The cybersecurity community is concerned about finding a potential security flaw that would allow a threat actor to manipulate Power Point files to download and install malware on a device with a simple mouse pointer interaction with a hypertext link.
According to reports, this attack requires the target user to accept a pop-up dialog box to run or install a program; While Microsoft does not consider such scenarios as a security vulnerability, multiple experts have a contrary view.
Mandar Satam, a standalone cyber security researcher, ensures that the attack can circumvent a fundamental restriction in PowerPoint, which prevents adding a remote file to the HyperLink action. Satam added that this attack would allow you to manipulate the dialog box to display anything.
The researcher created a proof-of-concept of the attack by abusing Power Point’s Open XML slideshow files, called PPSX. These files were designed only for playback of presentations, so they cannot be edited.
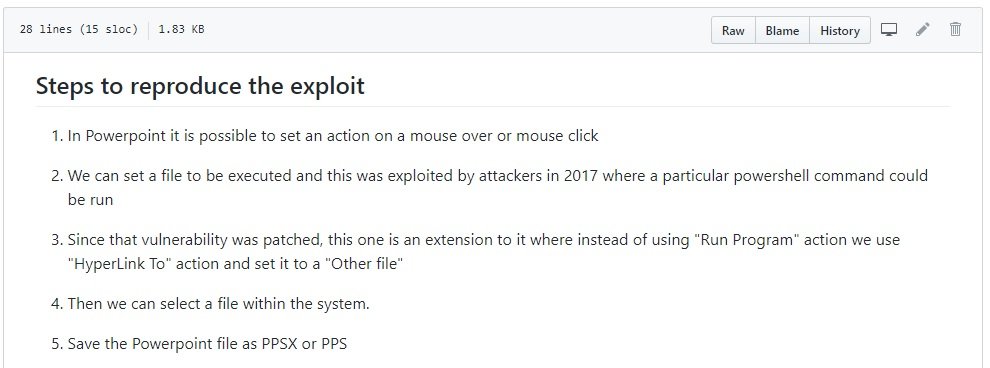
However, Satam managed to evade the restrictions, getting the malicious links used for the attack to install local executable programs at the time the user hovered over a hypertext link: “Since that vulnerability was corrected, this is an extension in which, instead of using the ‘Run Program’ action, we use the ‘HyperLink To’ action configured in ‘Other File’ specifically,” the researcher says.
When you change “Run Program” to “HyperLink To”, the proof of concept runs the file from a remote server, which allows remote editing and reading of content. “Because of the way SMB connections work on Windows 10, SMB connections over the Internet are possible even if SMB ports (445/139) are closed if an attacker hosts a web server that supports the WebDAV extension,” the researcher wrote.
Because the attack is triggered very simply, the researcher assures that it should be treated as a security vulnerability. After receiving the report, the Microsoft Security Response Center (MSRC) has a different opinion, as the attack consists largely of a social engineering process. Satam’s investigation was rejected by Microsoft, although the company claims its security teams will be investigating this behavior by their own.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
