Websites that are powered by WordPress have been the target of attacks by hackers for a number of years. Experts in information security keep track of incidents in which different flaws in the WordPress platform are exploited in order to hack websites and insert dangerous scripts into them. An investigation into a previously unknown trojan application by the experts at Doctor Webs revealed that it is possible that the application is the malicious tool that cybercriminals have been employing for more than three years to carry out attacks of this nature and make money through arbitrage, which is the process of profiting from the resale of traffic.
According to the categorization provided by anti-virus software, this malicious software is known as Linux.BackDoor.WordPressExploit.1, and it is designed to attack 32-bit versions of Linux. However, it is also capable of running on 64-bit versions of Linux. A backdoor known as Linux.BackDoor.WordPressExploit.1 allows malicious actors to have remote control over the system. It is able to conduct the following things when they give it the instruction to do so:
- Target and attack a particular webpage (website);
- Change its mode to standby;
- power itself off;
- and temporarily stop tracking its activities.
The primary purpose of the malware is to hack into websites that use WordPress as their CMS (Content Management System) and insert a malicious script into the websites’ respective webpages. It does this by exploiting flaws that are already known to exist in WordPress plugins and website themes. Before launching its attack, the trojan communicates with its command and control server to get the address of the website it is intended to infect. Next, Linux. BackDoor. WordPressExploit.1 will repeatedly attempt to attack vulnerabilities in the dated plugins and themes listed below, all of which are capable of being installed on a website:
- WP Live Chat Support Plugin
- WordPress – Yuzo Related Posts
- Yellow Pencil Visual Theme Customizer Plugin
- Easysmtp
- WP GDPR Compliance Plugin
- Newspaper Theme on WordPress Access Control (vulnerability CVE-2016-10972)
- Thim Core
- Google Code Inserter
- Total Donations Plugin
- Post Custom Templates Lite
- WP Quick Booking Manager
- Faceboor Live Chat by Zotabox
- Blog Designer WordPress Plugin
- WordPress Ultimate FAQ (vulnerabilities CVE-2019-17232 and CVE-2019-17233)
- WP-Matomo Integration (WP-Piwik)
- WordPress ND Shortcodes For Visual Composer
- WP Live Chat
- Coming Soon Page and Maintenance Mode
- Hybrid
In the event that one or more vulnerabilities are successfully exploited, the targeted website will have a malicious JavaScript injected into it, which will be downloaded from a remote server. Because of this, the injection is carried out in such a manner that, whenever the infected page is loaded, this JavaScript will be run first — despite the fact that the page’s original content will not be affected by this in any way. At this point, visitors will be sent to the webpage that the attackers need people to visit anytime they click anywhere on the compromised page.
