A crucial component of the production and distribution of electric power is the use of flow computers, which are specialized computers that calculate oil and gas volume and flow rates. These devices monitor liquids or gases that are essential for process reliability and safety as well as being inputs for other processes (alarms, records, settings), therefore precision is a must. Billing is another crucial component of flow computers’ function in a utility. Due to their widespread usage in big oil and gas utilities, ABB flow computers are crucial. Flaws in them that would enable an attacker to interfere with measurements by remotely executing code on the target device.



Since flow measurement calculations, particularly those involving gas flow, require a significant amount of computing power, they are frequently performed by a low-power CPU rather than a microcontroller.
Flow meters read raw data from connected sensors that, depending on what is being measured, can measure the volume of a material in a variety of ways (gas or a liquid). Electromagnetic, vortex, differential pressure, thermal, coriolis, and other types of flow meters are some examples.
The investigation focused on the FLO G5 flow computers made by ABB.
The FLO G5 is a single board computer that has a CPU, Ethernet, USB, and other IO interfaces. The CPU has a 32-bit architecture and is an ARMv8 processor. Linux is the device’s operating system.
A designated configuration program can be used to remotely configure the flow computer.
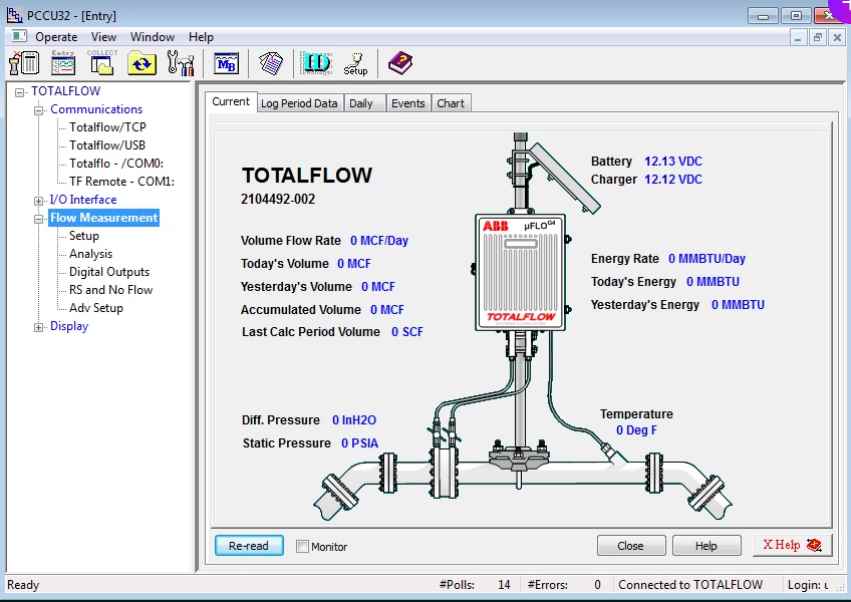
The key thing to notice is that setup is done using a proprietary protocol established by the ABB called TotalFlow. Using this protocol on top of a serial or Ethernet (TCP) connection is possible. The TotalFlow protocol (TCP/9999) is used for the majority of communication between the client and the device, including retrieval of the gas flow calculations, establishing and obtaining device settings, and importing and exporting configuration files.
