This week it was announced that Apple discreetly fixed a severe vulnerability in Apple Wireless Direct Link (AWDL) that could have been exploited by malicious hackers in order to compromise “air-gap” networks, a term used to refer to the isolated and highly secure environments employed by some public and private organizations.
The flaw was addressed with the release of the Big Sur 11.31, iOS 14.5, iPadOS 14.5 and watchOS 7.4 systems and publicly disclosed a few days ago by Finnish security researcher Mikko Kenttälä through his blog.
The researcher points out that AWDL is a protocol implemented by Apple in 2014 that allows the company’s devices to communicate with each other via Bluetooth or WiFi and that it is critical for the use of AirPlay and AirDrop. By default, devices with AWDL search for other devices within their search range, a process performed in the background on Apple devices whenever their WiFi or Bluetooth connection is enabled.
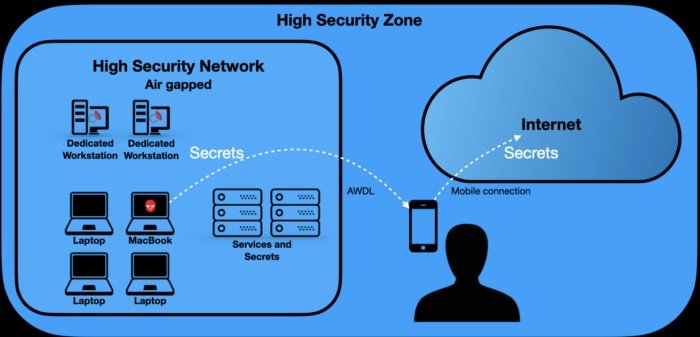
Due to the complexity behind this attack, the researcher summarized the details by mentioning that it all starts from finding a method to use ICMPv6 and IPv6 packets to extract data from the vulnerable system, bounce the packets into a nearby AWDL, and send the stolen data to other IPv6 devices.
Although much more functional methods for data theft are currently known, Kenttälä mentions that this could be a serious problem for air-gap network administrators, who are designed for offline operation and are in isolated environments. As mentioned above, these solutions are deployed in government, military, and enterprise entities for confidential storage.
The expert considers that, in the event that a cybercriminal succeeds in infecting a device on any air-gap network, the reported flaw could be abused to steal information as long as an employee with a vulnerable device stays close enough to an air-gap environment.
The cybersecurity community often does not take these reports seriously due to their complex operating conditions; nonetheless these issues do represent a concern for air-gap system administrators, as they know that the nature of the information stored in these environments will always be attractive to threat actors, so they consider that sufficient precautions are never taken.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
