Cisco confirmed today that the Yanluowang ransomware group breached its corporate network in late May and that the actor tried to extort money from them under the threat of leaking stolen files online. The company revealed that the attackers were only able to collect and steal non-sensitive data from a account linked to a compromised employee’s account.
“Cisco experienced a security incident on our corporate network in late May 2022 and we immediately took action to contain and root out bad actors”. “Cisco did not identify any impacts as a result of this incident, including Cisco products or services, sensitive customer data or sensitive employee information, intellectual property, or supply chain operations. On August 10, the criminals published a list of files from this dark web security incident. We are also implementing additional measures to protect our systems and sharing technical details to help protect the broader security community.”
Stolen employee credentials used to breach Cisco network
Yanluowang threat actors gained access to the Cisco network using an employee’s stolen credentials after hijacking the employee’s personal Google account containing the credentials synced from their browser.
The attacker convinced the Cisco employee to accept multi-factor authentication (MFA) push notifications through MFA fatigue and a series of sophisticated voice phishing attacks initiated by the Yanluowang gang posing as support organizations trustworthy
The threat actors eventually tricked the victim into accepting one of the MFA notifications and gained access to the VPN in the context of the targeted user.
Once they became entrenched in the company’s corporate network, Yanluowang’s operators spread laterally to Citrix servers and domain controllers. “They moved into the Citrix environment, compromising a number of Citrix servers and eventually gaining privileged access to domain controllers, ” Cisco said in a blog post published on Wednesday.
After obtaining the domain administrator, they used enumeration tools such as ntdsutil, adfind and secretsdump to gather more information and installed a number of payloads on the compromised systems, including a backdoor.
Cisco eventually caught them and kicked them out of their environment, but they continued to try to regain access for the next few weeks.
“After gaining initial access, the threat actor performed a variety of activities to maintain access, minimize forensic artifacts, and increase their level of access to systems within the environment,” Cisco Talos added. “The threat actor was successfully removed from the environment and showed persistence, repeatedly attempting to regain access in the weeks following the attack, however these attempts were unsuccessful”.
Hackers claim to have stolen Cisco data
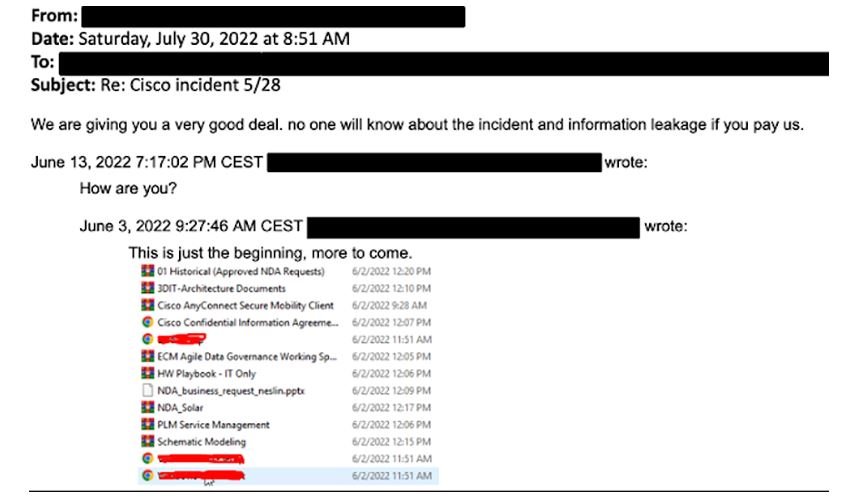
Last week, the threat actor behind the Cisco hack emailed BleepingComputer a list of file directories allegedly stolen during the attack.
The threat actor claimed to have stolen 2.75 GB of data, consisting of approximately 3,100 files. Many of these files are non-disclosure agreements, data dumps, and engineering drawings.
Threat actors also sent a redacted NDA document stolen in the attack as proof of the attack and a “hint” that they breached Cisco’s network and mined files. The extortionists announced the Cisco breach on their data leak site and posted the same directory listing.

No ransomware deployed on Cisco systems
Cisco also said that although the Yanluowang gang is known for encrypting its victims’ files, it found no evidence of ransomware payloads during the attack.
“While we did not observe ransomware deployment in this attack, the TTPs used were consistent with ‘pre-ransomware activity,’ activity commonly observed prior to ransomware deployment in victim environments, Cisco Talos added.
“We assess with moderate to high confidence that this attack was carried out by an adversary previously identified as an initial access broker (IAB) with ties to the UNC2447 cybercrime gang, the LAPSUS$ threat actor group, and operators of Yanluowang ransomware”.
The Yanluowang gang also claimed to have recently breached the systems of US retailer Walmart, which denied the attack, that it found no evidence of a ransomware attack.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
