Cisco security teams announced the correction of an authentication bypass vulnerability in Enterprise NFV Infrastructure Software (NFVIS). Tracked as CVE-2021-34746, this flaw resides in the TACACS+AAA system of the affected product, designed for the virtualization of network services.
According to the report, the flaw exists due to incorrect input validation provided by the user passed to an authentication script during logon. This error would allow unauthenticated remote threat actors to log on to an out-of-date device with administrator privileges.
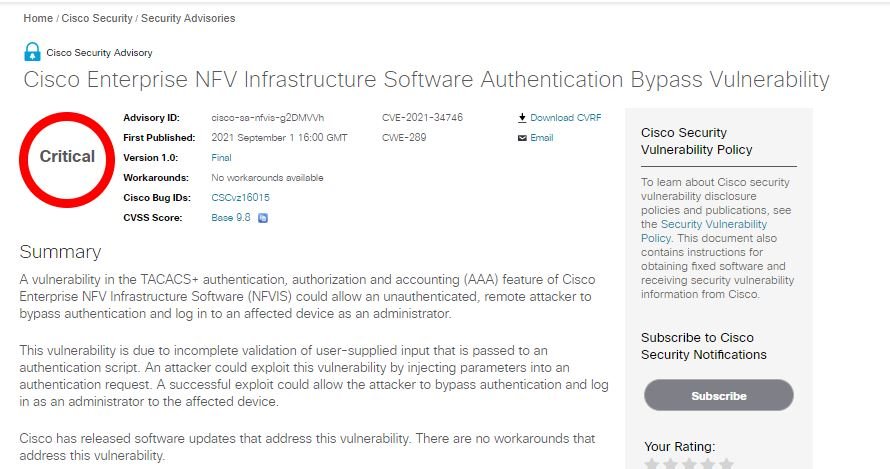
According to Cisco’s report, malicious hackers could exploit the flaw by injecting parameters into an authentication request: “Successful exploitation would allow attackers to evade authentication and access the affected system as an administrator,” the experts add.
It is worth mentioning that enterprise NFVIS implementations are affected by this flaw as long as the TACACS external authentication method is enabled on an affected device. To verify whether a device is vulnerable to CVE-2021-34746 exploitation, administrators should only check if the TACACS external authentication feature is enabled.
For this, only one command line is enough. Apply the show running-config tacacs-server command, which should display the message “No entries found” when TACACS is disabled.
Users can also use the GUI by going to Settings – Host – Security – User and Roles to check if the feature appears under External Authentication. The company notes that, at the moment, no workarounds are known, so affected users will need to update to v4.6.1 forcibly to address the issue.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
