In a joint statement from the National Security Agency (NSA), the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI) and the UK’s National Cybersecurity Centre (NCSC) reported that the hacking group known as Sandworm is employing a dangerous new malware variant.
Dubbed as Cyclops Blink, the creation of this new malicious development has been attributed to the Main Center for Special Technologies of Russia. This group has been linked to multiple incidents before, including international threats such as:
- Disruptions in the Ukrainian electricity system in 2015
- Development of NotPetya ransomware in 2017
- Cyberattacks against the Olympic and Paralympic Winter Games in 2018
- Cyberattacks against the Georgian government in 2019
The agencies described Cyclops Blink as a replacement framework for the VPNFilter malware, detected in 2018 and designed for the exploitation of network devices such as routers and network-attached storage (NAS) drives.
Cyclops Blink operators appear to act indiscriminately against WatchGuard firewall devices with default settings, although it is highly likely that malware can dock into other architectures and firmware.
The malware has basic core functionality for sending information from the compromised device to a hacker-controlled server, as well as allowing files to be downloaded and executed. Additional functionality allows new modules to be added while the malware is running, causing Sandworm to include new features to an attack as needed.
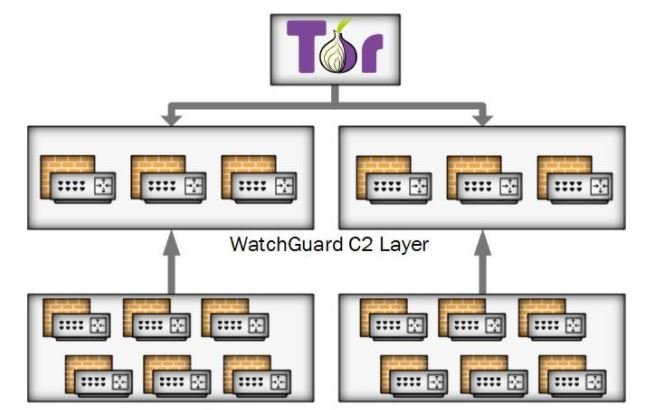
In later stages, hackers deploy the payload as part of a supposed firmware update, gaining persistence in the system and complicating the reset. Victims’ devices are organized into groups and each Cyclops Blink deployment has a list of IP addresses of C&C servers and ports used. All known IP addresses to date have been used by compromised WatchGuard firewalls.
Communications between Cyclops Blink clients and servers are protected by Transport Layer Security, using individually generated keys and certificates. Sandworm manages Cyclops Blink by connecting to its C&C servers over the Tor network.
The threat is still active and an attack can prove disastrous for affected organizations, so agencies recommend that system administrators check their full report to stay on top of the best ways to mitigate this security risk.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
