Surely the vast majority of the cybersecurity community heard about the hacking incident in Oldsmar, Florida. It was the morning of February 8 that county sheriff Ponellas held a press conference to reveal that an attempt had been detected to manipulate the city’s water treatment plant systems, which would have resulted in the poisoning of millions of gallons.
One of the investigative teams that were able to analyze this incident was that of security firm Dragos, who found a connection with a water services contractor in Florida that hosted malicious code on its website. The malicious code targeted public water systems in the state of Florida in a hacking variant known as a watering hole attack.
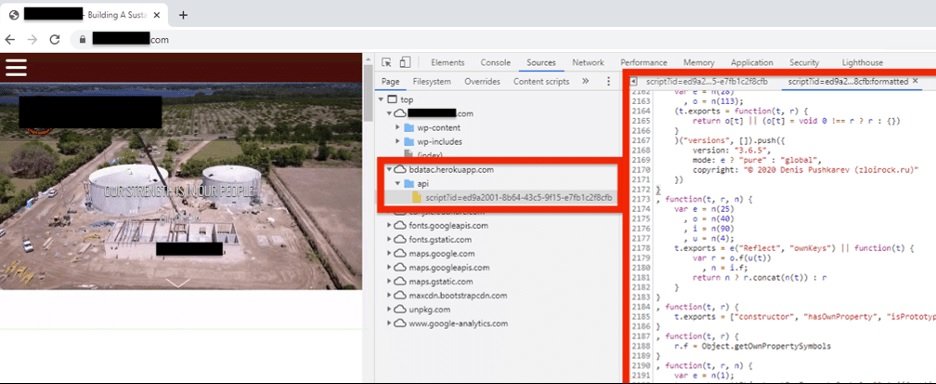
According to the report, threat actors injected the malicious code into the footer file of the aforementioned WordPress-based contractor’s website. Cybercriminals would also have abused a vulnerable WordPress plugin installed at the time of the attack.
Attacks persisted for two months
This attack impacted virtually every system from which the compromised website was visited, within nearly 60 days from December 20, 2020. The malicious code was removed from this website on February 16, 2021.
The compromised website was visited from multiple teams, including computers of water service clients, local government offices and multiple private companies. The malware injected into this website was able to take detailed logs of at least 1000 end-user computers, mainly in the state of Florida.
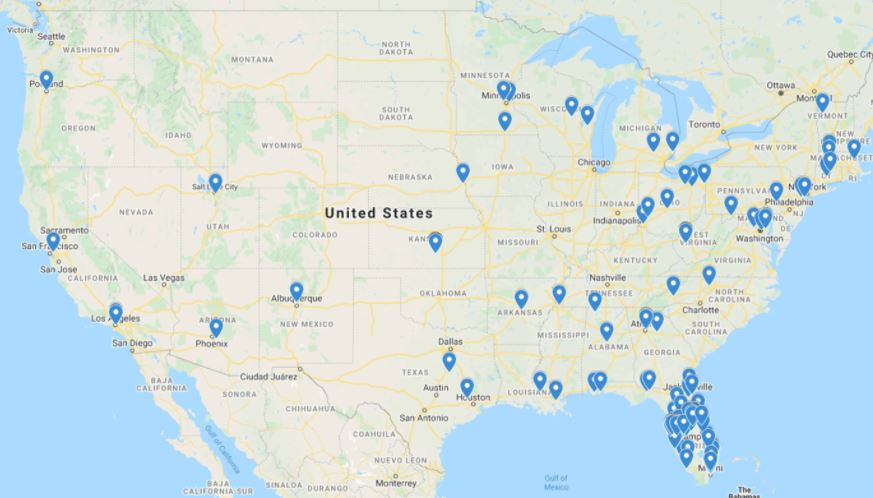
Researchers used telemetry to determine that a user of a networked system in Oldsmar, Florida, visited the compromised website on the morning of February 5, 2021. A detailed analysis showed that this is the same network from which threat actors managed to compromise a computer in the water treatment silver that same day in previous hours, trying to manipulate the supplied chemicals into the water using the Man-Machine Interface (HMI) in the system.
