The cybersecurity community continues to try to collect and process as much information as possible about the recent attack on the SolarWinds supply chain, finding more and more information to help understand the incident as a whole. One of the most recent revelations came directly from the software company, whose executives claim that everything could be related to an unsafe password that went unnoticed for years.
The incident has already compromised at least nine U.S. government agencies, as well as a hundred private companies, so it is considered one of the most complex cyberattacks in recent years.
SolarWinds staff believed that the password (solarwinds123) was publicly accessible through a GitHub repository since June 2018, before this condition was fixed in November 2019. However, company CEO Sudhakar Ramakrishna recently confirmed that this password has been in use since 2017. This statement was issued during a Ramakrishna hearing before the Oversight and Reform and National Security Committees of the House of Representatives.
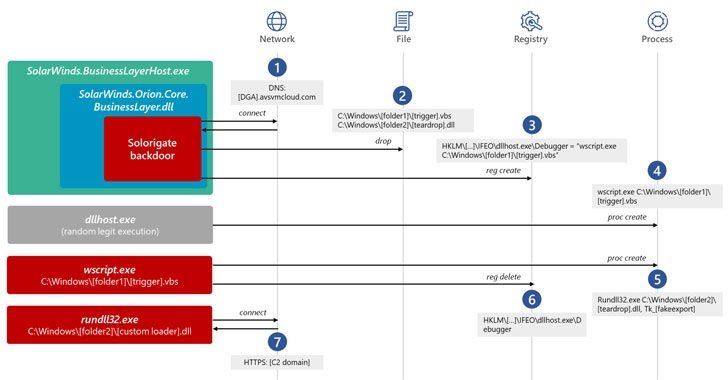
Initial reports mentioned that the operators of this campaign managed to compromise SolarWinds Orion’s supply chain to distribute the Sunburst backdoor in October 2019. However, a recent Crowdstrike investigation claims that the first attacks were detected approximately one month before the date mentioned above.
“I think that was a password used by an intern with access to a server in 2017, which was reported to our security team and corrected immediately, Ramakrishna mentioned during his hearing. Kevin Thompson, former CEO of SolarWinds, agrees with the current CEO on this password: “This behavior was related to the mistake made by an intern, resulting in a violation of our internal password policy. As soon as we detected that incident, improper access was shut down and the password was restored.”
Last December, cybersecurity expert Vinoth Kumar reported to SolarWinds that a publicly accessible GitHub repository was leaking the FTP credentials of its official download site, noting that a threat actor could use this information to load all kinds of malicious executables and add them to software updates.
The biggest problem facing the company today is the lawsuit filed in January alleging that failures exploited by threat actors had been present at SolarWinds Orion since mid-2020. These flaws would have compromised the affected servers, in addition to poor security practices in the company, such as the use of very unsafe passwords.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
