Following the announcement of the close of operations of the DarkSide ransomware as a service (RaaS) platform, a group of threat actors allegedly affiliated with the platform is demanding that malware operators pay for various successful attacks, including the recent incident in Colonial Pipeline. To demand payment, criminals are turning to hacking forum administrators, who in cases like these operates as a court of law.
Investigators at security firm Huntress have experience in monitoring similar cases, noting that the most recent complaints to this “law court” relate to DarkSide and non-compliance with its affiliate policies. These claims are resolved in a courtroom made up of recognized hackers and illegal platform administrators.
Huntress investigators published some screenshots showing some of the plaintiffs’ arguments and possible measures for resolving the dispute.
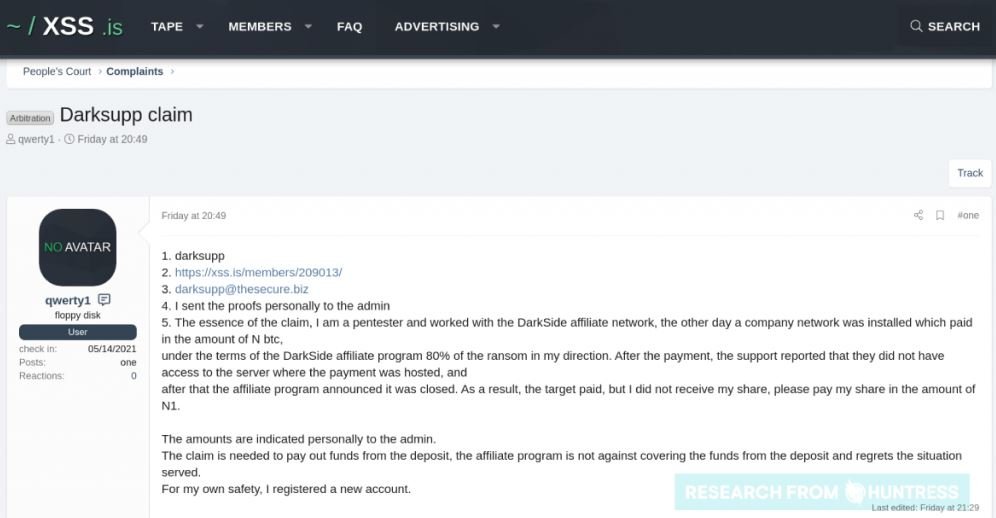
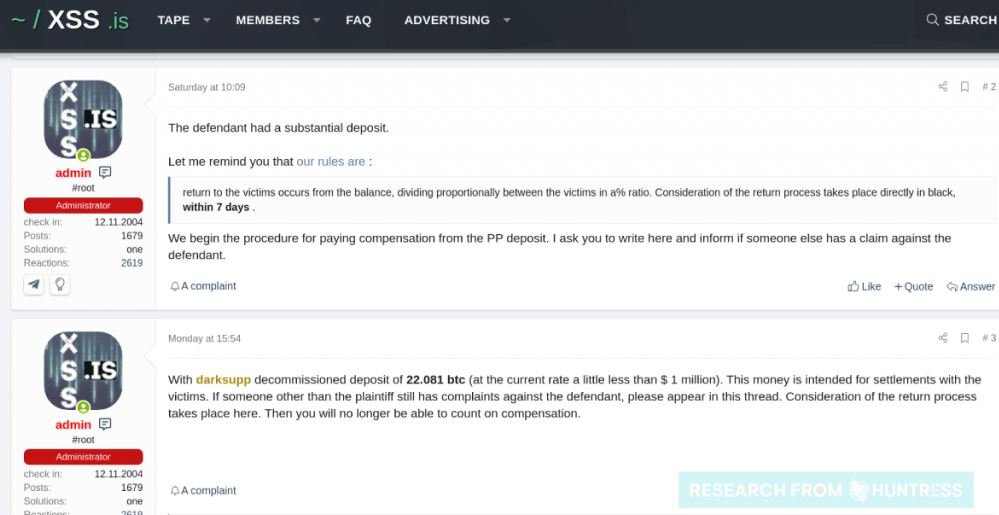
Cybersecurity specialist John Hammond says: “Cybercrime has evolved to such a high standard that there is a kind of popular court for multi-conflict dispute; in cases where a scammer is scamming or two parties breach an agreement. There is really no honor among the cybercriminal community, but there is a code of conduct to which threat actors must adhere.”
The screenshots collected by Huntress refer to the latest news, possibly speaking of the incident in Colonial Pipeline: “Our goal is to make money, we are not interested in going into controversy for politically motivated acts,” the alleged DaskSide operators mention.
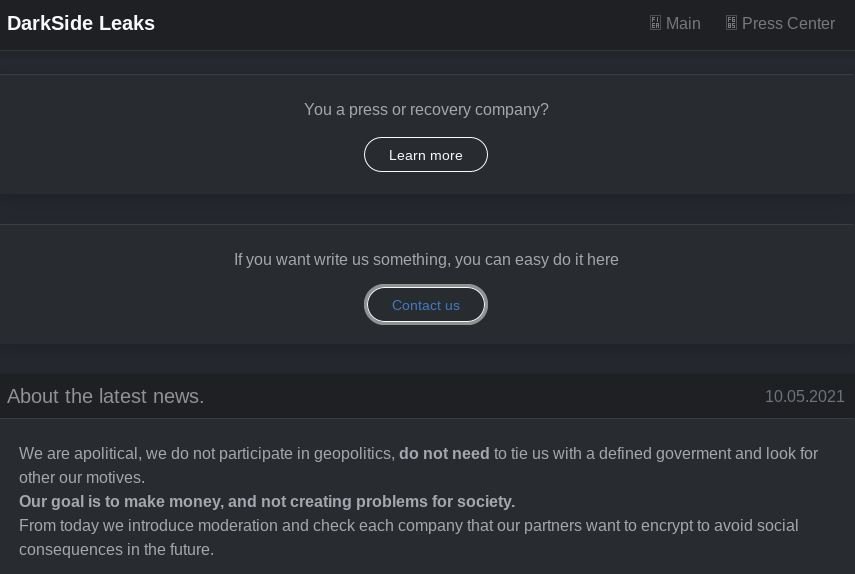
DarkSide added a note announcing the implementation of a form of moderation in their malicious campaigns to avoid possible political consequences in subsequent attacks. The measures announced by the ransomware operators have to do with requesting information from their affiliates, as at all times the creators of DarkSide have denied having to do with the recent attack on Colonial Pipeline, attributing the consequences of these attacks to their affiliates.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
