Cybersecurity specialists report the discovery of a critical vulnerability in VMware vCenter Server, the management interface for vSphere environments that is being exploited in the wild. The vulnerability, tracked as CVE-2021-21986, has already been fixed, although exploit attempts had already been detected prior to the release of the fixes.
The company specifies that this flaw affects the Virtual SAN Health Check plug-in of the vSphere Client, enabled by default in vCenter Server. Threat actors with access to port 442 can abuse the flaw to execute privileged commands on the operating system that hosts vCenter Server.
Separately, a Chinese researcher known as “iswin” published a proof of concept (PoC) exploit in early June; just hours after a Bad Packets report detected multiple indications of malicious activity linked to CVE-2021-21985. Security researcher Kevin Beaumont also reported that one of his honeypots was hacked by abusing this security flaw.
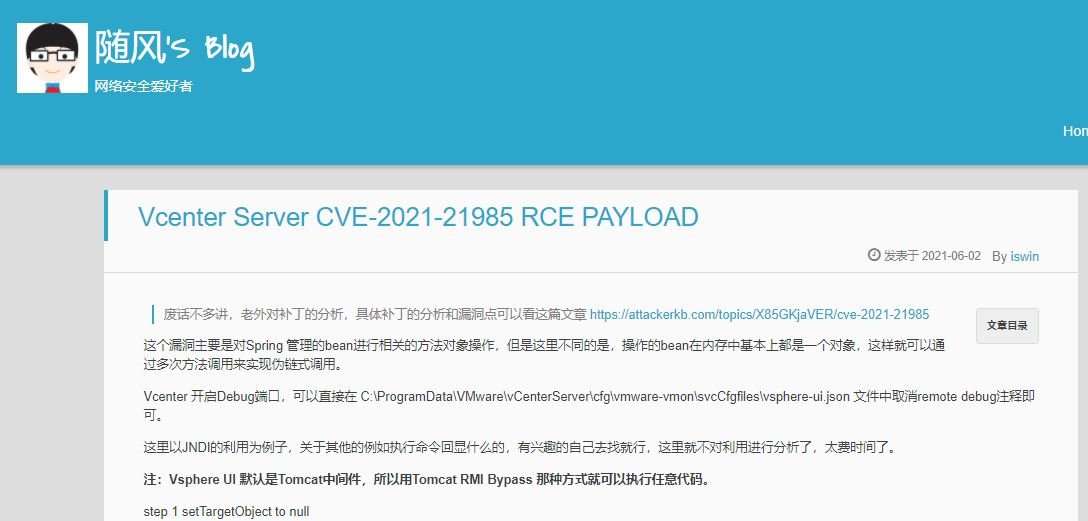
Researcher Nguyen Jang also published a proof of concept, plus some technical details to show the exploitation process. It should be noted that there are thousands of vCenter Server deployments exposed.
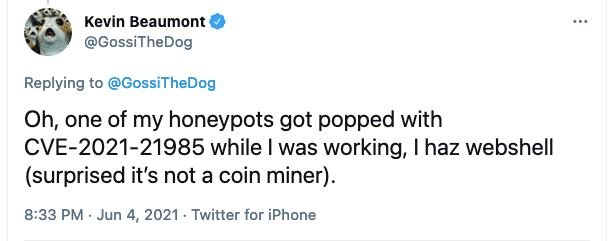
Beaumont warns of the risks of keeping these deployments exposed: “It is best not to connect vCenter directly to the Internet, especially the version preinstalled on the appliance, as it would allow the installation of a backdoor.” The Cybersecurity and Infrastructure Security Agency (CISA) also issued a security alert warning organizations using the affected deployment in order to complete the installation of the corresponding updates.
This isn’t the first time malicious hackers have exploited a vCenter Server vulnerability shortly after it was updated. Earlier this year, scanning of systems affected by CVE-2021-21972 began a day after the fixes were released.
A few days ago, Cisco Talos reported last week that a malware identified as Necro has been exploiting the CVE-2021-21972 flaw since the beginning of May. Necro is a malware designed for denial of service attacks, network traffic exfiltration and cryptojacking.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