The following screenshot illustrates an example of one of the pages that has been compromised:
An illustration of one of the pages that has been compromised.
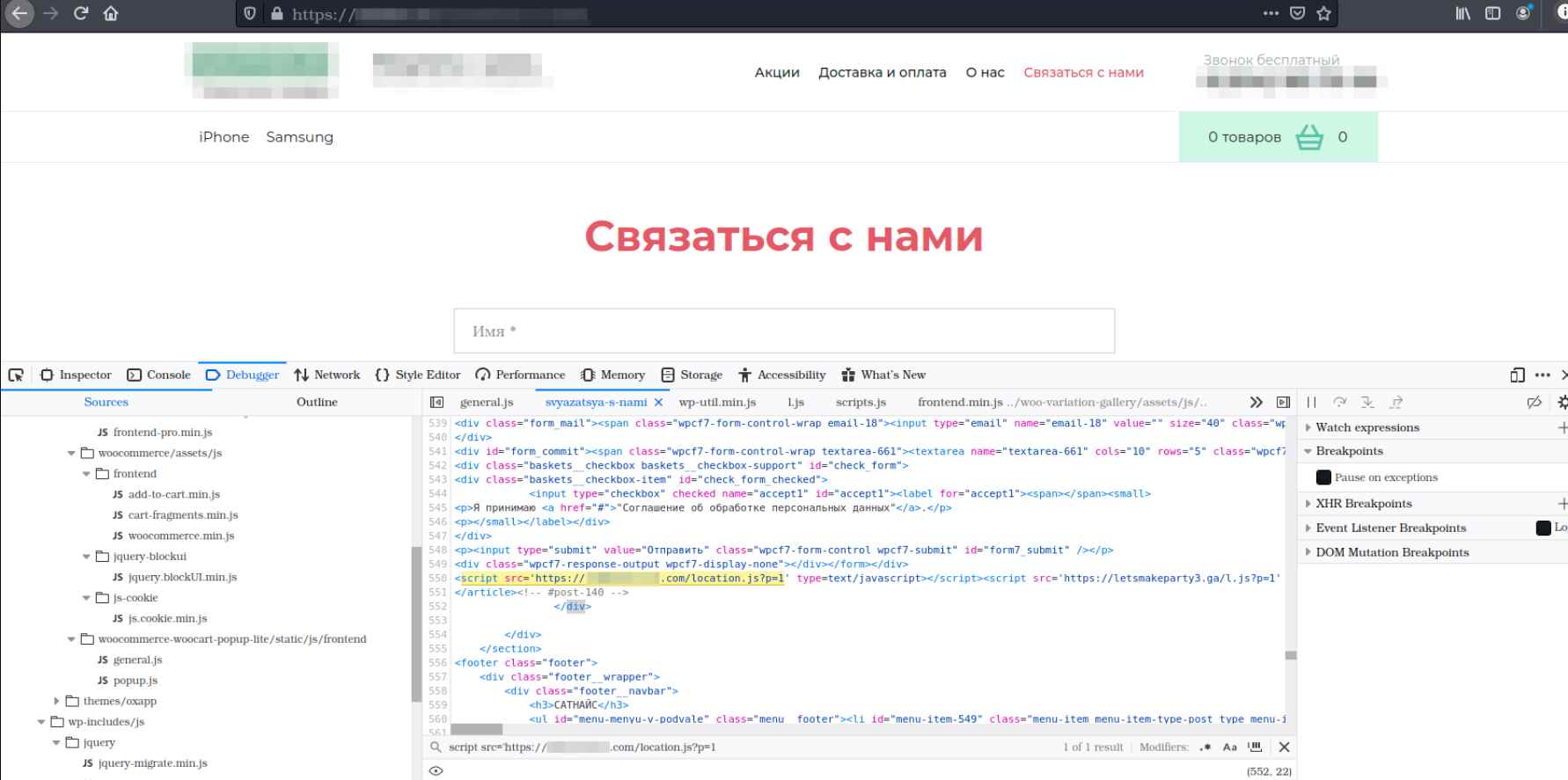
The trojan program keeps a log of its activity and gathers statistics. It monitors the total number of websites that have been attacked, each instance in which a vulnerability has been successfully exploited, and in addition to that, it monitors the total number of times that it has successfully exploited the WordPress Ultimate FAQ plugin and the Facebook messenger that Zotabox provides. In addition to this, it notifies the remote server of any vulnerabilities that are found that have not been fixed.
Experts have uncovered the most recent version of Linux for this trojan program, in addition to the most recent alteration of the virus itself.
BackDoor.WordPressExploit.2. It varies from the original one in terms of the address of the C&C server, the address of the website from which the malicious JavaScript is downloaded, as well as the presence of an extra list of vulnerabilities that may be exploited in the following plugins:
- Brizy WordPress Plugin
- FV Flowplayer Video Player
- WooCommerce
- WordPress Coming Soon Page
- WordPress theme OneTone
- Simple Fields WordPress Plugin
- WordPress Delucks SEO plugin
- Poll, Survey, Form & Quiz Maker by OpinionStage
- Social Metrics Tracker
- WPeMatico RSS Feed Fetcher
- Rich Reviews plugin
As a result of this, it was discovered that both variants of the trojan contained unimplemented functionality for hacking the administrator accounts of targeted websites by employing a brute-force attack. This attack involves applying known logins and passwords while making use of specialized vocabularies. It is conceivable that this feature was included in prior updates, or alternatively, that the attackers aim to utilize it for future versions of this malicious software. Both of these possibilities are feasible. If such an option is implemented in newer versions of the backdoor, then cybercriminals will even be able to successfully attack some of those websites that use current plugin versions with patched vulnerabilities. This is because cybercriminals can exploit a vulnerability in a plugin when it is used in conjunction with the backdoor.
It is highly recommended by that owners of websites built with WordPress maintain all of the components of the platform, including third-party add-ons and themes, up to date. In addition, it is recommended that owners use robust and unique logins and passwords for their accounts.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