Experts issued an alert to notify that this watering hole attack could be targeting Florida’s water services. The Department of Homeland Security (DHS) also received an alert to announce possible hacking attempts. After launching the security alert, Dragos experts undertook their research into the incident.
Tracking the origin of the attack
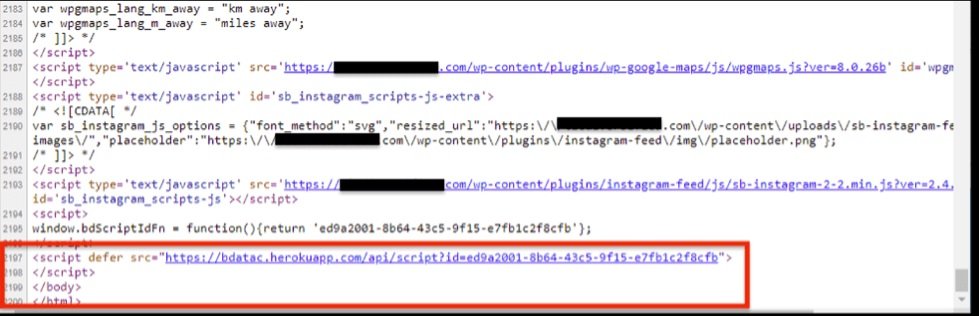
Dragos’ research began by reverse engineering the script for the collection of fingerprints found on this website, discovering that hackers created this script from code from four different projects: core-js, UAParser, regeneratorRuntime and a script for data collection that has only been found on two websites associated with a domain registration, hosting and web development company.
Hackers would have collected more than 100 items of detailed information about website visitors, including:
- Operating system and CPU
- Web browser used
- Contact points, input methods, camera presence, accelerometer, microphone, etc.
- Details of the video card display adapter
- Time zone, geolocation, screen resolution and browser plugins
The script used by hackers also redirected affected users to two separate websites where encrypted digital fingerprints such as TLS logs and JA SSL logs would be collected.
When this information was collected from browser memory, the JavaScript code sent the data via HTTPS protocol POST to a database on the same Site in the Heroku application that hosted this script (bdatac.herokuapp.com). The app was removed after Dragos experts filed their report. Dragos researchers discovered that the DarkTeam platform hosted this website and served it to the Internet browsers that visited it. It should be noted that this is a black market website that offers stolen financial information.
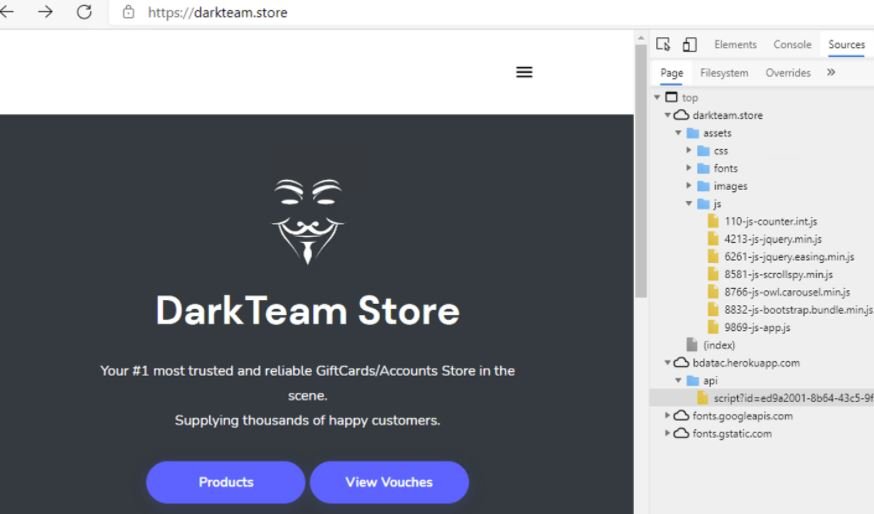
Subsequent scans revealed that this website is not a hacking platform, but a registry for infected systems with a botnet malware variant known as Tofsee.
