Since at least the middle of 2021, a Chinese cyberespionage group known as Volt Typhoon has been targeting critical infrastructure companies throughout the United States, including Guam, according to Microsoft, which analyzes the activities of both groups.
Their victims come from a broad variety of important industries, such as the government, marine, communications, manufacturing, information technology, utilities, transportation, construction, and education, among others. Since the middle of 2021, Volt Typhoon has been active and has attacked organizations in Guam and elsewhere in the United States that are vital to the nation’s essential infrastructure. The companies that are being targeted in this campaign come from a variety of fields, including communications, manufacturing, utilities, transportation, construction, marine, government, information technology, and education. The pattern of activity that has been seen strongly shows that the threat actor aims to conduct espionage and keep access without being discovered for the maximum amount of time feasible.
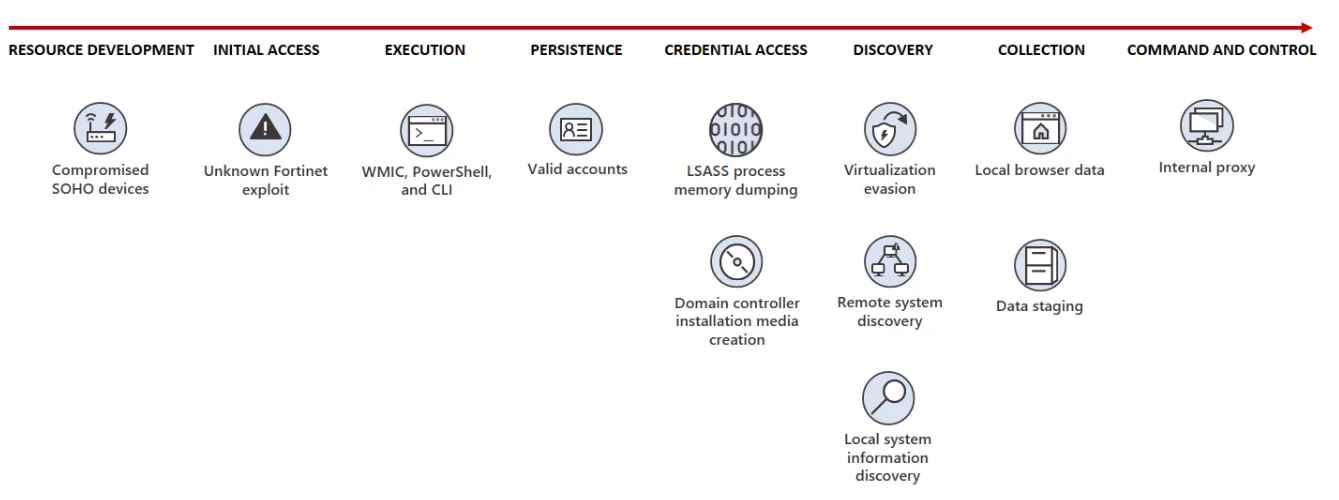
The threat actor places a significant amount of focus on stealth throughout this campaign in order to accomplish their goal. They do this by depending nearly completely on living-off-the-land practices and hands-on-keyboard activities. They utilize the command line interface to issue commands in order to: (1) gather data, including credentials, from local and network systems; (2) place the data into an archive file in order to stage it for exfiltration; and (3) use the stolen valid credentials in order to sustain persistence. In addition, Volt Typhoon attempts to blend in with regular network activity by redirecting traffic via hijacked small office and home office (SOHO) network equipment, such as routers, firewalls, and VPN devices. This is done in an effort to imitate normal network behavior. They have also been seen establishing a command and control (C2) channel through proxy by utilizing a customized version of an open-source application. This is another method they use to avoid detection by authorities.
Their campaign targeted suppliers of critical infrastructure, as well as their strategies for gaining and retaining illegal access to target networks. Detecting and combating this attack may be difficult due to the fact that it is dependent on legitimate accounts and living-off-the-land binaries (LOLBins).
Initial access to the enterprises that are the focus of the Volt Typhoon attack is gained via internet-facing Fortinet FortiGuard devices. Microsoft is continuing its investigation into the tactics used by Volt Typhoon in order to acquire access to these devices.
Volt Typhoon’s post-compromise activities very seldom involves the usage of malware. Instead, they depend on instructions that allow them to “live off the land” in order to exfiltrate data, access information on the system, and identify more devices connected to the network.
Particularly difficult is the task of mitigating danger posed by adversaries such as Volt Typhoon, which are dependent on genuine accounts and living-off-the-land binaries (LOLBins). The usage of regular sign-in channels and system binaries needs behavioral monitoring in order to be detected as suspicious behaviour. In order to remediate the situation, compromised accounts need to have their credentials deleted or changed.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
