The malware was given the name Mélofée by the French cybersecurity company ExaTrack after they discovered three instances of the previously disclosed harmful software that date back to the beginning of 2022.
One of the artifacts is intended to drop a kernel-mode rootkit that is based on an open source project known as Reptile. This rootkit was meant to steal sensitive information. The business said in a report that “According to the vermagic information, it is built for a kernel version 5.10.112-108.499.amzn2.x86 64.” “The rootkit only comes with a few characteristics, the most important of which is the installation of a hook specifically made for concealing itself.”
It is believed that shell commands are used to deliver both the implant and the rootkit. These shell instructions are reported to download an installer and a bespoke binary package from a remote site. The binary package is sent as a parameter to the installer, after which the rootkit and a server implant module that is during development at the moment are extracted from the package.
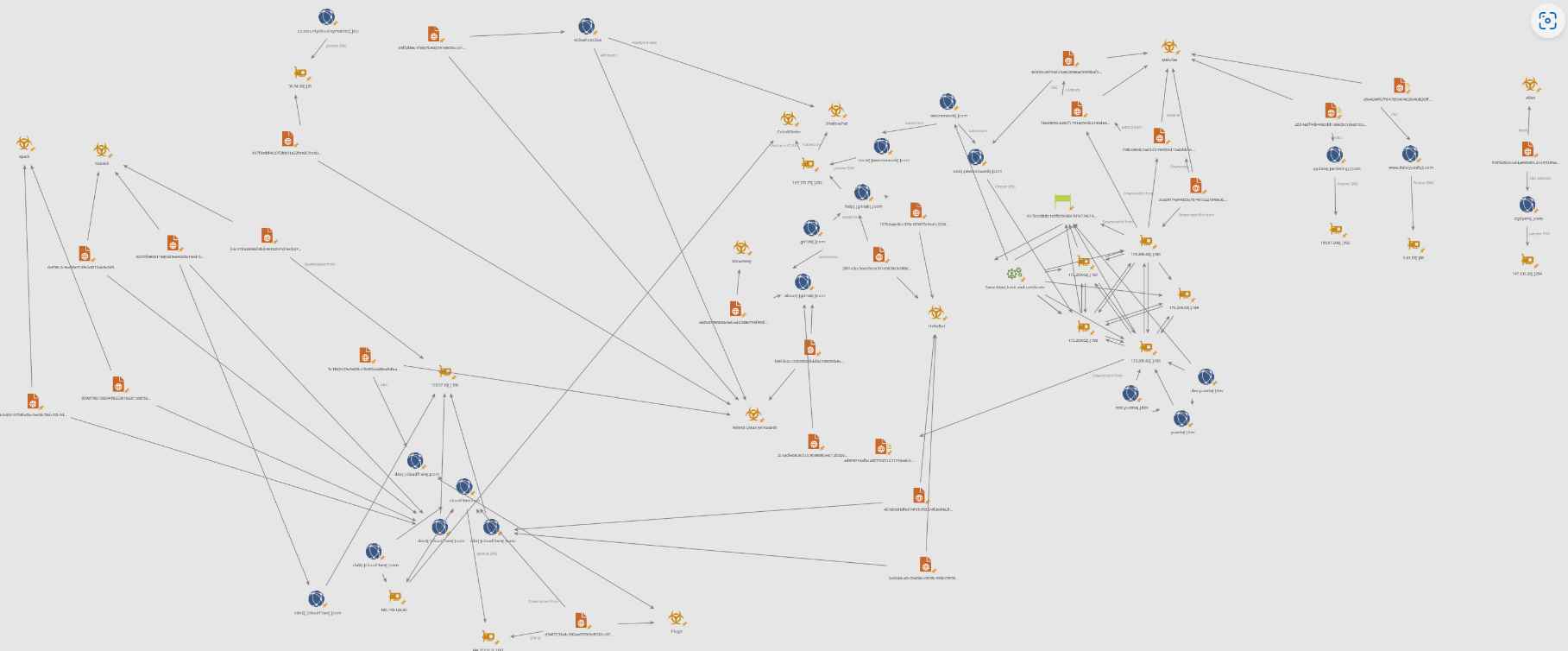
It is possible for Mélofée to communicate with a remote server and receive instructions that enable it to carry out file operations, create sockets, launch a shell, and execute arbitrary commands, just like other backdoors of its kind. These features allow Mélofée to be functionally equivalent to other backdoors of its kind. Infrastructure overlaps with other organizations, including APT41 (also known as Winnti) and Earth Berberoka, are the source of the malware’s connections to China (aka GamblingPuppet).
From at least the year 2020, a state-sponsored actor known as Earth Berberoka has mostly targeted gambling websites in China employing multi-platform malware such as HelloBot and Pupy RAT. This actor goes by the moniker Earth Berberoka. Trend Micro claims that certain samples of the Python-based Pupy RAT have been hidden by employing the Reptile rootkit.
A second implant with the codename AlienReverse was also found by ExaTrack. Like Mélofée, this implant uses freely accessible software such as EarthWorm and socks proxy. Both of these implants have significant similarities in their programming. According to a statement released by the business, “The Mélofée implant family is another weapon in the armory of Chinese state sponsored attackers, which exhibit continual innovation and improvement.”
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
