Over one million different attempts have been made to get into a popular WordPress plugin over the last several days, according to experts that study security.
According to Wordfence, the attacks started on July 14 and continued over the weekend, reaching their peak on July 16 with 1.3 million strikes against 157,000 sites. According to the information provided by the security vendor, the attacks took use of a major vulnerability in the WooCommerce Payments plugin (CVE-2023-28121), which has a CVSS score of 9.8.
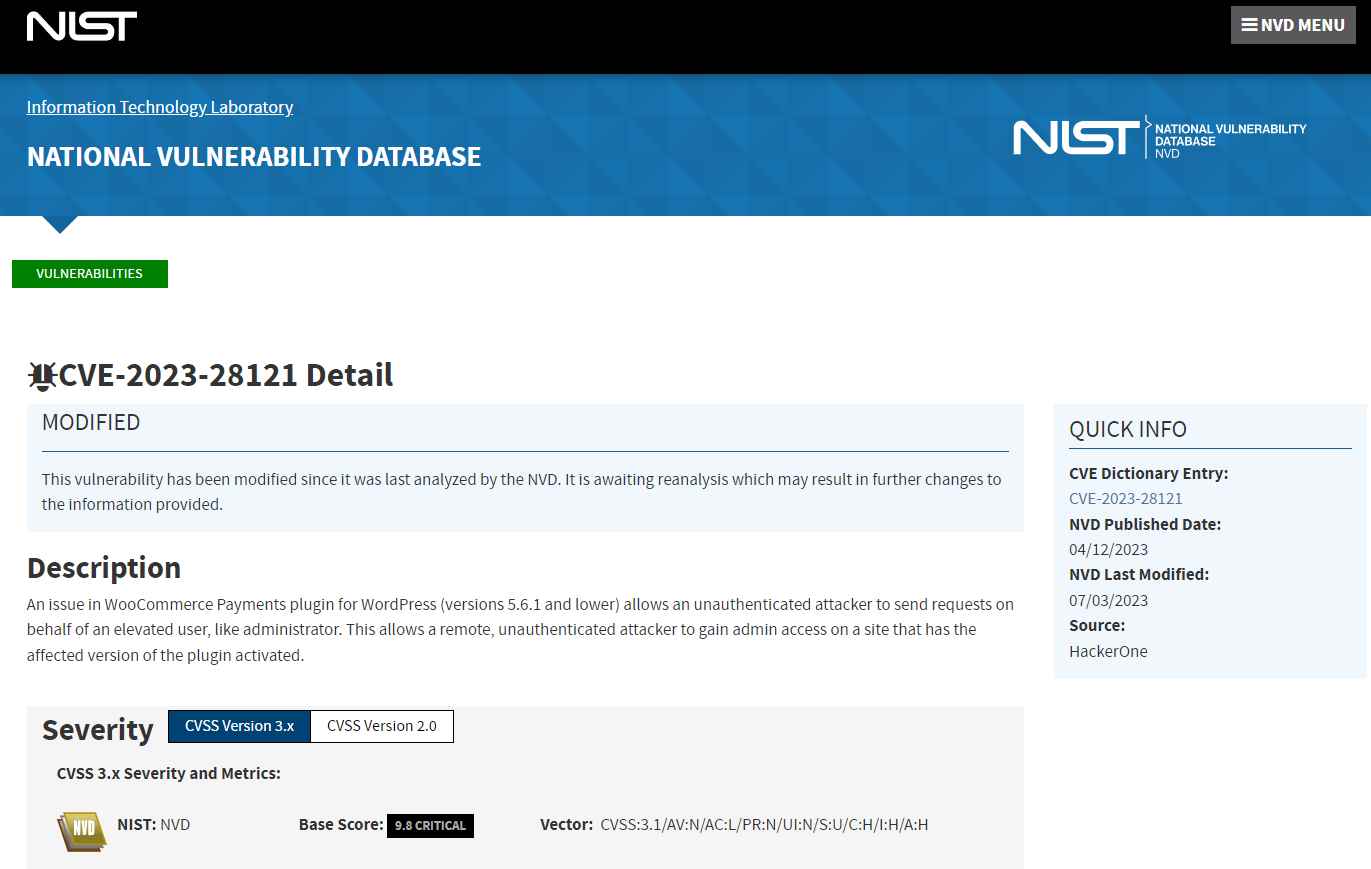
It is estimated that there are around 600,000 installations of the WooCommerce Payments plugin, which gives customers the ability to take credit card payments in online businesses powered by WooCommerce.
If this vulnerability were to be exploited, it would make it possible for a remote attacker to impersonate an administrator and gain control of a WordPress site that was affected by the issue. According to Wordfence, it has been seen that threat actors are trying to exploit their admin rights in order to remotely install the WP Console plugin on websites that have been compromised.
On March 23, the makers of the WooCommerce Payments plugin released version 5.6.2, which corrected a vulnerability that had been discovered. Versions 4.8.0 and later are affected by this issue.
