Cybersecurity experts report that a group of threat actors managed to compromise the update mechanism of Passwordstate, a password manager for business users. The report was sent to Click Studios, the app’s developer company, which has already notified its nearly 30,000 business customers.
An internal company report, obtained by the News website Niebezpiecznik, mentions that the malicious update was active for at least 28 hours between April 20 and 22.
In this regard, the cybersecurity company CSIS published an analysis of this supply chain attack, mentioning that threat actors forced Passwordstate applications to download a ZIP file identified as “Passwordstate_upgrade.zip”, which had hidden the DLL file “moserware.secretsplitter.dll”.
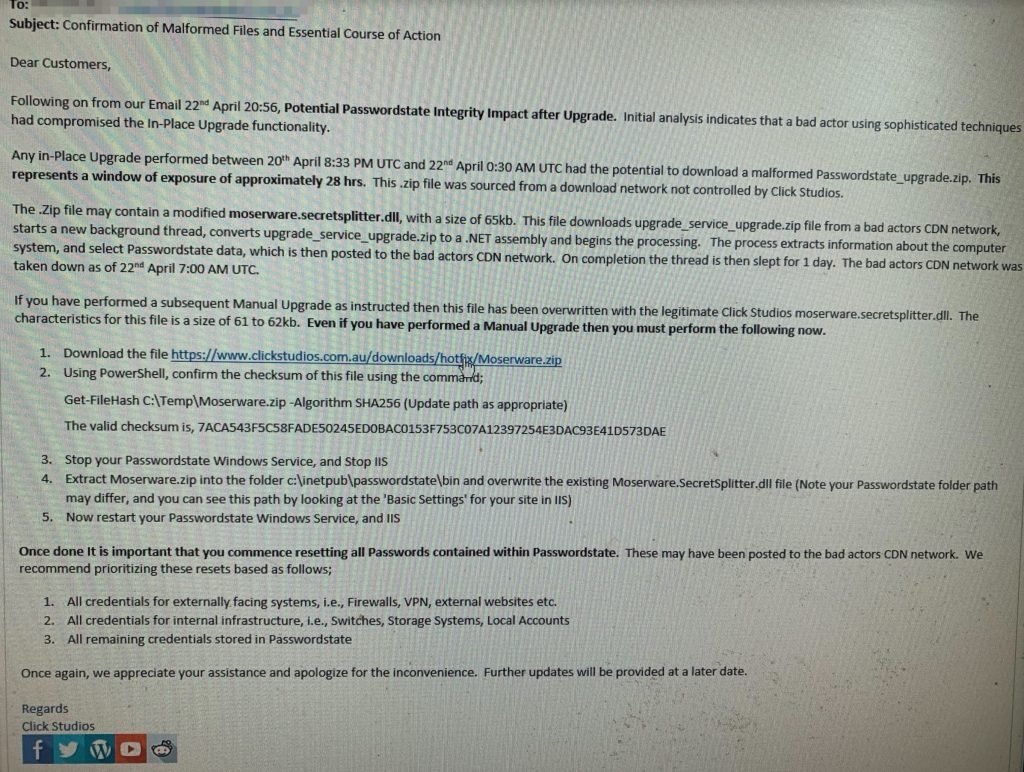
Upon completion of the installation, this file pings to a C&C server to request subsequent commands and obtain additional payloads.
Information about affected systems collected by threat actors was unknown at first, although in a later update Click Studios developers mentioned that the malware collected multiple details to send to the command and control server. Among the information compromised are details such as:
- Computer name
- Username
- Domain name
- Running processes
- Password status instance proxy server address Username and password
In other words, threat actors obtained full password storage. Developers also mention that there are other details included in the password table:
- Title
- Username
- Description
- GenericField1, GenericField2 and GenericField3
- Notes
- URL
- Password
While the company mentioned that no evidence of compromise of encryption keys or database connection strings has been detected, specialist Juan Andres Guerrero-Saade posted to his Twitter account that there are multiple tools available to decrypt Passwordstate-protected mechanisms and recover unencrypted text passwords.
The developers released a patch package that would help customers remove malware from the attacker. Click Studios mentions that the attack took place after hackers compromised the on-site update functionality of a CDN not controlled by Click Studios. Only the company’s Windows client appears to have been modified to add malware to the attack.
Because of this incident, more than 20,000 companies have reset their passwords to prevent security incidents related to this attack. Passwordstate is expected to release an update to completely mitigate the risk of attack. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
