AirAsia Group was victimized by the Daixin ransomware group, which stole the data of over five million customers and staff. Having the largest fleet and most destinations in Malaysia, AirAsia is a multinational low-cost carrier from Malaysia. Databreaches.net claims that Daixin destroyed backups and encrypted a lot of resources. However, because of the disorganized network of AirAsia Group, they didn’t do as much as they would have.

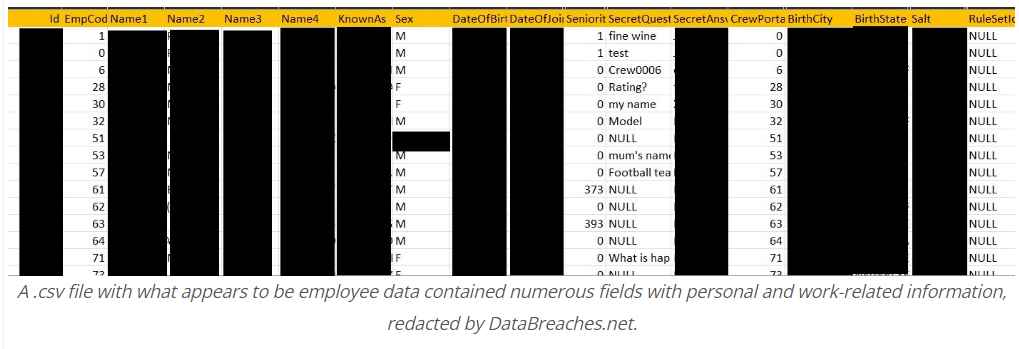
AirAsia Group was the target of a Daixin Team ransomware attack on November 11 and 12. DataBreaches received information from the threat actors, who were the subject of a recent CISA notice, that they had gotten the personal information of 5 million distinct passengers as well as all staff. Two.csv files that Daixin Team also gave to AirAsia Group. Information about identified travelers was included in one file. The second file had information about the employees, including names, dates of birth, nationalities, places of birth, dates of employment beginning, “secret question,” “answer,” and salt.
Daixin uses well-known VPN vulnerabilities and phishing to access the network of their target. Once they have access, they increase their level of authority and utilize RDP and SSH to move laterally within the network of their target. Although the Daixin ransomware group earlier this year targeted the healthcare industry, this most recent breach reveals they are inherently opportunistic. The Daixin Team reportedly uses ransomware to encrypt health data, diagnostic, imaging, and intranet services, according to a joint alert from CISA, the Federal Bureau of Investigation (FBI), and the Department of Health and Human Services.
Babuk Locker source code, which surfaced after the Washington DC Metro Police hack, served as the foundation for the ransomware developed by the Daixin Team.
The spokesman for Daixin said that AirAsia responded to the attack. They apparently soon entered the chat, requested a sample of the data from Daixin’s negotiator, and then “asked in great detail how we would remove their data in case of payment.” According to reports, AirAsia did not attempt to haggle over the price, which might mean they never intended to pay anything. ‘ Typically, everyone wants to agree to a lower price.
One thing that the Daixin spokesman made clear was that the team had avoided locking “XEN, RHEL – hosts of flying equipment (radars, air traffic control, and similar)” while locking files in order to prevent encrypting or deleting anything that would have life-threatening consequences.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
