Experts detail the finding of a phishing campaign in which threat actors craft a trap, making it difficult for potential victims to identify malicious behavior, increasing the chances of success in the attack.
Most phishing campaigns are really simple, involving only a malicious website to which it is about redirecting the target user. In this case, cybercriminals include some additional steps to confuse users and eliminate any suspicions that may arise about the attack.
Like any other phishing campaign, it all starts when you receive an unknown email:
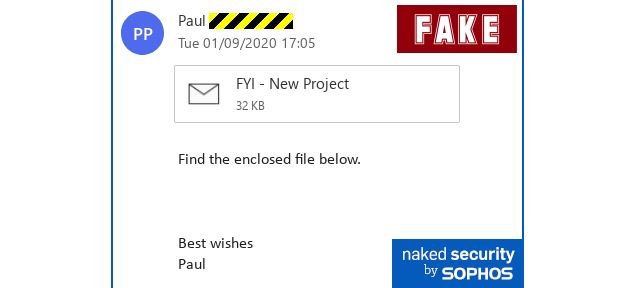
In the case analyzed by NakedSecurity researchers, the message comes from the owner of a legitimate British company whose email account was previously compromised. The message came into the hands of the experts because the sender is a subscriber to the company’s blog, so NakedSecurity’s email address was on their contact list.
Given the characteristics of the compromised account, researchers believe the owner regularly communicated with their contacts, sending messages and attachments of all kinds.
This is an attack known as Commercial Email Engagement (BEC), which can be used in conjunction with some phishing campaigns. Cybercriminals intentionally use these compromised accounts to deceive business partners and unsuspecting users. When opening attachments, a legitimate-looking message appears, specially designed for users who communicate the most with the compromised account.
Threat actors expect the user to click on a link that redirects to a One Note file, which should already seem suspicious, as there is no clear connection between the sending company and this location. In most cases, the file should look similar to the following:
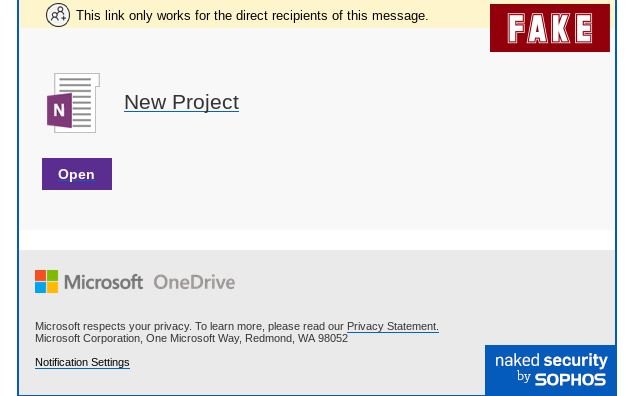
It is at this stage that hackers demonstrate their true intentions, using a Review Document button that appears to be part of the One Note file that the user previously opened.
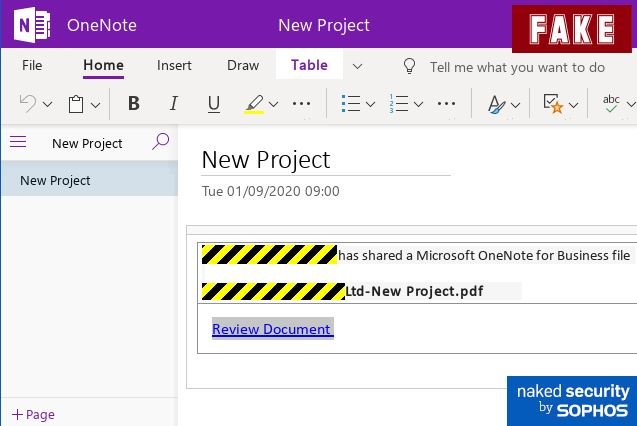
Needless to say, users do not receive any documents; instead, this button redirects them to a fake login page where threat actors will try to extract sensitive data from victims. Users are redirected to a compromised WordPress website belonging to an event organizing company.
While this is a well-organized fraudulent campaign, threat actors made a couple of mistakes that give away their intentions. To begin with, the criminals misspelled the name of the sending company, something that the most alert users will have no problem detecting.
In addition, the compromised WordPress domain does not match the name of the affected company, which is the clearest indication of fraudulent activity associated with this campaign. Finally, users are redirected to a login form where their data would be extracted.

As usual, users are advised to ignore such emails and, if possible, notify their IT area of malicious activity for the implementation of additional security measures.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
