A web application security researcher reported a cross-site script vulnerability affecting the McDonald’s website (mcdonalds.com) that compromised the information on the website and its users. Before we explain the researcher’s finding, let’s see what this security flaw is all about.
What is Cross-Site Scripting (XSS)?
A cross-site script (usually abbreviated as XSS) is a vulnerability that allows a hacker to compromise user interactions with the vulnerable web application (in this case, the McDonald’s site). By exploiting these security flaws, attackers can bypass the Same Origin Policy (SOP), which prevents loading documents or scripts from third-party sources on any website; thanks to this, hackers can perform actions as legitimate users and access the information processed by the target web application. In addition, if the attacker has privileged access to the application, they could gain full control over its functions and data.
How the XSS vulnerability works
An XSS attack works by manipulating a vulnerable website, forcing the delivery of malicious JavaScript code to the victim. When the malicious code runs in the victim’s browser, the attacker could completely compromise interactions with the app, as mentioned by web application security specialists.
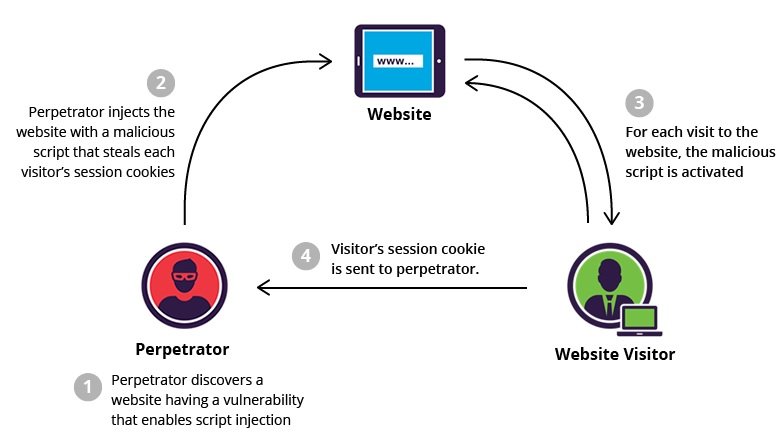
How can the XSS vulnerability be used?
This attack allows hackers to perform various malicious activities, such as:
- User interactions’ impersonation
- Access to any user information
- Capture the user’s login credentials
- Alteration of the target website
- Trojan injection via websites
Impact of an XSS attack
The real impact of these attacks depends on the compromised application, its capabilities, and stored data. For example, a brochureware application, where users are anonymous and the information is public, would not suffer from major drawbacks. On the other hand, applications capable of storing sensitive information (mobile banking apps, for example) would suffer disastrous consequences in the event of an XSS attack.
The McDonald’s case
The web application security expert known as amlnspqr reported the flaw on the fast food chain website through the responsible vulnerability disclosure platform openbugbounyt.org. This XSS flaw posed a serious potential for danger to the company and users of the affected website.
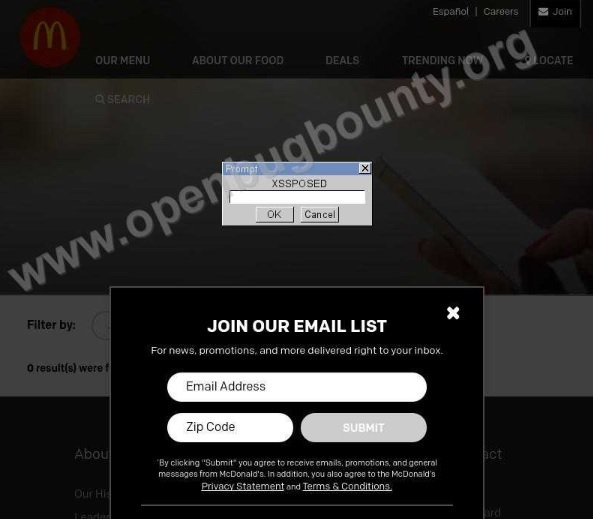
The company has already received the report. As an OpenBugBounty protocol, operators of the affected website should contact the report manager for further reporting. Technical details of the report will be disclosed as soon as the vulnerability is corrected.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
