches that are now available and to put the mitigation techniques that have been advised into action in order to protect their systems from being exploited. To protect the system against vulnerabilities of this kind in the future, developers should also concentrate on strengthening the Linux kernel and the setuid applications.
The linux-bluetooth mailing list has been notified of the existence of a patch that addresses this issue. The function capable() is replaced by sk_capable() in the patch. sk_capable() examines the capabilities of the socket opener in addition to the capabilities of the current job. One of the other patches under consideration would strengthen the ioctl processing logic. Users may temporarily reduce the effect of the vulnerability by blocking Bluetooth devices using rfkill as a solution. This stops the devices from being powered up, which considerably lessens the impact of the issue.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
