The US Cybersecurity and Infrastructure Security Agency (CISA) posted 10 new actively exploited vulnerabilities (KEV) to its Vulnerability Catalog, one of which is a highly significant security issue impacting security products. automated manufacturing from Delta Electronics.
DOPSoft 2 is impacted by the vulnerability, identified as CVE-2021-38406 (CVSS score: 7.8). This vulnerability can enable the execution of arbitrary code with a successful attack.
“Delta Electronics DOPSoft 2 lacks proper validation of user-supplied data when parsing specific project files (improper input validation), resulting in out-of-bounds writing that allows code execution”
It’s important to remember that CVE-2021-38406 was first made public as part of an Industrial Control Systems (ICS) warning that was released in September 2021. The CISA warns that the “affected product has reached the end of its useful life and should be unplugged if it is still in use” since there are no updates to address the vulnerability.
Web shells, cryptocurrency miners, botnets, remote access trojans (RATs), brokers initial access (IABs), and eventually ransomware are often used in a precise order for the exploitation of these assaults.
The list of actively exploited bugs now includes:
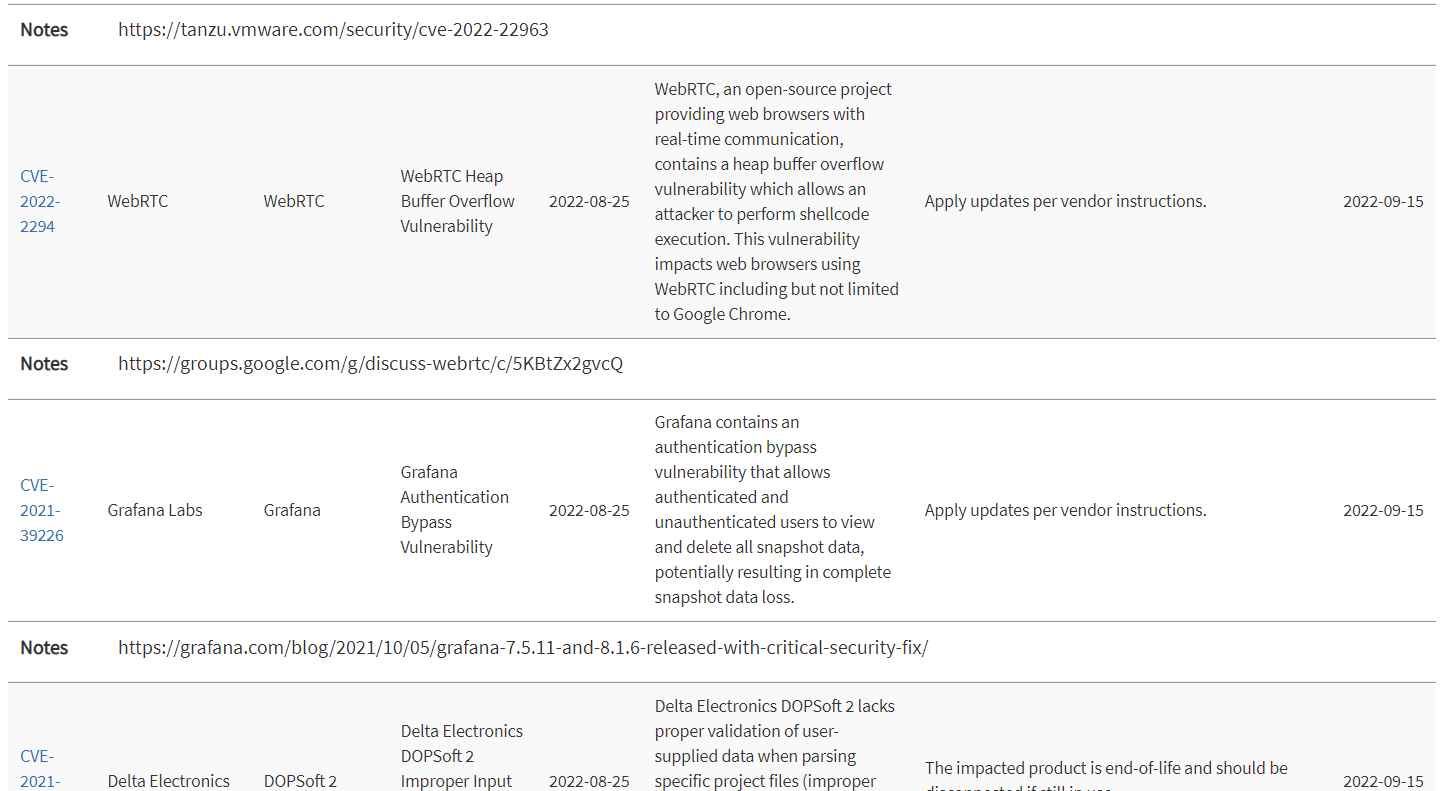
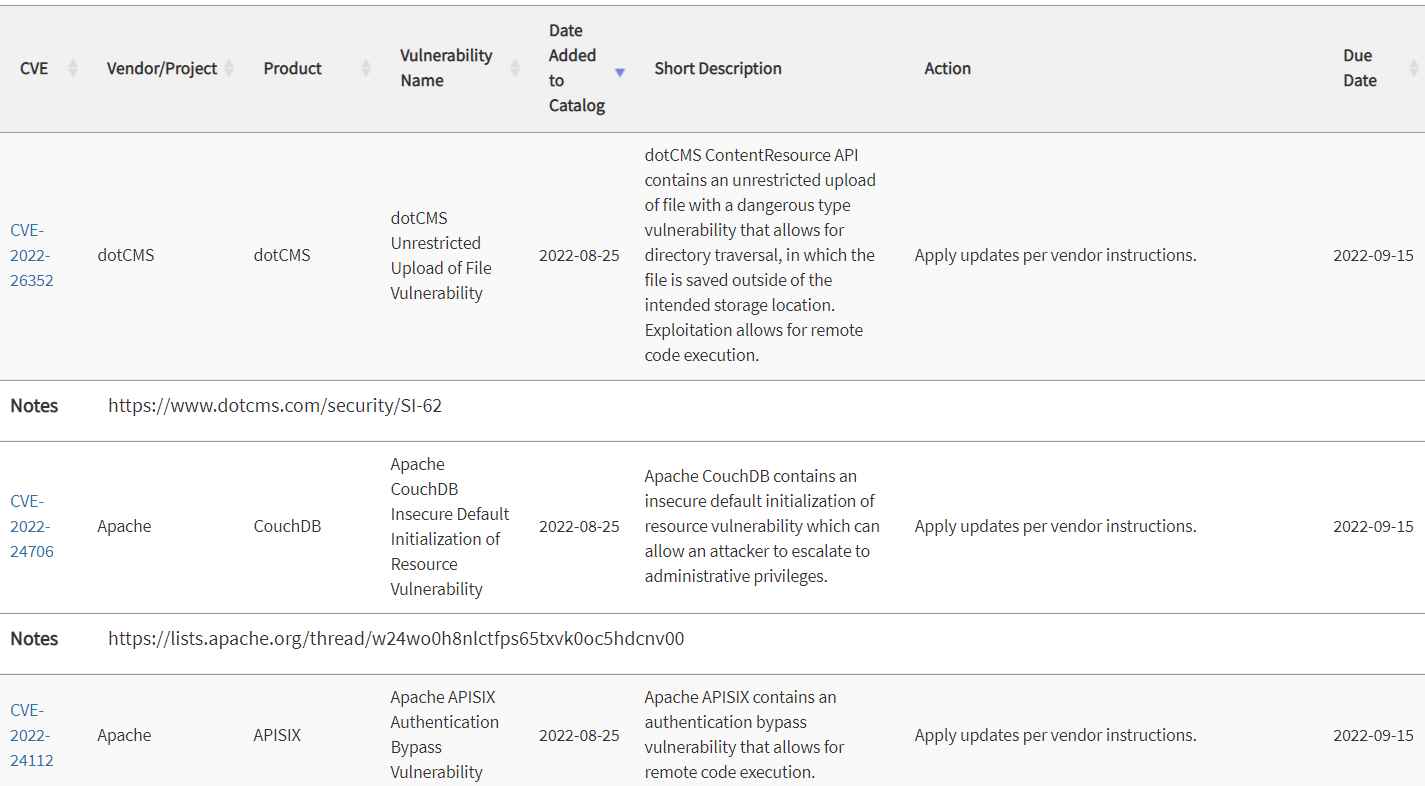