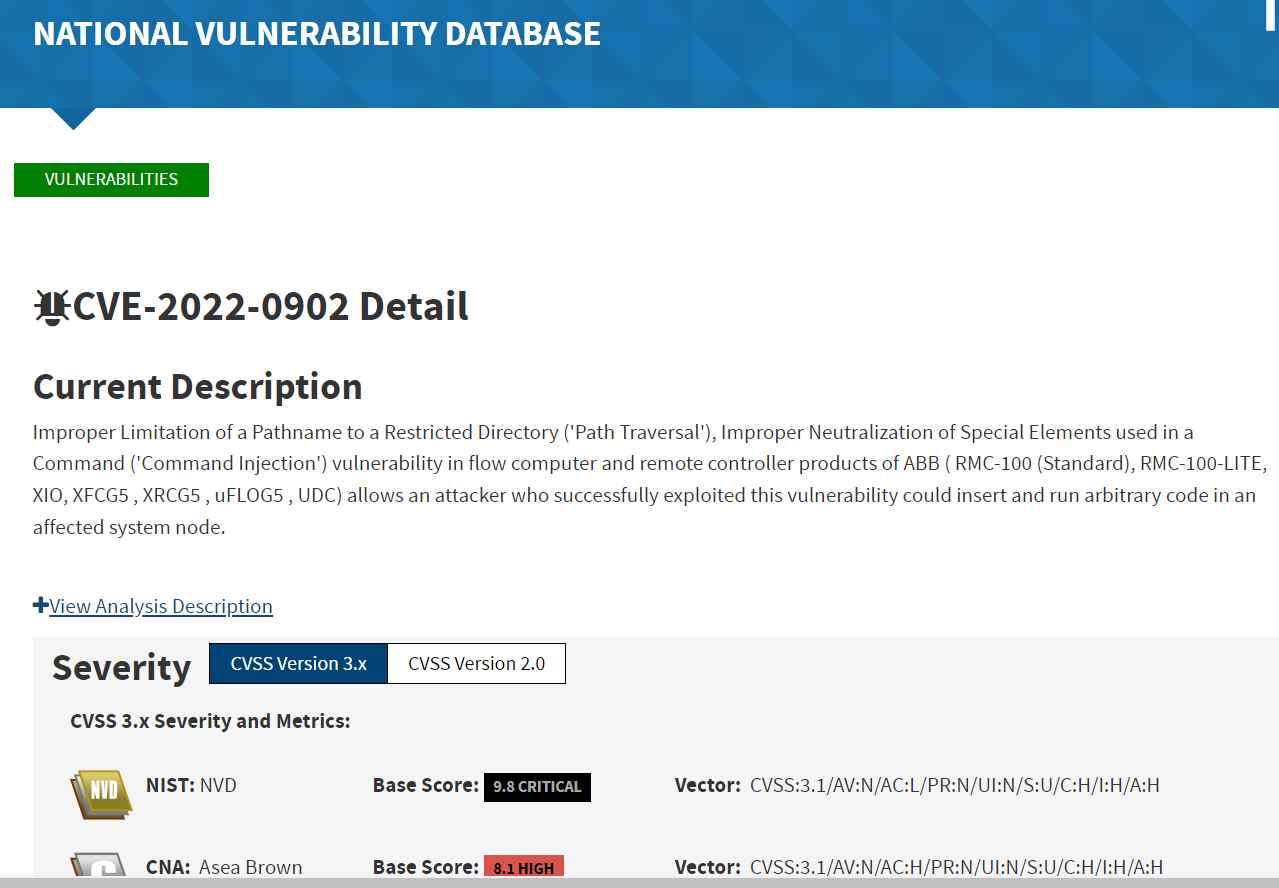
Their discovered vulnerability, CVE-2022-0902, has a CVSS v3 score of 8.1 out of 10 and was just fixed in an ABB firmware upgrade.
CVE-2022-0902
Path Traversal Vulnerability
Products Affected: The Totalflow TCP protocol for ABB Flow Computers and Remote Controllers. ABB’s RMC-100 (Standard), RMC-100-LITE, XIO, XFCG5, XRCG5, uFLOG5, and UDC products.
An attacker may be able to remotely control flow computers and interfere with their capacity to precisely monitor oil and gas flow thanks to this path traversal vulnerability. These specialized computers compute the measures, which are inputs for a variety of operations including configurations and customer billing.
A successful exploitation of this vulnerability might make it difficult for a business to bill clients, necessitating a suspension of services, much to what happened to Colonial Pipeline after its 2021 ransomware attack.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
