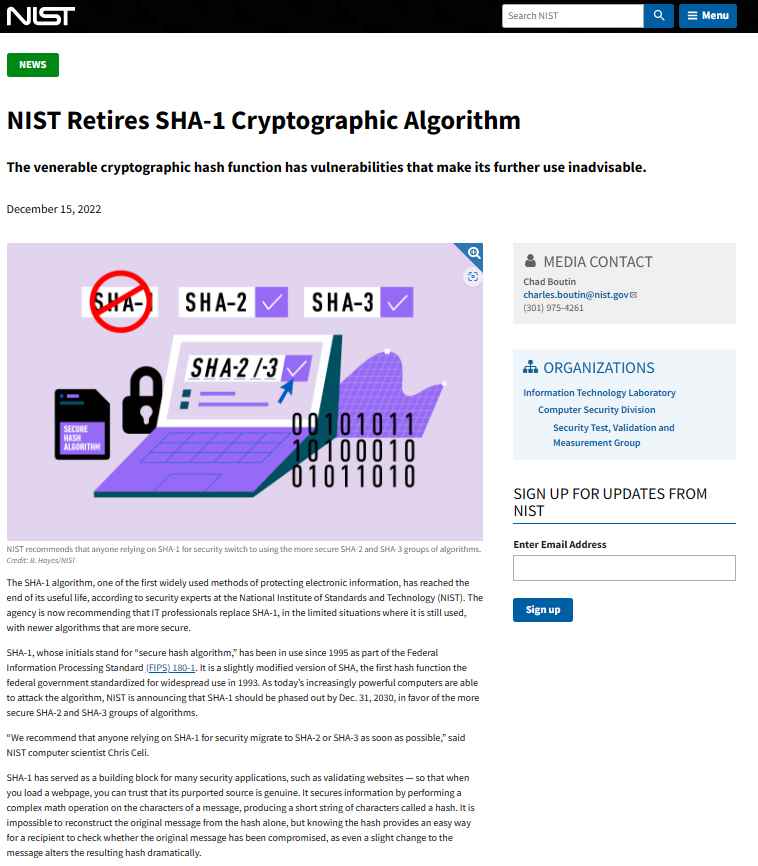
The National Institute of Standards and Technology (NIST) in the United States has announced that it is time to stop using Secure Hash Technique-1 (SHA-1), a vulnerable algorithm that has been in use for security purposes for the last 27 years. If you are concerned about your security and are still using SHA-1, we strongly suggest that you switch to SHA-2 or SHA-3 as soon as you can.
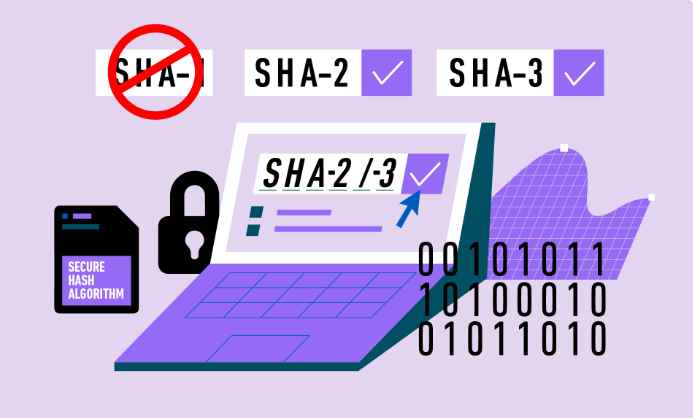
When it comes to timeliness, “as soon as feasible” isn’t often all that soon: According to the NIST, you should remove SHA-1 from all of your software and systems by the end of the year 2030. In the meanwhile, the IT sector has, for the most part, already moved on. The Federal Information Processing Standard (FIPS) 180-4 allows the use of seven different hash algorithms, and SHA-1 is one of such algorithms. SHA-1 will be removed as a supported specification from the next upgrade of the government’s hash standard, FIPS 180-5, which will take place towards the end of the year 2030.
In order to bring SP 800-131A and any other relevant NIST publications up to date and to reflect the deprecation of SHA-1, NIST plans to update these documents. Furthermore, it intends to publish a transition plan for verifying cryptographic modules and algorithms in the near future. To generate a SHA-1 hash, translate a message of indeterminate length to a message digest of fixed length, consisting of 160 bits and commonly represented by 40 hexadecimal digits. This will produce a fixed-length SHA-1 hash.
Although hashes aren’t meant to be reversible, basic message inputs like “password” may be pre-calculated and kept in lookup tables, making it easy to extract dictionary-stored input messages from related hash digests – paired with an extra value for increased security.
Because of a theoretical collision attack that was published in 2005 and became feasible in 2017 [PDF], the National Institute of Standards and Technology (NIST) deprecated SHA-1 in 2011 and banned its usage in the production and verification of digital signatures in 2013, with a few exceptions.
A collision attack occurs when two different messages serve as input but result in the same hash value when processed. Collisions are undesirable for applications such as digital signatures and file checksums because they contradict the security assumptions made about the uniqueness of the data. When a good program and a malicious application have the same hash value, the security of the system is compromised.
By the year 2015, major corporations like as Facebook, Google, Microsoft, and Mozilla had already begun making preparations to break their ties with SHA-1. In 2017, the majority of online browsers finally abandoned support for SHA-1 certificates; nevertheless, it took some time for the rest of the industry to catch up to this development.
In spite of the fact that it is recognized to have flaws, SHA-1 has been used more often in recent years to support outdated programs and to provide subpar password storage. In August of 2020, Microsoft will finally get around to retiring the SHA-1 hashing algorithm from the Windows update process.
SHA-1 is still readily accessible, despite the fact that its usage in current applications is quite low. The NIST Cryptographic Algorithm Validation Program, which evaluates cryptographic algorithms for manufacturers, comprises 2,272 cryptographic modules that have been certified in the previous five years and still support the SHA-1 standard.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
