In its latest security alert, the Cybersecurity and Infrastructure Security Agency (CISA) has compiled a list of the most popular free security tools and services, which can be used by federal agencies in the U.S. to increase their security measures.
Available in a repository, the list includes tools and services provided by CISA, as well as open source software used in the public and private sectors by the entire cybersecurity community. The Agency also plans to implement a process so that organizations that have developed these tools continue to collaborate with each other for their maintenance and improvement.
CISA claims to apply neutral principles and criteria for the consideration of new tools to be included in the repository, in addition to the fact that the Agency has repeatedly stated that it does not endorse specific commercial products or services. In other words, CISA has no business agreements with any commercial firm dedicated to software development.
The tools and services recommended in the CISA repository are selected and classified according to some criteria established by cybersecurity specialists, including:
- Reduced likelihood of a harmful cyber incident
- Early detection of malicious activity quickly
- Effective response to confirmed incidents
- Maximizing resilience
Below are some examples of tools available in this repository:
Reduce likelihood of a harmful cyber incident
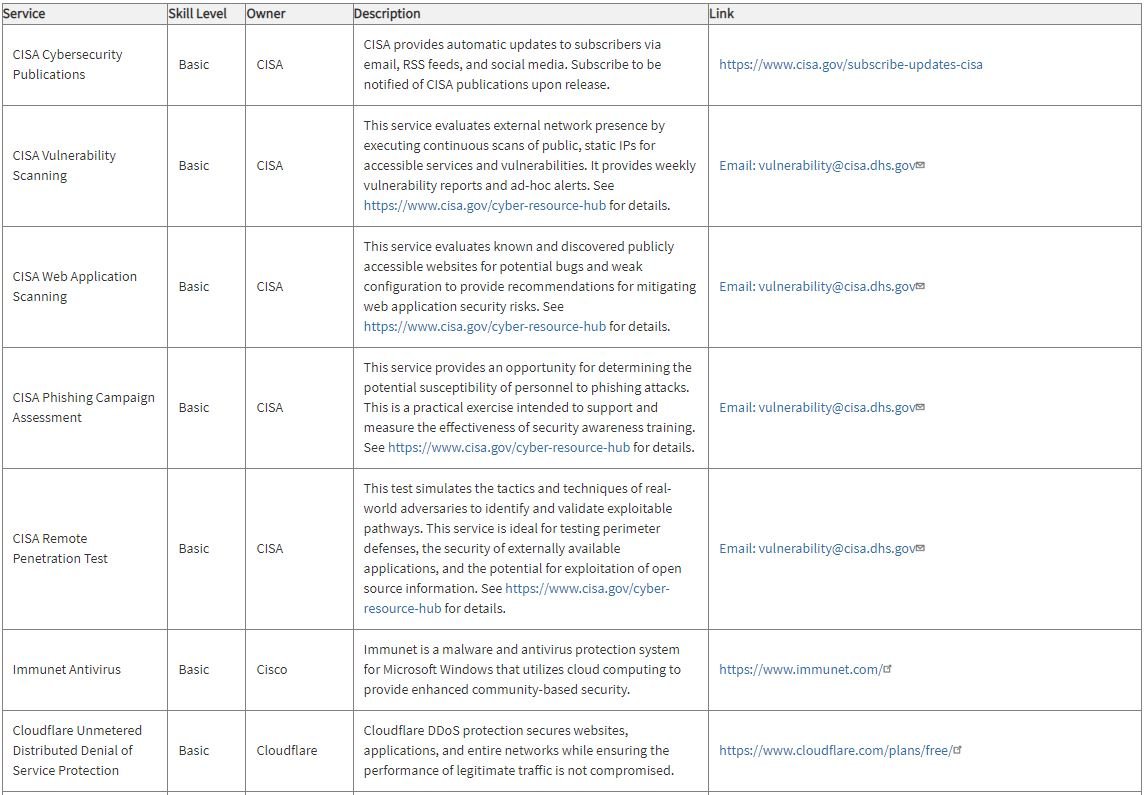
Early detection of malicious activity quickly
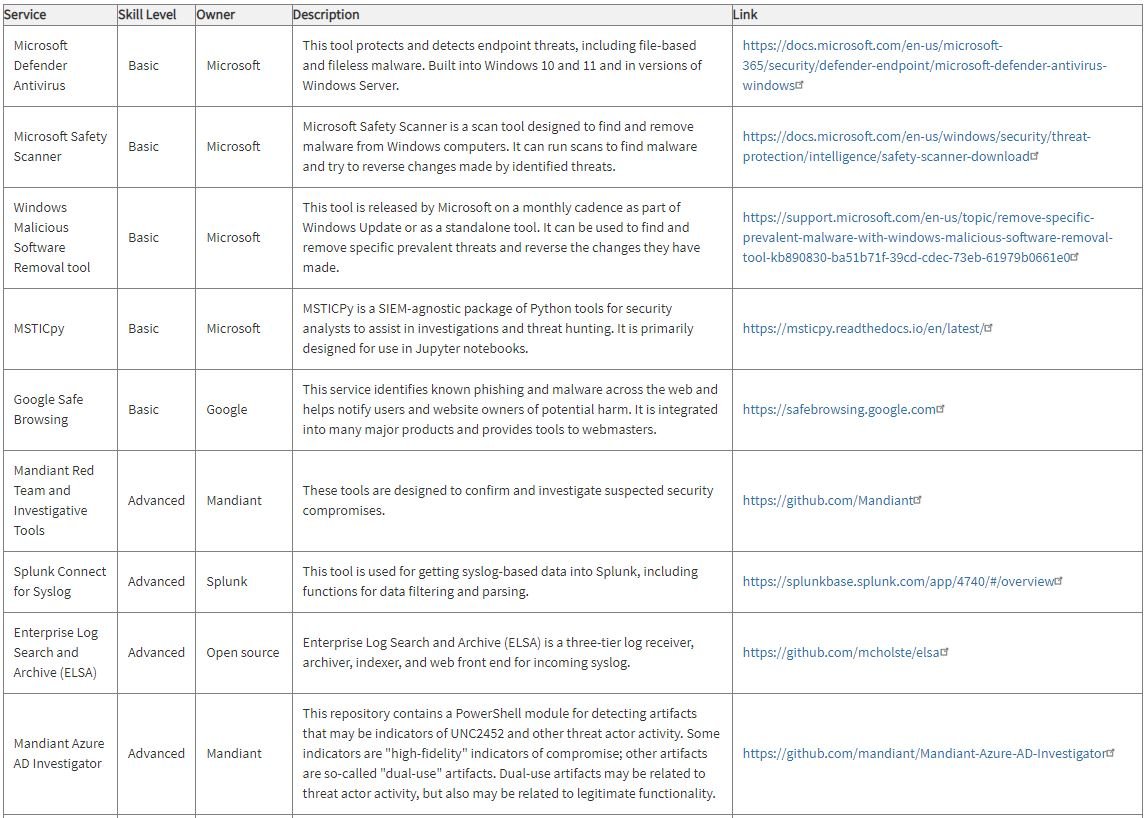
Effective response to confirmed incidents
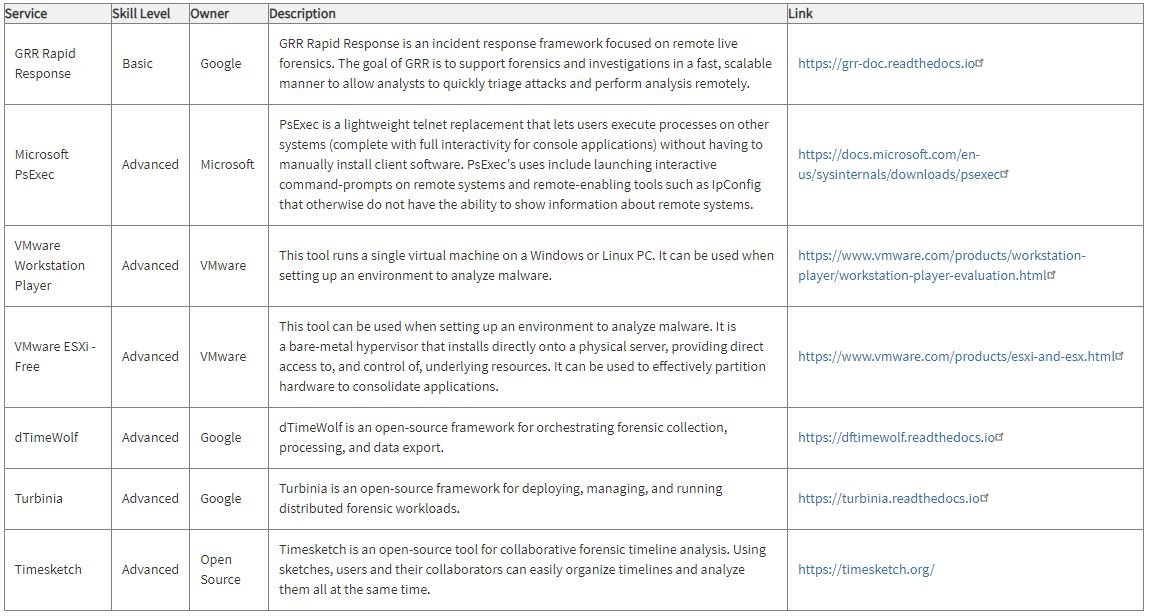
Maximizing resilience
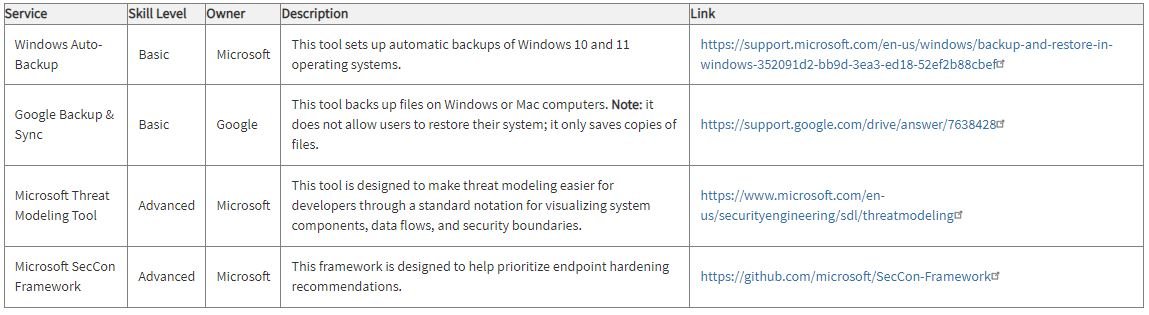
Fundamental security mechanisms
In addition to the use of these solutions, CISA recommends organizations take standardized security measures in order to implement a reliable, stable, and responsive cybersecurity environment to any attack incident. Among the measures recommended by the Agency are:
- Fix known vulnerabilities: Organizations are encouraged to consult the CISA Known Exploited Vulnerabilities Catalog to keep their software always up to date to the latest version available in order to prevent the exploitation of known security flaws in advance
- Multi-factor authentication: It is recommended to enable this security mechanism whenever possible, as it adds an additional layer of security for online accounts and data linked to them. By enabling multi-factor authentication to email accounts and similar resources, you prevent the abuse of leaked passwords in data breach incidents to access protected platforms, as entering a username and password will not be enough to access your organization’s sensitive information.
- Eliminate risky practices: Bad practices in many organizations are the leading cause of cybersecurity incidents. Tasks such as replacing discontinued software, modifying default passwords, or using additional security tools will strengthen cyber-attack protection in your organization
- Use of CISA Cyber Hygiene Vulnerability Scanning: Organizations can subscribe to this automated service in order to evaluate their systems and apply relevant security measures. CISA performs a detailed vulnerability scan and delivers a weekly report to subscribers, making it a process that doesn’t even impact the operations of user organizations.
- Stuff Off Search (S.O.S.): While combating the riskiest security threats, system administrators may overlook lesser-known risks. By implementing Stuff Off Search, attack surfaces on the Internet become visible and it becomes easier to contain a potential attack.
Organizations are recommended to implement all these measures and use the tools recommended by CISA in order to prevent the most well-known security risks, since a preventive approach gives an advantage against most hacking incidents and strengthens the security infrastructure in public and private organizations.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
