Experts from Talos, Cisco’s threat intelligence and research team, have reported the finding of two vulnerabilities in the Nitro Pro PDF editor. According to the report, these flaws could be exploited by threat actors to execute remote code on the affected hosts.
Nitro Pro is a software solution designed to read, edit, sign and store PDF files that is part of Nitro Software’s enterprise toolset; according to data provided by the company, its solutions are currently employed by more than 10 thousand organizations worldwide.
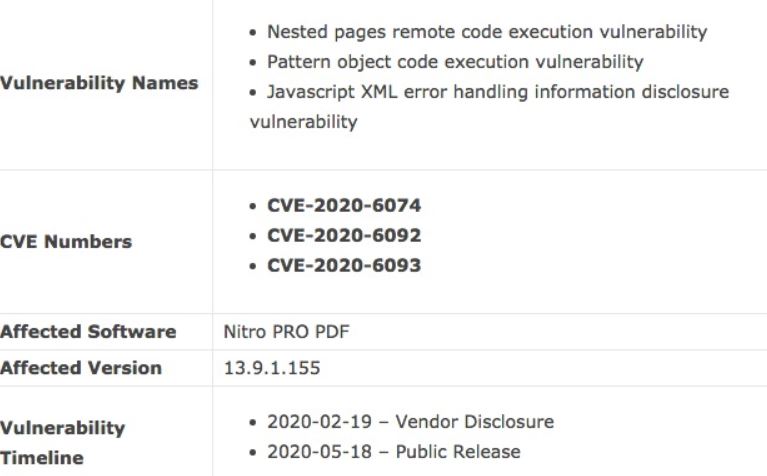
Cisco Talos researchers reported the identification of three vulnerabilities in the company’s PDF application, noting that exploiting two of these flaws could lead to remote code execution scenarios. These two vulnerabilities received a score of 8.8/10 on the Common Vulnerability Scoring System (CVSS) scale.
The first of these vulnerabilities, tracked as CVE-2020-6074, was discovered in the Nitro Pro PDF analyzer. A malicious hacker wishing to exploit the flaw must send the victim a specially designed PDF document to activate a use-after-free condition and get arbitrary code executed.
On the other hand, the second security flaw, tracked as CVE-2020-6092, exists because of the way Nitro Pro scans Pattern objects. Threat actors could create malicious PDF files and trick the victim into triggering an integer overflow, leading to remote code execution.
During their research, Cisco experts discovered an additional information disclosure vulnerability via Nitro Pro. This flaw, TRACKED as CVE-2020-6093, appears to be related to how the application handles XML errors, and received a score of 6.5/10 on the CVSS scale, so it is considered a medium severity error.
Acorde al informe, para explotar esta vulnerabilidad, un actor de amenazas sólo tendría que entregar al usuario objetivo un documento PDF especialmente diseñado. Si la víctima abre el documento, el atacante obtendría acceso de memoria no inicializado, lo que podría conducir a escenarios de filtración de información.
All three vulnerabilities were found in Nitro Pro version 13.9.1.155 and were reported to developers last February with adherence to the procedures established by the cybersecurity community. In response, Nitro Software recognized the reports and pledged to release a security update that would correct these flaws. The update was released in early May, so users of vulnerable deployments are advised to upgrade immediately to mitigate the risk of exploitation.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