The investigation observed at least 12,700 IP addresses identified as Systems Infected with Tofsee; these clients connect to a page that required authentication associated with the DarkTeam site, presenting a browser user agent string with a Tesseract/1.0 agent.
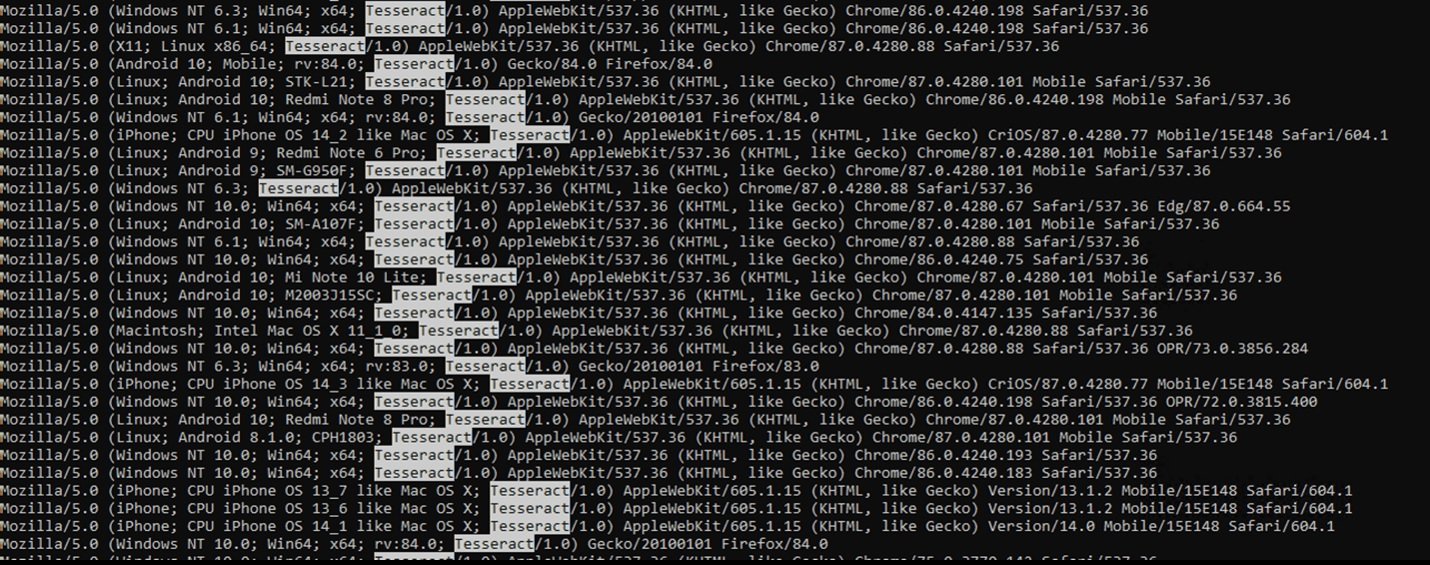
The bot verification routine may be the response of the author of the Tofsee malware to the defense tactics used to detect pre-Tofsee malware iterations with an identifiable JA3 hash. Dragos performed a forensic log analysis and identified three ja3 hashes unique to this new Tofsee botnet that Dragos identifies as “Tesseract”. Dragos also obtained other JA3 hashes from an industry partner who observed connections from this botnet. Some of these JA3 hashes are also associated with legitimate browsers.
In short, experts conclude that the threat actors installed the watering malware on the contractor company’s website to collect legitimate information from users in order to increase the capabilities of the Tofsee botnet, hiding its malicious activity from security tools.
It is unclear why threat actors decided to focus on water treatment plants, although a couple of similar incidents have been detected in the United States in recent months. Most strikingly, unlike other watering hole attacks, the code does not generate exploits or be used to access the victims’ systems. According to experts, the attacker may have believed that the contractor’s website would allow more time to collect data important to the attackers’ targets, although the hackers’ intentions have not been confirmed.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