On the other hand, security researchers working for Patchstack have found that the widely used plugin has a flaw that makes it susceptible to the CVE-2023-33999 vulnerability. The WordPress community has been alarmed by the discovery of a security flaw in the Freemius WordPress SDK (versions 2.5.9 and earlier). This flaw may potentially affect the over 7 million websites that depend on the hundreds of plugins and themes that utilize this SDK.
The Freemius WordPress SDK is a software development kit (SDK) that is an essential component of the Freemius managed eCommerce platform, which is widely regarded as the industry standard for the sale of WordPress plugins and themes. It is a software library that combines the Freemius services with the WordPress plugins and themes products in an efficient and effective manner. It acts as a launching pad for developers all around the globe, allowing them to sell and license their products more effectively. However, due to a recent bug in its software development kit (SDK), it has recently come under scrutiny for all the wrong reasons.
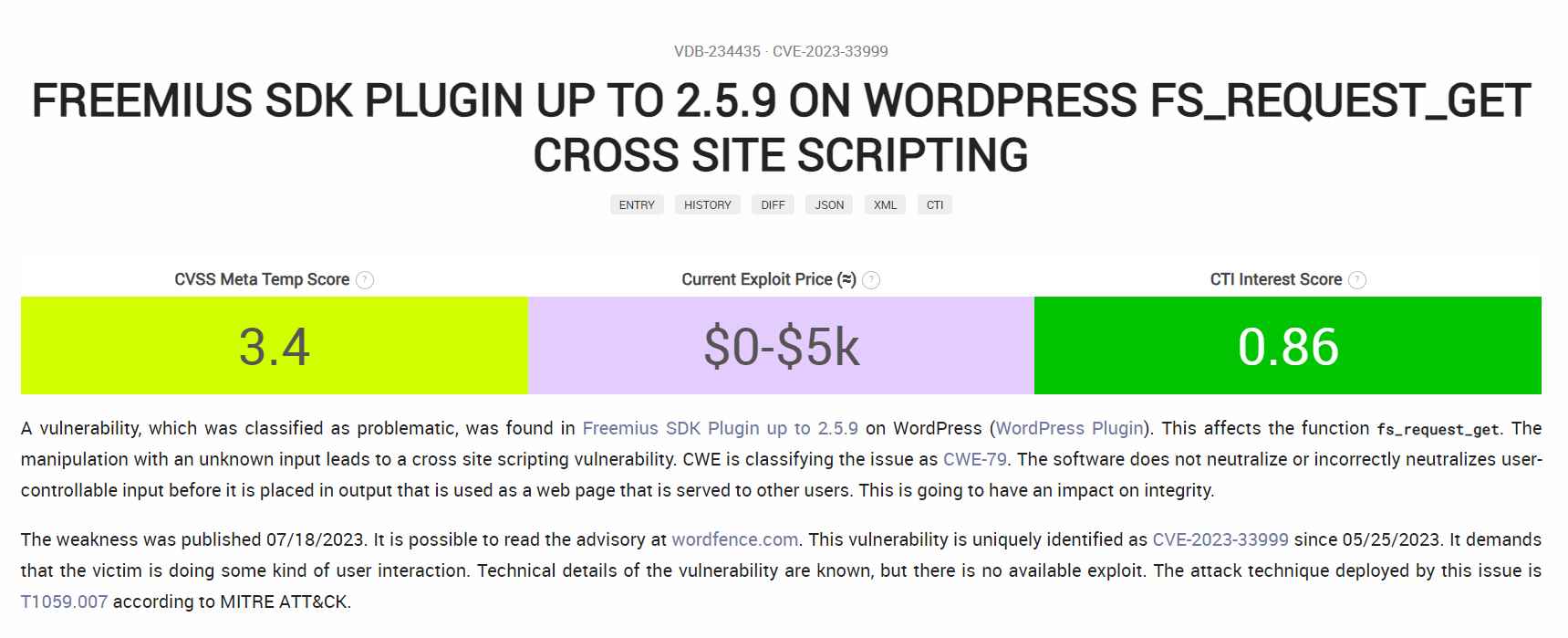
This particular flaw, which has been given the identifier CVE-2023-33999, is a Reflected Cross-Site Scripting (XSS) vulnerability that affects the whole website. Because of this vulnerability, any user who is not authenticated on the WordPress site might possibly be given the opportunity to steal important information or even elevate their privileges. To exploit this vulnerability, the malicious attacker may, for example, fool an administrator or another privileged user into accessing a specially designed URL. This would allow the attacker to take advantage of the issue.
The developers have resolved this vulnerability in the Freemius WordPress SDK version 2.5.10, therefore patching up the security vulnerability and assuring that the platform is secure. Fortunately, the silver lining to this ominous cloud is here. Although no attacks that explicitly target this vulnerability have been documented up to this point, it is always best to err on the side of caution rather than regret.
The suggestion is loud and clear: if you are a vendor with a plugin or theme that requires these plugins, please update them.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