- CVE-2022-26352 – dotCMS Unrestricted File
- CVE-2022-24706 Default Resource Initialization Vulnerability
- CVE-2022-24112 – Apache APISIX Authentication
- CVE-2022-22963 – VMware Tanzu Spring Cloud Function Remote Code Execution
- CVE-2022-2294 – WebRTC Buffer Overflow Vulnerability
- CVE-2021 -39226 – Grafana authentication bypass vulnerability
- CVE-2020-36193 – PEAR Archive_Tar bad link resolution vulnerability
- CVE-2020-28949 – Rogue data deserialization vulnerability in PEAR Archive_Tar
CVE-2021-31010 (CVSS score: 7.5), a deserialization flaw in Apple’s Core Telephony that may be exploited to get beyond sandbox constraints, is another extremely serious bug that has been added to the KEV Catalog.
The flaw was resolved by the tech giant in September 2021 releases of iOS 12.5.5, iOS 14.8, iPadOS 14.8, macOS Big Sur 11.6 (including security update 2021-005 Catalina), and watchOS 7.6.2.
The September update is significant for resolving CVE-2021-30858 and CVE-2021-30860, both of which were exploited by NSO Group, the company behind the infamous Pegasus trojan, to get beyond the operating system’s security measures.This increases the potential that CVE-2021-31010 and the two previously described issues were combined in an attack chain to get outside the sandbox and execute arbitrary code.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
