The National Security Agency (NSA), the Federal Bureau of Investigation (FBI), and the Five Eyes (Five Eyes) from a variety of nations came together to write a report that was just released by the Cybersecurity and Infrastructure Security Agency (CISA).
The paper offers a comprehensive understanding of the Common Vulnerabilities and Exposures (CVEs) that threat actors commonly took advantage of.
According to the research, threat actors have been relying on obsolete software vulnerabilities for the purpose of exploiting software rather than those that have been reported lately. The majority of attacks were directed at unpatched, internet-facing systems that were vulnerable because they lacked security updates.
The Vulnerabilities exploited in the Year 2022
Within two years of their first public disclosure in 2022, it was discovered that threat actors were already exploiting known vulnerabilities. The majority of the vulnerabilities that were exploited contained Proof-of-concept (PoC) code that was accessible to the public.
However, timely patching of these vulnerabilities will minimize threat actor activities, which will result in the malicious actors moving to a procedure that takes more time (such as performing software supply chain operations or using a zero-day exploit).

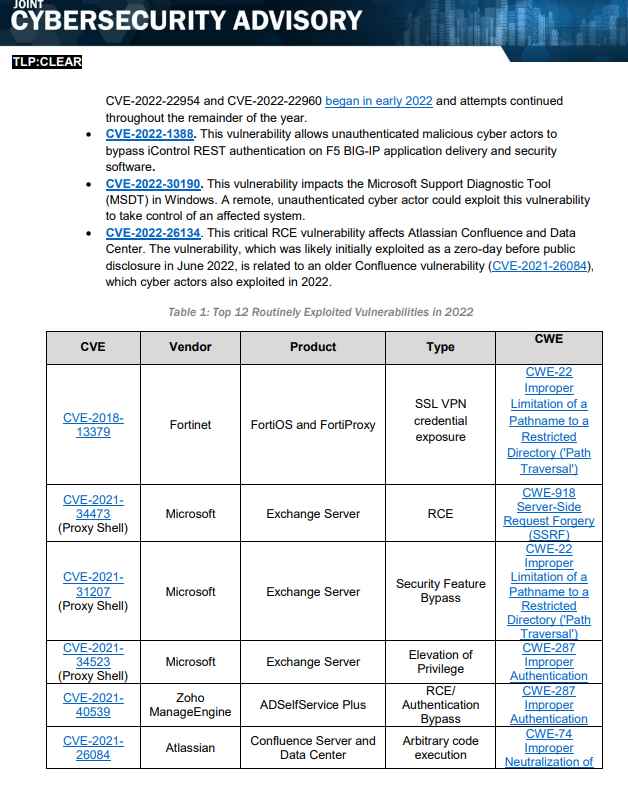
The Most Commonly Exploited Flaws
CVE-2018-13379, a vulnerability that impacted Fortinet SSL VPNs, was the one that was used to exploit the issue the most in 2022. In addition to that, this vulnerability was one of the most abused ones in both the year 2020 and the year 2021.
This vulnerability has not been addressed by many businesses, which leaves additional room for hostile actors to take advantage of it.
Both of Atlassian’s vulnerabilities, CVE-2021-26084 (which allowed for the execution of arbitrary code) and CVE-2022-26134 (which allowed for the execution of remote code), were mostly exploited in the year 2022. The Confluence Server and the Data Center are responsible for both of them.
In 2022, vulnerabilities such as CVE-2021-31207, CVE-2021-34473, and CVE-2021-34523 were regularly exploited and could be found in Microsoft Exchange email servers. A threat actor might potentially execute arbitrary code if they exploited any of these vulnerabilities, which are collectively referred to as ProxyShell.
CVE-2022-22954 and CVE-2022-22960 were the two flaws in VMware products that threat actors focused on exploiting the most. These flaws were present in VMware Workspace ONE Access, Identity Manager, and other VMware products.
These flaws were known as Remote Code Execution (RCE), Privilege Escalation (PE), and Authentication.
In addition, the Computer Security Industry Association (CISA) has made public a list of 42 vulnerabilities that were often exploited by threat actors but have not been patched by many different organizations.
Users of the products in question are strongly encouraged to update their software to the most recent patched version in order to protect themselves against exploitation by malicious actors.
Maintaining an up-to-date record of the most current patches and software versions that are installed and operational inside a company is a recommended best practice.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
