The video chat company Zoom has issued updates for various security flaws that leave users of Windows and macOS vulnerable to malicious hacker attacks. These vulnerabilities affect users of both operating systems. The two vulnerabilities, CVE-2023-22885 (with a CVSS score of 8.3) and CVE-2023-22883, were both given a “high-severity” rating by Zoom on the company’s security bulletin (CVSS score of 7.2)
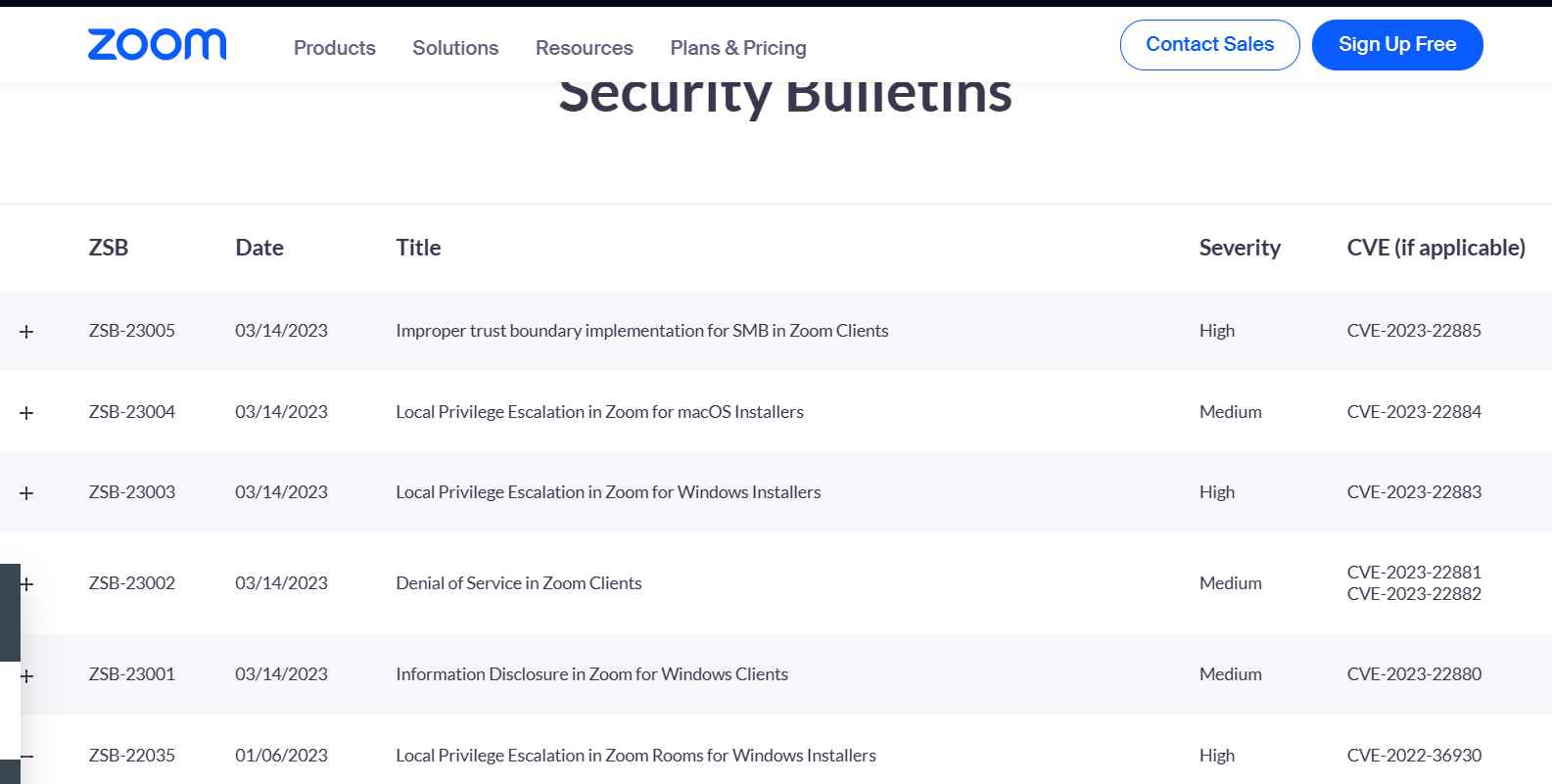
CVE-2023-22883 – Local Privilege Escalation in Zoom for Windows Installers
The Zoom Client for IT Administrators has an issue that allows for the elevation of local privileges may be found in earlier versions of the Windows installation. This vulnerability might be exploited by a local user with low rights as part of an attack chain carried out during the installation process. This would allow the user’s privileges to be elevated to those of the SYSTEM user. Windows installations for the Zoom Client for Meetings designed for IT Administrators that are older than version 5.13.5
Affected Products:
- Zoom Client for Meetings for IT Admin Windows installers before version 5.13.5
CVE-2023-22885 – Improper trust boundary implementation for SMB in Zoom Clients
CVSS Score: 8.3
Zoom clients previous to version 5.13.5 have a security issue that involves an inappropriate trust boundary implementation. If a victim saves a local recording to an SMB location and later opens it using a link from Zoom’s web portal, an attacker positioned on an adjacent network to the victim client could set up a malicious SMB server to respond to client requests, causing the client to execute executables controlled by the attacker. This occurs when a victim saves a local recording to an SMB location and later opens it using a link from Zoom’s web portal. This might lead to an attacker getting access to a user’s device and their data, as well as allowing the attacker to remotely execute code.
Affected Products:
- Zoom (for Android, iOS, Linux, macOS, and Windows) clients before version 5.13.5
- Zoom Rooms (for Android, iOS, Linux, macOS, and Windows) clients before version 5.13.5
- Zoom VDI Windows Meeting clients before version 5.13.10
In the aftermath of the work-from-home wave that occurred during the pandemic, Zoom became a favorite target for assaults of the “Zoom-bombing” and other varieties.
This raised concerns about the platform’s security as well as its encryption procedures. Researchers have pointed out that even though the corporation has deployed a plethora of new security measures to match its elevated position, problems such as these are still fairly predictable.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
