Visual Studio Code, more often known by its acronym VSCode, is a source code editor that was created by Microsoft and is available for free. It is a very effective and adaptable coding environment that is capable of supporting a diverse selection of programming languages, frameworks, and tools. VSCode has seen significant growth in popularity over the last several years, and it has emerged as one of the most popular code editors among developers. The VSCode Extensions Marketplace is one of the primary reasons for this, since it offers a central center where developers can find and install new extensions to improve their coding experience. The marketplace offers both official Microsoft extensions as well as extensions built by third parties with contributions from the community.
As at this moment, there are around 50,000 different extensions available on the market. The VSCode extensions are add-ons that may be added in order to improve the editor’s overall capabilities. They may be used to introduce new features, support new programming languages, interface with other tools and services, and a variety of other applications. Users run the danger of having malicious extensions installed on their computers, which might then steal their data or steal their personal information or execute other malicious acts.
Microsoft has implemented a number of security measures for the VSCode Extensions Marketplace in order to prevent the distribution of malicious extensions. These security measures include automatic extension scanning tools in order to detect and remove malicious extensions from the marketplace, as well as user reviews and ratings in order to identify and report malicious extensions. To this day, there have been nearly no harmful extensions that have been released on the VSCode marketplace that can be found.
Open-source code components may be a popular source for infections, particularly the more common ones. Threat actors are always looking for new methods to infect users, and open-source code components can be a common source for infections.
Researchers from Check Point have set out on a quest to identify potentially malicious VSCode extensions in view of the possible threats that might arise from these extensions. Their research uncovered a number of potentially malicious extensions that had over 45,000 installations each; these extensions were immediately reported to the VSCode team and then deleted thereafter.
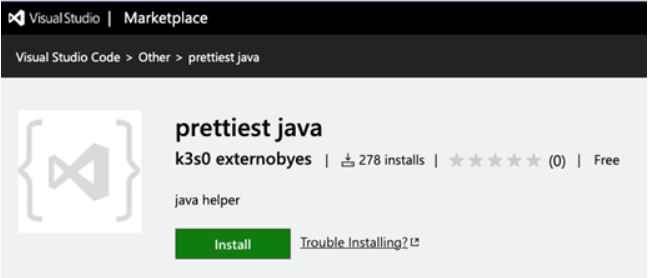
One of the malicious extensions that was discovered was called “prettiest java.” It seemed to be a harmless extension called “java helper,” but it really included traditional PII stealer code. This kind of malware is regularly seen in the PyPI distribution. Another plugin called “Theme Darcula dark” was meant to increase color uniformity but instead it included code that stole personal information (PII). Finally, the malware known as “python-vscode” employed obfuscated lines to inject malicious code onto the computer that the installer was running on. It did this in order to trick people into downloading the malware by giving the impression that its name enabled Python programming in VSCode.
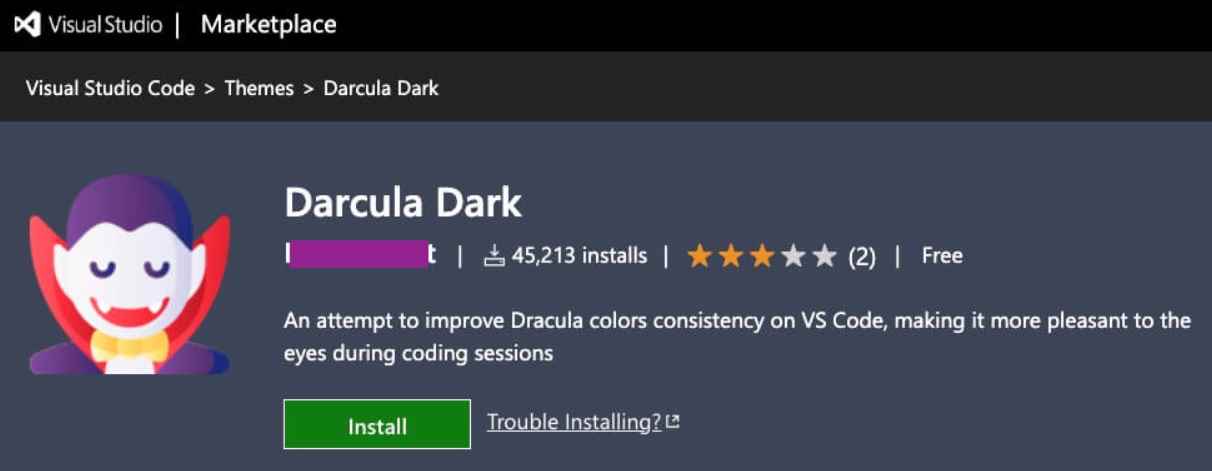
The second extension that should be mentioned is called “Theme Darcula dark,” and according to the description of the extension, it was meant to be “an attempt to improve Dracula colors consistency on VS Code, making it more pleasant to the eyes during coding sessions.” This add-on caught their attention for a couple of different reasons. For one, it had over 45,000 active installations, which indicated that it was highly popular. The second issue is the presence of some harmful code therein. Despite the fact that the extension was just meant to be a straightforward theme configuration (no code was intended to be included), it had a straightforward PII stealer code, which is rather typical of malicious NPM packages. This code sent a great deal of information describing the installation settings to a remote computer. Code that shouldn’t exist, particularly for something that’s supposed to be an editor theme.
These results highlight the urgent need for developers to validate every open-source component rather than presuming the component’s safety, since bad actors continue to discover methods to penetrate even the most renowned platforms. Users are reminded to maintain a high level of vigilance, and developers are encouraged to work toward further enhancing security measures as the VSCode Extension Marketplace continues to grow.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
