In recent weeks, the renowned Lazarus gang, which acts as a cyber threat actor, has been more active than usual, exploiting software vulnerabilities in order to gain control of computers. Even if the vulnerabilities themselves were not novel, what is especially worrisome is the fact that some systems remained susceptible despite the fact that fixes were already available for them. Despite the availability of many updates and warnings from the programme provider, the North Korean hacker organisation known as Lazarus was able to regularly hacked a software vendor by exploiting vulnerabilities in susceptible software.
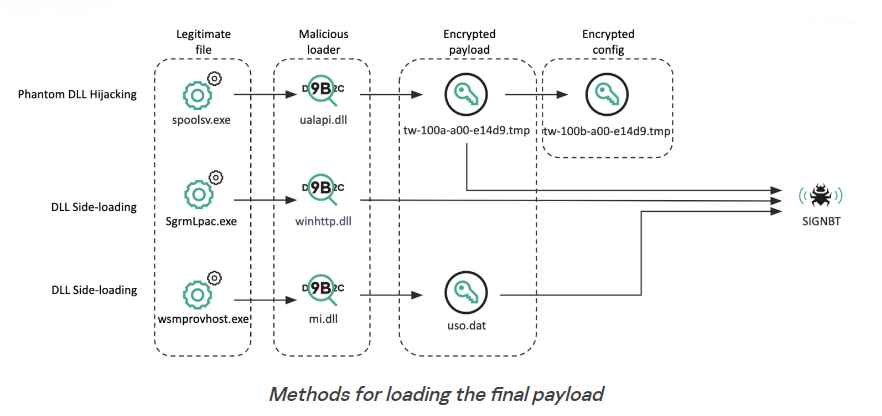
The fact that the same target was infiltrated by Lazarus many times suggests that the hackers were attempting to either steal source code or launch an attack on the supply chain. Surprisingly, this wasn’t the first time that had happened. The security experts at Kaspersky came to the conclusion that this software company had, on several instances in the past, been the target of Lazarus attacks. The repeated intrusions bring to light a persistent threat actor who most likely has the purpose of stealing important source code or disrupting the software supply chain. One concerning finding was the distribution of malware known as SIGNBT, which intended to exert control over its victims. The very complicated loading procedure is one of its distinguishing characteristics. It is believed to have originated from a file known as “ualapi.dll,” and in order to authenticate its victim, it consults a sequence stored in the Windows registry. If the validation is successful, the malicious software will utilise an AES decryption key to decode its payload before beginning its harmful actions. The communication capabilities of the SIGNBT virus set it apart from other similar threats. It employs certain strings, beginning with SIGNBT, which serves as its identifier in this context.
Complexity characterises the communication between the virus and its Command and Control (C2) server. A hard-coded value, an MD5 hash of the victim’s machine name, and a randomly generated identification are all included in the 24-byte value that makes up the C2 transmission. This structure, which is intended to verify and secure communications, consists of a method that is repeated and applied to each and every HTTP communication sequence. The different strings that SIGNBT use for command and control (C2) communications, which it uses to communicate information about the infected system and receive instructions to carry out, are where the malware got its name. It has been observed by Kaspersky that Lazarus utilises that capability on SIGNBT in order to load credential dumping tools as well as the LPEClient malware on infected devices. LPEClient is a self-contained information stealer and malware loader that, according to Kaspersky, in its most recent versions displays remarkable development in comparison to samples that were previously disclosed.
“It now employs advanced techniques to improve its stealth and avoid detection, such as disabling user-mode syscall hooking and restoring system library memory sections,” explains Kaspersky antivirus.
Although it employed the malware in early infection stages to inject other payloads, Kaspersky reports that Lazarus used the LPEClient into subsequent campaigns it performed in 2023.This virus was first discovered in an attack on a defence contractor in the year 2020. It functions mostly in the memory of the machine, which ensures its stealthiness. Recent versions of LPEClient have been improved so that they are less likely to be detected by making changes such as removing user-mode syscall hooking and restoring system library memory regions. These changes are indicative of the group’s intention to increase the effectiveness of their malware.
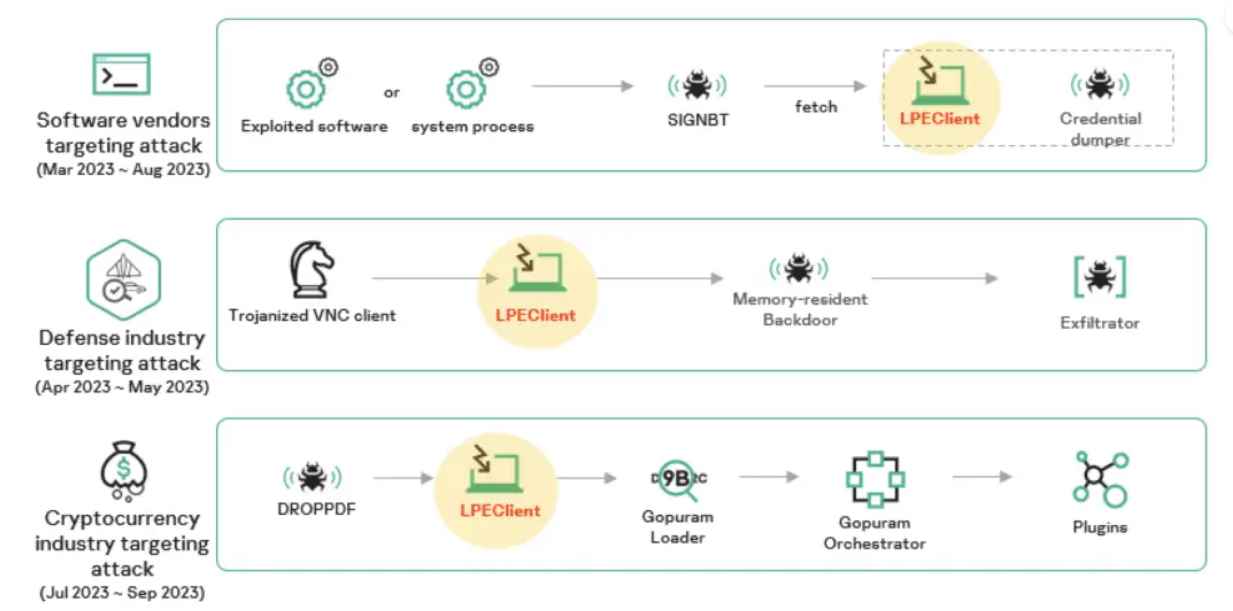
Across all of the Lazarus group’s efforts, the use of the malicious LPEClient software has been constant. LPEClient continues to play a crucial role in the delivery of the final payload, despite the fact that multiple infection vectors and chains were used initially. In the year 2023, this pattern was seen in efforts directed at military contractors, nuclear experts, and those working in the cryptocurrency industry.
The ever-changing strategies used by the Lazarus gang bring to light the significant difficulties faced by cybersecurity specialists in the modern day. Their extensive skills and agility are shown by their diversified clientele, which includes software providers as well as a variety of business sectors. The persistent breaching of the security of the same software provider is evidence of their dogged determination to achieve their goals. Their significant technological talents are shown by the creation of malware such as SIGNBT and LPEClient, as well as by the intricacy of these programmes.
In conclusion, the Lazarus gang is still a strong foe in the digital sphere because to the advanced means and unyielding goals that it employs. In order to tackle sophisticated attacks like these, vigilance, consistent patching, and improved threat detection are more important than they have ever been.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
